How Organizations Can Do Their Part and Be CyberSmart Beyond National Cyber Security Awareness Month
October is National Cyber Security Awareness Month (NCSAM), which was created to raise awareness around the importance of cybersecurity and provide organizations with resources to be safer and more secure online. With COVID-19 increasing cybercrime in the remote work environment and targeting the education and healthcare sectors, the lessons of NCSAM are now more important than ever before. Doing business in a widely exposed security environment often proves to be detrimental to the company’s data framework and its reputation in the market — not to forget that even employees find it increasingly hard to explain what really went wrong with their data privacy policies. When a majority of companies are transitioning to digital operations and remote collaboration tools, facing a trove of security challenges in not an uncommon sight. In fact, more than 90% of these companies would agree that their focus now lies on thwarting them from getting entangled amid the global rise in cyber-attacks, which they can do by maintaining a safe and secure flow of data.
But, there’s much more to following and executing a procedural action against security attacks.
We compiled a list of top insights from the industry leaders who evangelize the efforts that are needed to be taken to secure businesses in today’s highly volatile cybersecurity ecosystem.
But first, some quick facts and statistics on how global businesses are performing against perennial cyber threats and data theft attacks and how much they lose every year to such forceful attacks.
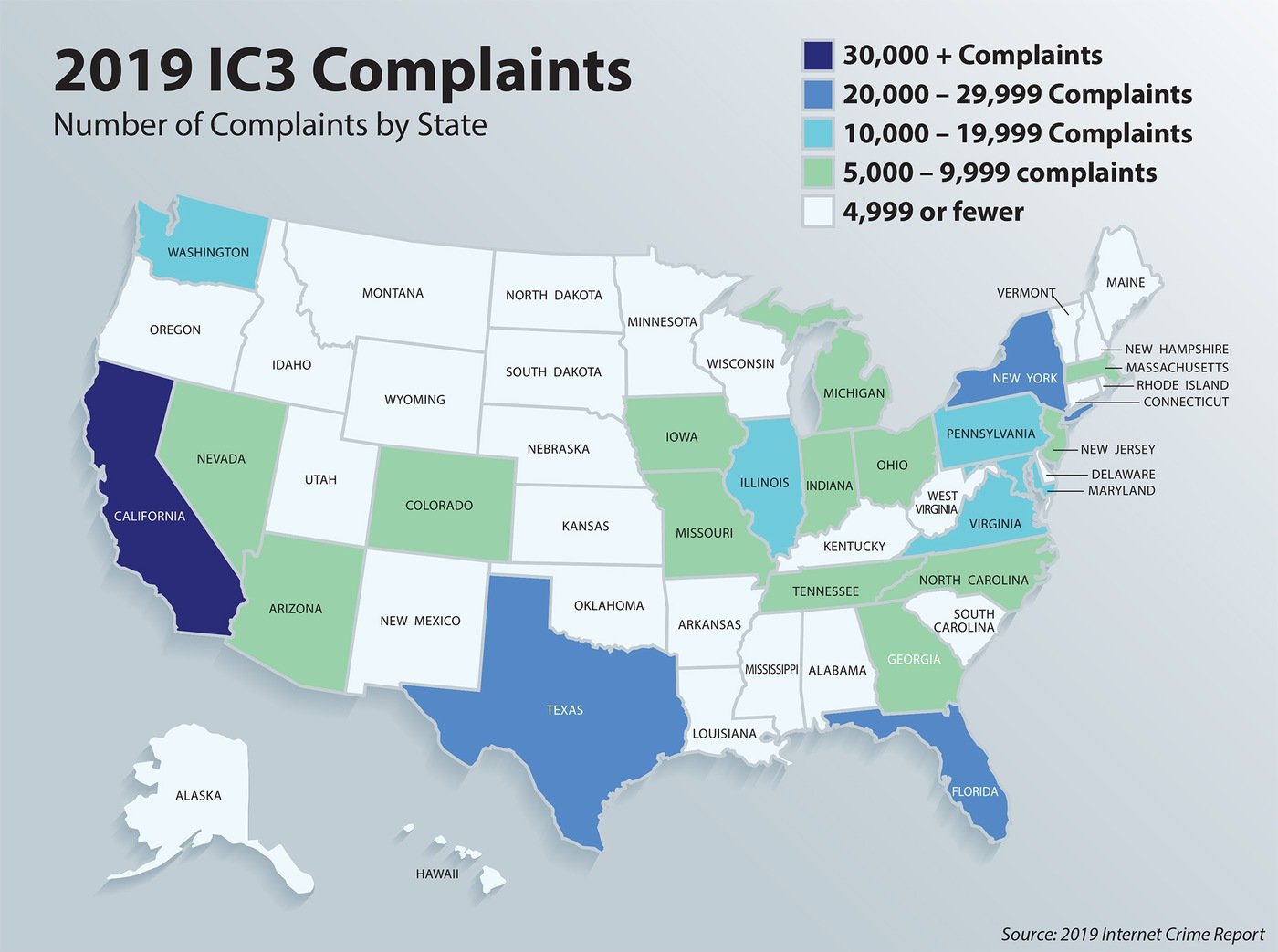
According to a recent study by IBM and the Ponemon Institute, data breaches have an average cost of nearly $4 million globally. Close to 1500 US-targeted attacks were reported in 2019, exposing 164.68 million records.
Below are the worst-hit cybercrime regions in the US in 2019.
According to CSO Magazine by IDG, “60 percent of breaches involved vulnerabilities for which a patch was available but not applied”. Organizations using Action1 can now enforce the same standard procedures and timelines of security patching for remote employees working from home, as well as office-based employees.
In one of the worst data attacks, Facebook had 540 million user records exposed on the Amazon cloud server. ( source: UpGuard) McAfee states that 780,000 records are stolen globally per day. IBM puts this number at an average of 25k+ records per data breach.
What’s even more astonishing is the time by which such attacks are first detected and reported. According to IBM, it takes an average of 279 days to report a data theft or cybercrime in an organization.
Attacks that target software-as-a-service (SaaS) user accounts are one of the fastest-growing and most prevalent problems for organizations, even before COVID-19 forced the vast and rapid shift to remote work. With many organizations increasing their cloud software usage, Microsoft has dominated the productivity space, with more than 250 million active users each month. Office 365 is the foundation of enterprise data sharing, storage, and communication for many of those users, making it an incredibly rich treasure trove for attackers.
This year’s theme is “Do Your Part. #BeCyberSmart.” Below are some reflections from the technology and cybersecurity industry’s leading experts on how organizations can implement the lessons of NCSAM all year long.
“Do Your Part: Be #CyberSmart”

Carl D’Halluin, CTO, Datadobi
“The COVID-19 pandemic and remote work economy have served to exacerbate existing cyber threats such as inside threat actors, ransomware, or a storage platform-specific bug or hack. Downtime caused by these attacks can come at a very high cost for organizations — both financially and reputationally. Unstructured data business continuity planning and protection — whether on-premises or in the cloud — is still lagging dangerously far behind other cybersecurity efforts. Even worse, hackers are increasingly viewing NAS (network-attached storage) as a highly-profitable target. It’s important for IT and security leaders to consider this data when building out security strategies.
“No IT professional wants to imagine the worst-case scenario happening to them: a situation where their NAS or object storage has been locked up by hackers. As organizations increasingly rely on unstructured data to perform day-to-day business-critical functions, they need to maintain instantaneous access to this core data. The best practice would be for organizations to maintain a secure ‘golden copy’ of business-critical data in an air-gapped location of their choosing (a physical bunker site, data center, or public cloud). The golden copy complements the traditional data protection strategy by providing an extra layer of insurance so that in the event of a cyberattack, business operations can continue.”

In a recent press announcement, Chris Morales, head of security analytics at Vectra said, “Within the new work-from-home paradigm, user account takeover in Office 365 is the most effective way for an attacker to move laterally inside an organization’s network. We expect this trend to magnify in the months ahead. Attackers will continue to exploit human behaviors, social engineering, and identity theft to establish a foothold and to steal data in every type of organization.”
Torsten George, Cybersecurity Evangelist, Centrify
“National Cyber Security Awareness Month is an excellent opportunity to remind businesses and consumers alike to never let their guard down when it comes to protecting access to data. All data has some kind of value, whether it’s a PIN code, digital medical records, social security numbers, social media posts, or even blood oxygen levels from your fancy new watch. This year’s theme, ‘Do Your Part: Be #CyberSmart,’ takes on increased significance, as our work and personal lives continue to blur, more devices are connected to the internet than ever, and a historic amount of critical personal and business data is shared digitally.

If there’s one takeaway for businesses, it’s that cyber-attackers no longer ‘hack’ in – they log in using weak, stolen, or phished credentials. This is especially damaging when it comes to privileged credentials, such as those used by IT administrators to access critical infrastructure, which are estimated to be involved in 80% of data breaches.
So how can we reduce this number in October, and as we move into the holiday season and 2021?
Granting ‘least privilege’ is essential to prevent unauthorized access to business-critical systems and sensitive data by both insiders and external threat actors. Striving towards zero-standing privileges and only granting just-enough, just-in-time access to target systems and infrastructure limits lateral movement. As organizations continue their digital transformation journeys, they should look to cloud-ready solutions that can scale with modern business needs. By embedding these key principles into the security stack, the risk of employees’ credentials being compromised and/or abuse can be dramatically reduced, compliance can be strengthened, and the organization can be more secure.”
Paul Cahill, Data Breach Solicitor at Fletchers Data c*****, “Whilst it might seem that BA has had a lucky escape here – with the original notice from the ICO suggesting a fine of £183.9 million – the ICO’s decision is likely to have large companies reviewing their data security arrangements and seeking to strengthen their protection against cyber-attacks.

“The ICO has decided that despite the fact that the data breach was not intentional or deliberate, BA was responsible for the breach of GDPR as a result of its failure to take ‘appropriate steps’ to secure its customers’ personal data. This decision shows that whilst the ICO does accept that the attack on BA’s systems was malicious, there were clear measures that could have been taken to protect customer data from such an attack.
“The decision suggests that companies cannot simply point to their security measures and suggest that they have tried to prevent an attack, but instead need to show that they regularly review and update their procedures, and could not have reasonably been expected to prevent the attack being successful.”
Sam Humphries, Security Strategist, Exabeam
“Anyone who’s ever worked from home knows how distracting it can be. Add the deluge of email communications from colleagues, managers, marketers, schools, the government, etc. and it quickly creates a utopian environment for well-crafted phishing attacks to succeed. Just a momentary lapse in concentration can lead to an employee clicking on something they shouldn’t, and as soon as they have… it’s too late.

We saw in the rapid transition to a remote workforce, security leaders had to quickly find the right balance between ensuring the organization’s productivity needs are met, and keeping the organization secure. Finding this equilibrium continues, and as we maintain a working-from-home structure we cannot afford to be complacent when it comes to cybersecurity.
This National Cybersecurity Awareness Month, it’s time to hit the reset button. Without a doubt, a combination of training, organizational alignment, and technology is the right approach to detecting and stopping security threats. Effective training should help employees understand and buy-in to the importance of cybersecurity, and in the BYOH (Bring your own home) world organizations should broaden awareness efforts to include helping users secure their home environments.
The cyber-threat landscape is becoming increasingly sophisticated and it’s up to us to pick up the pace and arm our security teams with the knowledge and tools required to succeed in building a better cyber defense.”

Alex Vovk, CEO of Action1 Corporation said –
“Many IT security teams were caught off-guard when the world had to suddenly switch to remote work because of COVID lockdowns. Existing on-premise tools, such as WSUS or built-in Windows Update simply stopped working as intended when employees took their laptops home. At the same time, cybercriminals exploiting unpatched systems only intensified their attacks. Organizations using Action1 can take back control and ensure that all users, in all locations, are adequately protected from cyberattacks.”
Steve Moore, Chief Security Strategist, Exabeam

“Organizations have yet to effectively manage the problem of cyberattacks initiated through stolen credentials, especially those which represent compromised internal accounts. This condition continues to plague organizations, and by using existing logins and tools already available on the network, adversaries can move laterally across the company network – as shown the MITRE ATT&CK lateral movement tactic. These combination-type attacks make it harder for a SOC to detect and respond to attackers, allowing adversaries to access private data and high-value assets.
Common organizational countermeasures are mostly ineffective, and most cybersecurity investigation techniques do little to uncover this problem’s occurrence. A point for every audit and compliance professional; when you review the credential entitlement lifecycle process, there must be an equal credential behavior process.
During National Cyber Security Awareness Month, organizations need to recognize how they can get ahead of these bad actors.
First: consider adding capabilities that augment or replace the source of truth in your SOC. Beyond static rules is the ability to identify lateral movement as part of a broader attack chain, tying the supporting events together to a full picture. This is a challenging but relevant use case that should be a capability in any modern SOC.
Second: for whatever is important to you, answer if those series of events are normal or abnormal and build attacker timelines without manual effort. Each of these drastically improves your time to answer. The right analytics will stitch together various log sources into a timeline to show traditional alerts and abnormal behavior. The right behavioral analytics also helps combat insider threats by notifying security teams when the unusual and risky has occurred – both on an individual basis and compared to peers.
Employees outside of the SOC also have a role to play. Over 80 percent of breaches are related to stolen or weak passwords. Thus, security teams must reiterate best password practices such as never using the same password twice, using password vaults, and enabling multi-factor /adaptive authentication. A combination of behavioral analytics and smart password practices can help employees, and their employers stop credential-based attacks during this month and beyond.”
Gijsbert Janssen Van Doorn, Director Technical Marketing, Zerto
“As organizations transitioned into remote working almost overnight, security teams were left to quickly ensure their businesses were secure while trying to fill in the cracks left behind by the introduction of new networks, new devices, and new cyber attacks.

It isn’t a surprise that cybercriminals started taking advantage of this almost immediately, carrying out ransomware attacks throughout the pandemic as businesses did everything they could to remain operational. However, away from the private sector, where healthcare and public sector organizations have been facing huge pressures to manage and control the COVID-19 outbreak, bad actors have posed a significant threat. Keeping healthcare operations running in normal circumstances is absolutely critical, but in the middle of a pandemic, that significance is only magnified.
This year, National Cybersecurity Awareness Month emphasizes personal accountability as well as the importance of taking proactive steps to enhance cybersecurity. Employees, now more than ever, need to remain vigilant in protecting their organization. Ransomware attacks can and will still occur, so cyber-resilience is imperative. With a 72% increase in ransomware attacks during COVID-19, organizations need to be prepared for the inevitable.
Once compromised, it’s too late to take any preventative measures. Organizations need to be able to recover data and get back to operating swiftly and painlessly without paying a ransom.
The key to this is leveraging IT resilience solutions that can quickly and effectively provide recovery after an attack. With the right continuous data protection tools in place, businesses need not worry about paying ransoms and can instead simply recover pre-attack data files within seconds.”
Jay Ryserse, CISSP, VP of Cybersecurity Initiatives at Connectwise
“Cybersecurity is a journey, not a destination. The need to reinforce policy and best practices around cyber hygiene requires continuing education. Whether it’s education for your team or conversations about culture with your customers, you have to consider it’s an ongoing process that requires maintenance. While National Cybersecurity Awareness Month is a great opportunity to discuss the current issues we’re facing and make plans to address them, cybersecurity is critical 365 days a year. Cybercrime doesn’t rest and neither should organizations.
This month also presents a good opportunity to discuss the growing importance of cybersecurity within the managed service provider (MSP) community. When we review the results of a recent survey we conducted with Vanson Bourne, the importance of investing in ongoing cybersecurity education is evident in the data. Ninety-one percent of SMBs say they would consider using or moving to a new IT service provider if it offered the ‘right’ cybersecurity solution. For most, that means having confidence that their provider will be able to respond to cyber-attacks and minimize any damage. If I’m an MSP, I’m going to focus on educating my team on how to deliver the ‘right’ cybersecurity solutions. MSPs owe it to themselves to keep up with trends and knowledge in cybersecurity in order to increase their service offerings and provide their customers with the protection they’re seeking.”
Surya Varanasi, CTO, Storcentric
“As cyber threats continue to raise concerns across virtually all industries, particularly healthcare and financial, it is important that organizations remain compliant and find solutions that implement the latest encrypted technology to protect their data and the data of their customers.
To support business continuity, as well as ensure data protection and security, IT professionals should look for policy-based solutions with the ability to fingerprint and encrypt data to fortify businesses against viruses, ransomware, and other bad actors. Solutions that are able to restore from virtual shortcuts can decrease the amount of time spent retrieving data and help users bring their businesses back up quickly. Implementing self-healing technology can help the system to automatically ensure it is in order and ensure your last line of defense is continuously updated and ready to go. This is an immutable copy that can’t be altered and it is replicated to a remote location using an encrypted transfer. While you can’t eliminate cybercrime, you can take steps to help organizations be prepared to evade and/or recover from it.”
Jeff Hussey, CEO, Tempered

“National Cyber Security Awareness Month is the perfect time to bring awareness to the work that needs to be done to secure our critical infrastructure. Critical infrastructure — from electrical grids, and smart city applications to water treatment plants — have vulnerabilities that pose an enormous cyber risk and in turn, risks to communities. Traditionally, these networks have been physically managed and air-gapped. Managing and securing these networks and remote sites today is difficult, as new technologies are added to legacy systems.
Fortunately, state-of-the-art secure networking solutions are now available that extends secure connectivity across physical, virtual, and cloud platforms and secure every endpoint in your network, with true micro-segmentation and secure remote access. These solutions not only eliminate network-based attacks, but they also reduce the cost and complexity required to effectively manage critical infrastructure for governments, utilities, and IoT applications.”
Trevor Bidle, VP of Information Security and Compliance Officer, US Signal

“When we celebrated National Cyber Security Awareness Month in 2019, no one could have predicted that at that time the following year, the world would be amid a pandemic — and that many companies would be faced with the technological challenges of a newly distributed workforce. Compounding this issue, 64,000 IT professionals are expected to have lost their jobs by the end of 2020, while cybercrime has quadrupled — leaving organizations short-staffed yet increasingly targeted by hackers. The solution for some may be to turn to a third-party SOC that can offload some of the security posture decisions and monitoring.
For years, vulnerability management tools have been reactive rather than proactive — only spotting weak points on the network after they’ve been compromised by a hacker. But the most effective, modern solutions use threat intelligence to proactively identify, classify and prioritize vulnerabilities based on criticality — allowing organizations to catch them before the bad guys do.
Many businesses struggle to set up, scan and effectively analyze vulnerability scan results in a way that drives meaningful action to remedy the issues, however. IT and security departments who want to expand their teams through a third-party SOC can turn to these highly-trained experts to manage vulnerability scanning, report analysis and remediation recommendations. In addition to vulnerability management, organizations can use third-party providers for backup and disaster recovery to help restore data in the face of ransomware attacks and to help build and test effective incident response plans.
While there are additional considerations, these steps are a strong start toward a more secure future, even in these unpredictable times. And it’s important to remember, there’s no shame in asking for help.”
JG Heithcock, General Manager of Retrospect, Inc., a StorCentric Company

“National Cybersecurity Awareness Month serves as a reminder that cybercriminals continue to exploit the pandemic and remote workforce by targeting organizations through phishing, malware distribution, false domain names, and other attacks on teleworking infrastructure.
Preparing for cybercrime attacks through the use of proven techniques will protect your data and critical systems, helping your organization to minimize risks, rapidly recover if necessary, and maintain operations.. This includes updating your system and investing in anti-malware software; protecting your endpoints and not just servers or file-sharing systems; implementing a 3-2-1 backup strategy consisting of: 3 copies of data, 2 different formats and 1 offsite location; routinely monitoring backups to help detect ransomware; and no matter how uncomfortable it might seem, do not pay the ransom in the event of a ransomware attack as this doesn’t guarantee your data will be restored.”
Mr. Andrea Carcano, Co-Founder of Nozomi Networks, a leader in OT and IoT security and visibility said-
“These survey findings echo what we’ve been seeing now for some time with our industrial customers worldwide. IoT devices – and 5G mobility – are becoming key drivers and critical considerations in their digital transformation. And, just like the ERP market was blowing up in the late 90’s primarily on tailwinds from the Y2K event, we believe digital transformation is accelerating 3-5 years on the tailwinds of the COVID-19 pandemic.

It’s encouraging to see that a majority of those polled understand that all these “things” require a change in the state of security for ICS – and to see that they’re pushing for new, more effective solutions for visibility and security of their IoT-enabled infrastructures. Juniper Research predicts there will be 83 Billion IoT connections by 2024 – and 70% are in the Industrial sector.
Traditional on-premises approaches won’t scale — either in terms of being able to add thousands (or more) IoT devices quickly in a single plant facility, production line or mine — or be able to analyze the volume of data that those devices generate. Effective cybersecurity solutions must be able to scale and deploy quickly and endlessly as devices are added – and be able to centrally manage and monitor endless numbers of devices, from multiple locations anywhere in the world.”
Yaniv Bar-Dayan, co-founder and CEO of Vulcan Cyber said –

“Vulnerability management is all about problem-solving, but too often it’s all problems, and not enough solving. So I’m especially thrilled to bring our customers, partners, advisors and staff together to share a vision for what vulnerability management can become through remediation orchestration.
Security and IT leaders understand the risk that poor cyber hygiene creates for their business. The Remediation Summit will provide actionable tools and resources, including the announcement of a new free offering from Vulcan Cyber, to help vulnerability management professionals get fix done.”
How to Manage Cybersecurity Challenges
Changing the existing IT policies that support remote workflows and secure data are top activities in the current ITOps goal-sheets. For now, less than a third of all businesses (30.7%) have changed their IT policy to help employees work within a new operating model and well under half (43.3%) have deployed new communication and productivity tools. In many cases, employees have been left to use their personal devices and applications which has rapidly increased the risk of security vulnerabilities. In fact, only 46.4% have increased their IT security capabilities to keep their organization and employees secure.

As Marilyn Chaplin, Chief Human Resources Officer, NTT Ltd. puts it – “The connected employee – their wellness and employee experience – must be at the heart of the future workplace strategy. Helping people stay connected and keeping their data secure is key to looking after the workforce and maintaining productivity and effectiveness. Yet this must be underpinned by a long-term strategy for digital transformation, with the rollout of new technologies, policies and of course training so employees feel comfortable with new platforms.”
Paul Lipman, CEO of SMB cybersecurity company BullGuard concludes the series by saying – ”
Typically cybersecurity vendors train their ML models using live customer data, “honeypots” designed to attract attackers, and through the sharing of data within the cyber community.
This enables a more comprehensive view of the threat landscape, for example, creating model features that might include a file’s recency, prevalence and frequency of usage across the entire customer universe. Vendors also train their models with corpora of known types of malware as well as legitimate files. The training includes determining if a file is malicious or not, but also often tries to classify the type of malware, which is vital in determining how to remediate or remove the malware.”
(To share your insights on Cybersecurity Awareness Month, please write to us at sghosh@martechseries.com)

chloroquine buy online buy plaquenil online
aralen medicine hydroxychloroquine reviews
plaquenil price https://chloroquine500mg.com/
chloroquine drugs chloroquine hydroxychloroquine
chloroquine phosphate aralen chloroquine
plaquenil cost buy aralen
how does plaquenil work is hydroxychloroquine an immunosuppressant
plaquenil hydroxychloroquine buy hcq
hydroxychloroquine for covid hydroxychloroquine buy
generic chloroquine phosphate cloroquina
plaquenil reviews https://hydrochloroquineada.com/
erectile deficiency http://ivermectinusd.com/# erectile mastery program
is erectile dysfunction secondary to ptsd http://stromectolusdt.com/# erectile photos
zithromax 100 mg https://zithromaxetc.com/
zithromax capsules buy online zithromax
buy cheap zithromax online https://zithromaxdot.com/
zithromax 500 buy generic zithromax
buying zithromax online where can you buy zithromax
provigil 200mg us modafinil 100mg cost buy modafinil 200mg pill
hydroxochlorquine https://keys-chloroquinehydro.com/
order provigil 200mg pills
how Long Until Daily Cialis Is Effective?
how To Take Daily Use Cialis?
how Long Does It Take For Cialis To Work?
order provigil 100mg generic
what Are The Dosage For Cialis?
when Will Generic Cialis Be Available?
how Much Cialis Can You Take Daily?
I was looking at some of your posts on this website and I conceive this site is very instructive! Retain posting.
flomax side effects https://candipharm.com/search?text=flomax+side+effects BreereeAnalo
candipharm kamagra price
I am constantly searching online for ideas that can assist me. Thx!
Hey there are using WordPress for your blog platform? I’m new to the blog world but I’m trying to get started and create my own. Do you require any coding knowledge to make your own blog? Any help would be really appreciated!
Hi would you mind sharing which blog platform you’re working with? I’m going to start my own blog soon but I’m having a difficult time selecting between BlogEngine/Wordpress/B2evolution and Drupal. The reason I ask is because your design and style seems different then most blogs and I’m looking for something completely unique. P.S My apologies for being off-topic but I had to ask!
Hi! Someone in my Myspace group shared this site with us so I came to check it out. I’m definitely enjoying the information. I’m book-marking and will be tweeting this to my followers! Fantastic blog and superb style and design.
Do you mind if I q**** a couple of your articles as long as I provide credit and sources back to your webpage? My website is in the very same niche as yours and my users would definitely benefit from some of the information you present here. Please let me know if this okay with you. Many thanks!
I enjoy what you guys are up too. This type of clever work and exposure! Keep up the wonderful works guys I’ve included you guys to my own blogroll.
Amazing blog! Is your theme custom made or did you download it from somewhere? A theme like yours with a few simple tweeks would really make my blog jump out. Please let me know where you got your theme. Appreciate it
I have to get across my respect for your generosity in support of those people who really want assistance with this important concern. Your real commitment to getting the message all around appeared to be exceptionally advantageous and has always empowered men and women much like me to reach their pursuits. Your new invaluable guideline signifies a lot to me and extremely more to my fellow workers. Thank you; from each one of us.
Hey there would you mind letting me know which web host you’re using? I’ve loaded your blog in 3 different browsers and I must say this blog loads a lot faster then most. Can you recommend a good internet hosting provider at a fair price? Thanks a lot, I appreciate it!
Elups
http://www.hydroxychloroquinex.com/# chloroquine tablets buy online
Howdy! I know this is somewhat off topic but I was wondering if you knew where I could get a captcha plugin for my comment form? I’m using the same blog platform as yours and I’m having problems finding one? Thanks a lot!
Hmm it appears like your blog ate my first comment (it was super long) so I guess I’ll just sum it up what I wrote and say, I’m thoroughly enjoying your blog. I too am an aspiring blog writer but I’m still new to the whole thing. Do you have any recommendations for newbie blog writers? I’d definitely appreciate it.
Appreciating the hard work you put into your blog and in depth information you provide. It’s good to come across a blog every once in a while that isn’t the same old rehashed information. Wonderful read! I’ve bookmarked your site and I’m adding your RSS feeds to my Google account.
Thanks for your personal marvelous posting! I seriously enjoyed reading it, you could be a great author.I will always bookmark your blog and will come back down the road. I want to encourage continue your great job, have a nice evening!
Woah! I’m really digging the template/theme of this blog. It’s simple, yet effective. A lot of times it’s very difficult to get that “perfect balance” between user friendliness and visual appearance. I must say you’ve done a superb job with this. In addition, the blog loads very quick for me on Safari. Exceptional Blog!
Hey there would you mind letting me know which web host you’re working with? I’ve loaded your blog in 3 different browsers and I must say this blog loads a lot faster then most. Can you suggest a good hosting provider at a fair price? Thank you, I appreciate it!
Today, I went to the beach with my kids. I found a sea shell and gave it to my 4 year old daughter and said “You can hear the ocean if you put this to your ear.” She placed the shell to her ear and screamed. There was a hermit crab inside and it pinched her ear. She never wants to go back! LoL I know this is entirely off topic but I had to tell someone!
Hi there just wanted to give you a quick heads up. The words in your post seem to be running off the screen in Firefox. I’m not sure if this is a format issue or something to do with browser compatibility but I figured I’d post to let you know. The layout look great though! Hope you get the issue solved soon. Thanks
Great, thanks for sharing this post. Great.
Greetings! I’ve been reading your site for a while now and finally got the courage to go ahead and give you a shout out from Lubbock Tx! Just wanted to say keep up the good work!
Hi there! This post could not be written any better!Reading through this post reminds me of my previous roommate!He always kept talking about this. I will send this article to him.Fairly certain he’ll have a good read. Thanksfor sharing!
Do you mind if I q**** a few of your articles as long as I provide credit and sources back to your weblog? My blog is in the very same niche as yours and my users would really benefit from a lot of the information you present here. Please let me know if this ok with you. Appreciate it!
Howdy would you mind stating which blog platform you’re using? I’m looking to start my own blog soon but I’m having a hard time choosing between BlogEngine/Wordpress/B2evolution and Drupal. The reason I ask is because your design and style seems different then most blogs and I’m looking for something unique. P.S My apologies for being off-topic but I had to ask!
Hey there just wanted to give you a quick heads up. The words in your content seem to be running off the screen in Internet explorer. I’m not sure if this is a formatting issue or something to do with web browser compatibility but I thought I’d post to let you know. The style and design look great though! Hope you get the issue fixed soon. Thanks
Would you be desirous about exchanging links?
Hey there just wanted to give you a quick heads up. The words in your content seem to be running off the screen in Opera. I’m not sure if this is a format issue or something to do with internet browser compatibility but I thought I’d post to let you know. The design look great though! Hope you get the issue solved soon. Kudos
I’m so happy to read this. This is the kind of manual that needs to be given and not the accidental misinformation that is at the other blogs. Appreciate your sharing this best doc.
It?s arduous to find educated folks on this subject, however you sound like you realize what you?re speaking about! Thanks
Thanks for your article. I would love to comment that the first thing you will need to complete is verify if you really need credit improvement. To do that you will need to get your hands on a replica of your credit rating. That should not be difficult, ever since the government necessitates that you are allowed to receive one absolutely free copy of your credit report on a yearly basis. You just have to check with the right people today. You can either find out from the website with the Federal Trade Commission or contact one of the major credit agencies instantly.
I have seen lots of useful things on your web-site about desktops. However, I have got the impression that notebook computers are still not nearly powerful more than enough to be a wise decision if you generally do jobs that require a lot of power, for example video editing and enhancing. But for website surfing, microsoft word processing, and quite a few other prevalent computer work they are just fine, provided you cannot mind the small screen size. Thanks for sharing your ideas.
Hi there, just became aware of your blog through Google, and found that it’s really informative. I?m going to watch out for brussels. I will appreciate if you continue this in future. Lots of people will be benefited from your writing. Cheers!
I have observed that online diploma is getting well-known because attaining your degree online has become a popular method for many people. Numerous people have never had a chance to attend an established college or university although seek the increased earning potential and a better job that a Bachelor’s Degree affords. Still other individuals might have a qualification in one discipline but want to pursue one thing they now have an interest in.
okmark your weblog and check again here frequently. I’m quite sure I?ll learn plenty of new stuff right here! Best of luck for the next!
Thanks for the sensible critique. Me & my neighbor were just preparing to do some research about this. We got a grab a book from our local library but I think I learned more from this post. I’m very glad to see such wonderful info being shared freely out there.
Incredible! This blog looks just like my old one! It’s on a entirely different topic but it has pretty much the same layout and design. Wonderful choice of colors!
One thing I’d really like to say is before purchasing more laptop memory, look into the machine within which it will be installed. If your machine is actually running Windows XP, for instance, the particular memory ceiling is 3.25GB. Putting in above this would purely constitute a waste. Make certain that one’s motherboard can handle the particular upgrade quantity, as well. Interesting blog post.
Hello there, I found your site via Google at the same time as looking for a similar matter, your web site got here up, it appears great. I have bookmarked it in my google bookmarks.
After examine a couple of of the blog posts on your web site now, and I truly like your approach of blogging. I bookmarked it to my bookmark web site list and will be checking again soon. Pls try my site as well and let me know what you think.
It’s best to participate in a contest for one of the best blogs on the web. I’ll advocate this web site!
Thanks for the helpful post. It is also my opinion that mesothelioma has an extremely long latency time, which means that warning signs of the disease might not emerge right until 30 to 50 years after the original exposure to mesothelioma. Pleural mesothelioma, which can be the most common kind and is affecting the area throughout the lungs, will cause shortness of breath, chest pains, and also a persistent coughing, which may result in coughing up our blood.
whoah this weblog is magnificent i love studying your posts. Stay up the great work! You know, lots of persons are looking round for this info, you can aid them greatly.
This design is wicked! You most certainly know how to keep a reader amused. Between your wit and your videos, I was almost moved to start my own blog (well, almost…HaHa!) Fantastic job. I really enjoyed what you had to say, and more than that, how you presented it. Too cool!
Thanks for your tips about this blog. One thing I would choose to say is purchasing electronic products items from the Internet is not something new. Actually, in the past ten years alone, the market for online electronic products has grown considerably. Today, you can find practically any specific electronic system and other gadgets on the Internet, including cameras in addition to camcorders to computer pieces and game playing consoles.
Hello my loved one! I wish to say that this article is awesome, great written and come with almost all important infos. I would like to look extra posts like this .
Hey There. I discovered your weblog using msn. This is a very smartly written article. Ill make sure to bookmark it and come back to read extra of your useful information. Thank you for the post. I will definitely return.
certainly like your web-site however you have to test the spelling on several of your posts. Several of them are rife with spelling problems and I to find it very bothersome to tell the truth then again I will certainly come again again.
Great post. I was checking constantly this blog and I am inspired! Very useful info specifically the last phase 🙂 I deal with such info much. I was looking for this particular info for a long time. Thank you and good luck.
Greetings from Colorado! I’m bored to death at work so I decided to check out your site on my iphone during lunch break. I enjoy the information you present here and can’t wait to take a look when I get home. I’m surprised at how quick your blog loaded on my mobile .. I’m not even using WIFI, just 3G .. Anyways, very good blog!
Thanks for this article. I’d also like to talk about the fact that it can be hard if you find yourself in school and simply starting out to create a long credit rating. There are many scholars who are just simply trying to survive and have an extended or good credit history can be a difficult issue to have.
I have read some good stuff here. Certainly worth bookmarking for revisiting. I surprise how much effort you put to make such a magnificent informative web site.
Hmm is anyone else experiencing problems with the images on this blog loading? I’m trying to determine if its a problem on my end or if it’s the blog. Any feedback would be greatly appreciated.
meclizinex
Outstanding post however , I was wanting to know if you could write a litte more on this topic? I’d be very thankful if you could elaborate a little bit further. Cheers!
I found your weblog web site on google and check just a few of your early posts. Proceed to keep up the excellent operate. I just extra up your RSS feed to my MSN News Reader. Looking for forward to studying more from you afterward!
I’ve noticed that credit repair activity should be conducted with techniques. If not, you are going to find yourself damaging your standing. In order to realize your aspirations in fixing your credit score you have to always make sure that from this time you pay your entire monthly fees promptly prior to their scheduled date. It is significant because by never accomplishing that area, all other activities that you will decide on to improve your credit standing will not be efficient. Thanks for sharing your tips.
This website won’t render appropriately on my i phone – you may wanna try and fix that
meclizine
As I web-site possessor I believe the content matter here is rattling fantastic , appreciate it for your hard work. You should keep it up forever! Good Luck.
I have been browsing on-line more than three hours lately, but I by no means discovered any fascinating article like yours. Its beautiful worth enough for me. Personally, if all web owners and bloggers made excellent content as you did, the net might be a lot more useful than ever before.
Segera buka aplikasi injector cheat slot maxwin dan kunjungi situs slot terpercaya ini untuk keseruan tak terbatas!
You can certainly see your expertise in the work you write. The world hopes for more passionate writers like you who aren’t afraid to say how they believe. Always follow your heart.
I am no longer certain where you’re getting your info, however good topic. I must spend a while studying much more or figuring out more. Thank you for excellent info I was in search of this information for my mission.
I haven?t checked in here for a while because I thought it was getting boring, but the last few posts are great quality so I guess I will add you back to my everyday bloglist. You deserve it my friend 🙂
Great, Thank you!
Thank you admin!
Thanks for your tips about this blog. Just one thing I wish to say is the fact that purchasing electronics items through the Internet is nothing new. In reality, in the past decades alone, the marketplace for online consumer electronics has grown noticeably. Today, you could find practically any type of electronic tool and tools on the Internet, ranging from cameras plus camcorders to computer elements and video gaming consoles.
meclizine
One thing I’d like to say is car insurance cancellations is a feared experience and if you’re doing the best things as being a driver you won’t get one. Some individuals do obtain the notice that they are officially dropped by their own insurance company they have to scramble to get extra insurance after a cancellation. Low cost auto insurance rates tend to be hard to get after the cancellation. Knowing the main reasons regarding auto insurance cancellation can help people prevent completely losing in one of the most critical privileges available. Thanks for the concepts shared by means of your blog.
Nice post. I learn something more challenging on different blogs everyday. It will all the time be stimulating to learn content from different writers and practice a little bit something from their store. I?d want to use some with the content material on my weblog whether or not you don?t mind. Natually I?ll give you a hyperlink in your internet blog. Thanks for sharing.
I like the helpful info you provide in your articles. I will bookmark your blog and check again here frequently. I’m quite certain I?ll learn plenty of new stuff right here! Best of luck for the next!
Hi! I know this is kind of off topic but I was wondering which blog platform are you using for this website? I’m getting sick and tired of WordPress because I’ve had problems with hackers and I’m looking at alternatives for another platform. I would be fantastic if you could point me in the direction of a good platform.
Howdy would you mind sharing which blog platform you’re working with? I’m going to start my own blog in the near future but I’m having a difficult time deciding between BlogEngine/Wordpress/B2evolution and Drupal. The reason I ask is because your design seems different then most blogs and I’m looking for something unique. P.S Apologies for being off-topic but I had to ask!
Good blog! I truly love how it is easy on my eyes and the data are well written. I am wondering how I could be notified whenever a new post has been made. I have subscribed to your RSS which must do the trick! Have a nice day!
Thanks for the ideas you have provided here. Something else I would like to express is that computer memory needs generally go up along with other innovations in the technology. For instance, whenever new generations of cpus are introduced to the market, there is certainly usually a similar increase in the size demands of both laptop or computer memory as well as hard drive space. This is because the software operated by simply these processor chips will inevitably increase in power to use the new technological know-how.
Thanks for your helpful article. Other thing is that mesothelioma is generally caused by the inhalation of material from mesothelioma, which is a carcinogenic material. It can be commonly noticed among workers in the engineering industry who may have long exposure to asbestos. It’s also caused by moving into asbestos protected buildings for a long period of time, Genetics plays an important role, and some people are more vulnerable for the risk than others.
A powerful share, I just given this onto a colleague who was doing a bit evaluation on this. And he in fact purchased me breakfast because I discovered it for him.. smile. So let me reword that: Thnx for the deal with! But yeah Thnkx for spending the time to discuss this, I really feel strongly about it and love studying more on this topic. If possible, as you develop into expertise, would you mind updating your weblog with extra particulars? It is extremely useful for me. Big thumb up for this weblog post!
Good day! Would you mind if I share your blog with my facebook group? There’s a lot of people that I think would really enjoy your content. Please let me know. Thank you
In my opinion that a home foreclosure can have a significant effect on the applicant’s life. Property foreclosures can have a Several to few years negative relation to a client’s credit report. A new borrower who has applied for a mortgage or any kind of l**** even, knows that the actual worse credit rating can be, the more difficult it is to get a decent mortgage loan. In addition, it could affect any borrower’s capacity to find a good place to lease or rent, if that will become the alternative homes solution. Good blog post.
tadalafil cost in canada http://tadalafilise.cyou/# generic tadalafil from uk
dose of ivermectin for scabies http://isotretinoin20mg.shop/# dose of ivermectin in scabies
I’m not that much of a internet reader to be honest but your blogs really nice, keep it up! I’ll go ahead and bookmark your website to come back later. All the best
stromectol cpr http://meclizine.top/# stromectol cvs
This is really interesting, You’re a very skilled blogger. I’ve joined your rss feed and look forward to seeking more of your fantastic post. Also, I’ve shared your site in my social networks!
stromectol 3mg tablets http://isotretinoin20mg.shop/# stromectol 6 mg tablet
Thanks for giving your ideas. One thing is that learners have a choice between federal student loan and also a private student loan where it can be easier to choose student loan debt consolidation reduction than with the federal education loan.
generic stromectol for humans http://meclizine.top/# how effective is stromectol
topical ivermectin side effects http://isotretinoin20mg.shop/# what is stromectol
naturally like your website but you need to test the spelling on quite a few of your posts. Several of them are rife with spelling problems and I in finding it very bothersome to inform the reality however I will definitely come again again.
stromectol for sale online http://isotretinoin20mg.shop/# stromectol for scabies
stromectol dosage for demodex http://meclizine.top/# stromectol dosage for dogs
You actually make it seem really easy along with your presentation but I in finding this topic to be really something which I feel I would by no means understand. It kind of feels too complicated and extremely broad for me. I am looking forward in your next post, I will try to get the grasp of it!
Thanks for another informative web site. Where else could I get that type of info written in such an ideal way? I’ve a project that I am just now working on, and I’ve been on the look out for such info.
qqspsdya http://para-mayores.es/# hawcargb
Thanks for the ideas you have shared here. Something else I would like to talk about is that pc memory demands generally go up along with other advancements in the know-how. For instance, as soon as new generations of processor chips are introduced to the market, there is certainly usually a related increase in the size and style calls for of both laptop or computer memory along with hard drive space. This is because the program operated simply by these cpus will inevitably increase in power to leverage the new technologies.
Appreciation to my father who shared with me
about this webpage, this web site is truly amazing.
Have you ever thought about creating an e-book or guest authoring on other blogs? I have a blog centered on the same subjects you discuss and would love to have you share some stories/information. I know my viewers would appreciate your work. If you’re even remotely interested, feel free to shoot me an email.
hey there and thank you for your information ? I?ve definitely picked up something new from right here. I did however expertise a few technical issues using this website, since I experienced to reload the website lots of times previous to I could get it to load correctly. I had been wondering if your web host is OK? Not that I’m complaining, but sluggish loading instances times will often affect your placement in google and could damage your high-quality score if advertising and marketing with Adwords. Anyway I?m adding this RSS to my email and can look out for much more of your respective intriguing content. Make sure you update this again soon..
Thanks a lot for the helpful write-up. It is also my belief that mesothelioma cancer has an incredibly long latency phase, which means that indication of the disease may well not emerge till 30 to 50 years after the preliminary exposure to asbestos fiber. Pleural mesothelioma, which can be the most common variety and is affecting the area across the lungs, could cause shortness of breath, torso pains, including a persistent coughing, which may produce coughing up bloodstream.
Wow, fantastic weblog layout! How long have you been running a blog for? you make running a blog look easy. The total look of your site is wonderful, as smartly as the content!
I’ve learned several important things via your post. I will also like to say that there can be situation in which you will have a loan and never need a co-signer such as a Fed Student Aid Loan. But when you are getting that loan through a classic bank or investment company then you need to be made ready to have a cosigner ready to help you. The lenders will certainly base their own decision using a few issues but the biggest will be your credit score. There are some financial institutions that will also look at your work history and come to a decision based on that but in almost all cases it will be based on on your score.
Thanks for your write-up on this blog site. From my experience, occasionally softening upward a photograph could possibly provide the wedding photographer with an amount of an creative flare. Sometimes however, this soft cloud isn’t exactly what you had in your mind and can frequently spoil a normally good snapshot, especially if you consider enlarging that.
Thank you for another fantastic article. Where else could anyone get that kind of info in such a perfect manner of writing? I’ve a presentation next week, and I am on the look for such info.
hey there and thank you for your information ? I?ve definitely picked up something new from right here. I did however expertise several technical points using this web site, since I experienced to reload the site a lot of times previous to I could get it to load correctly. I had been wondering if your web host is OK? Not that I’m complaining, but sluggish loading instances times will often affect your placement in google and can damage your high quality score if ads and marketing with Adwords. Anyway I am adding this RSS to my email and could look out for much more of your respective intriguing content. Ensure that you update this again soon..
What i don’t realize is actually how you’re not really much more well-liked than you may be now. You are very intelligent. You realize therefore considerably relating to this subject, made me personally consider it from a lot of varied angles. Its like women and men aren’t fascinated unless it is one thing to do with Lady gaga! Your own stuffs great. Always maintain it up!
I will immediately grasp your rss as I can’t in finding your email subscription hyperlink or e-newsletter service. Do you have any? Please permit me realize so that I may just subscribe. Thanks.
尼卡西奥公司 III 作弊者
Excellent items from you, man. I have take into account your stuff prior to and you’re simply extremely magnificent. I really like what you have received here, really like what you’re saying and the way in which by which you are saying it. You’re making it enjoyable and you continue to care for to stay it wise. I cant wait to read much more from you. That is really a wonderful site.
My spouse and I stumbled over here coming from a different website and thought I might as well check things out. I like what I see so now i’m following you. Look forward to looking over your web page again.
oral cialis 5mg tadalafilise.cyou/#
Hey there! Someone in my Myspace group shared this website with us so I came to look it over. I’m definitely enjoying the information. I’m book-marking and will be tweeting this to my followers! Wonderful blog and terrific design and style.
how fast cialis work tadalafil soft tabs best place to buy tadalafil online
great issues altogether, you simply gained a brand new reader. What may you suggest about your post that you simply made some days in the past? Any positive?
Hello! Someone in my Facebook group shared this website with us so I came to give it a look. I’m definitely loving the information. I’m book-marking and will be tweeting this to my followers! Great blog and excellent style and design.
cialis generic india cialis pills canada cialis coupon rite aid
Does your blog have a contact page? I’m having a tough time locating it but, I’d like to shoot you an e-mail. I’ve got some creative ideas for your blog you might be interested in hearing. Either way, great website and I look forward to seeing it grow over time.
Hey there! Someone in my Facebook group shared this website with us so I came to look it over. I’m definitely loving the information. I’m bookmarking and will be tweeting this to my followers! Superb blog and great design.
This article is a refreshing change! The author’s unique perspective and thoughtful analysis have made this a truly fascinating read. I’m appreciative for the effort she has put into creating such an educational and provocative piece. Thank you, author, for providing your wisdom and sparking meaningful discussions through your outstanding writing!
10mg vs 20mg cialis when to take cialis 5mg coupons for cialis
excellent post, very informative. I wonder why the other specialists of this sector do not notice this. You should continue your writing. I am sure, you have a great readers’ base already!
cialis 20mg sale cialis in canada online side effects of cialis for daily use
This is the correct blog for anybody who needs to search out out about this topic. You understand a lot its virtually onerous to argue with you (not that I really would want?HaHa). You positively put a new spin on a subject thats been written about for years. Great stuff, just great!
Thanks for your posting. One other thing is the fact individual American states have their very own laws that affect house owners, which makes it very hard for the Congress to come up with the latest set of rules concerning property foreclosure on home owners. The problem is that each state offers own legislation which may have impact in an unfavorable manner in relation to foreclosure insurance policies.
I was wondering if you ever thought of changing the page layout of your website? Its very well written; I love what youve got to say. But maybe you could a little more in the way of content so people could connect with it better. Youve got an awful lot of text for only having one or two images. Maybe you could space it out better?
Hi there, I found your site via Google while searching for a related topic, your website came up, it looks good. I’ve bookmarked it in my google bookmarks.
Hey there, You’ve done an incredible job. I?ll definitely digg it and in my opinion suggest to my friends. I am confident they’ll be benefited from this web site.
you’re in reality a just right webmaster. The web site loading pace is incredible. It kind of feels that you’re doing any distinctive trick. In addition, The contents are masterwork. you’ve performed a wonderful task on this topic!
The fact is that an individual accused in a crime will probably get a half-baked deal, with no skills of a qualified attorney. Therefore, in the event that you or a family member has been charged of committing a criminal activity, do not forget to make contact with certainly one of our Los Angeles county criminal defense attorney experts. Our Staff Our firm exclusively occupy our ranks aided by the best judiciary minds in the neighborhood. All of us of legal workers are particularly proficient in what the law states additionally the bureaucratic procedure that complicates a number of criminal record lawsuits. Our criminal defense attorney are true masters. These legal representatives should never pass personal judgment on a client charged with intense offenses such as for example murder, rape and even child molestation. They need to and to the best of their capability defend a customer which they might actually trust to be blameworthy for the crime by which they truly are charged. Also, they need to put aside personalized viewpoints or viewpoints and represent a customer that is faced with committing atrocious actions. Therefore, becoming a criminal defense lawyer not merely may take labor and true character to defending every single man or woman’s proper rights provided underneath the law. Every instance provides its very own definite groups of problems despite which region of the court room your client rests. Along with all sorts of law you will find advantages and disadvantages, however with criminal law some seem to simply look at cons. Often there is the alternative of a unlawful sentence, a mistrial in a very worthwhile case, or the risks of working with violent villain, primarily his or her i***** and various criminal sourced elements of large revenues. Many legal professionals could concur that there clearly was a long listing of cons, additionally bad feedback that accompany the future, but the majority worthwhile legal professionals be seemingly in a position to see through the extreme words and practices, and tend to be in a position to see the good that is released of doing criminal law. The huge verdicts just that moreover prove your customers innocence towards the subdivision, all of the the cases and clients, in addition to capacity to be cross examining witnesses in the court room nearly every week, usually are thought. If you want to educate yourself on more info on this one subject matter go visit my martial art web site: [url=https://amicuslegalgroup.com/2020/07/31/how-to-prove-the-other-driver-was-on-the-phone-and-caused-my-la-car-accident/[color=#000_url]riverside car accident lawyer in the region of Jurupa Valley California[/color][/url]
Thanks for the helpful posting. It is also my opinion that mesothelioma has an very long latency phase, which means that warning signs of the disease would possibly not emerge right until 30 to 50 years after the initial exposure to asbestos fiber. Pleural mesothelioma, which can be the most common variety and is affecting the area around the lungs, might cause shortness of breath, chest muscles pains, and also a persistent coughing, which may lead to coughing up body.
Mybudgetart.com.au is Australia’s Trusted Online Wall Art Canvas Prints Store. We are selling art online since 2008. We offer 1000+ artwork designs, up-to 50 OFF store-wide, FREE Delivery Australia & New Zealand, and World-wide shipping.
Attractive component of content. I just stumbled upon your weblog and in accession capital to assert that I get actually loved account your weblog posts. Anyway I will be subscribing in your feeds and even I fulfillment you get admission to constantly quickly.
Hi! This is my 1st comment here so I just wanted to give a quick shout out and say I genuinely enjoy reading through your blog posts. Can you recommend any other blogs/websites/forums that cover the same subjects? Thank you!
Hi, Neat post. There is a problem with your web site in internet explorer, would check this? IE still is the market leader and a big portion of people will miss your fantastic writing because of this problem.
whoah this blog is wonderful i love reading your articles. Keep up the great work! You know, many people are looking around for this information, you could help them greatly.
WONDERFUL Post.thanks for share..more wait .. ?
I was curious if you ever considered changing the page layout of your site? Its very well written; I love what youve got to say. But maybe you could a little more in the way of content so people could connect with it better. Youve got an awful lot of text for only having 1 or 2 images. Maybe you could space it out better?
Create an environment of total acceptance and unconditional love between you and your partner
Good post. I learn something more challenging on totally different blogs everyday. It can always be stimulating to read content material from different writers and apply a little something from their store. I?d prefer to make use of some with the content on my weblog whether or not you don?t mind. Natually I?ll give you a hyperlink in your internet blog. Thanks for sharing.
Howdy would you mind letting me know which webhost you’re utilizing? I’ve loaded your blog in 3 different browsers and I must say this blog loads a lot faster then most. Can you suggest a good hosting provider at a honest price? Thanks a lot, I appreciate it!
I would like to thank you for the efforts you have put in writing this site. I’m hoping the same high-grade site post from you in the upcoming also. Actually your creative writing skills has encouraged me to get my own site now. Actually the blogging is spreading its wings rapidly. Your write up is a good example of it.
I’ve discovered a treasure trove of knowledge in your blog. Your unwavering dedication to offering trustworthy information is truly commendable. Each visit leaves me more enlightened, and I deeply appreciate your consistent reliability.
Your blog has quickly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you put into crafting each article. Your dedication to delivering high-quality content is evident, and I look forward to every new post.
Hello There. I discovered your blog the usage of msn. This is an extremely smartly written article. I?ll be sure to bookmark it and return to learn more of your helpful info. Thanks for the post. I will definitely return.
I was recommended this blog by my cousin. I am now not positive whether this submit is written via him as nobody else recognize such unique approximately my difficulty. You’re amazing! Thank you!
Your enthusiasm for the subject matter radiates through every word of this article; it’s contagious! Your commitment to delivering valuable insights is greatly valued, and I eagerly anticipate more of your captivating content. Keep up the exceptional work!
I must applaud your talent for simplifying complex topics. Your ability to convey intricate ideas in such a relatable manner is admirable. You’ve made learning enjoyable and accessible for many, and I deeply appreciate that.
You really make it appear so easy with your presentation however I in finding this matter to be actually something which I feel I would by no means understand. It seems too complex and extremely broad for me. I am taking a look ahead for your subsequent put up, I?ll try to get the grasp of it!
I wanted to take a moment to express my gratitude for the wealth of valuable information you provide in your articles. Your blog has become a go-to resource for me, and I always come away with new knowledge and fresh perspectives. I’m excited to continue learning from your future posts.
I couldn’t agree more with the insightful points you’ve articulated in this article. Your profound knowledge on the subject is evident, and your unique perspective adds an invaluable dimension to the discourse. This is a must-read for anyone interested in this topic.
I’ve found a treasure trove of knowledge in your blog. Your dedication to providing trustworthy information is something to admire. Each visit leaves me more enlightened, and I appreciate your consistent reliability.
This site is a treasure trove of information. I’m constantly learning and growing thanks to your content.
There are definitely a whole lot of particulars like that to take into consideration. That could be a great point to deliver up. I provide the thoughts above as general inspiration but clearly there are questions like the one you bring up where the most important thing will be working in trustworthy good faith. I don?t know if best practices have emerged around things like that, however I am certain that your job is clearly recognized as a good game. Each girls and boys feel the affect of just a second?s pleasure, for the remainder of their lives.
Thanks for the recommendations shared on the blog. One more thing I would like to talk about is that fat reduction is not exactly about going on a celebrity diet and trying to reduce as much weight as you can in a few months. The most effective way to l********** is by consuming it little by little and using some basic recommendations which can assist you to make the most from a attempt to lose fat. You may realize and already be following most of these tips, but reinforcing understanding never damages.
Your blog is a true gem in the vast online world. Your consistent delivery of high-quality content is admirable. Thank you for always going above and beyond in providing valuable insights. Keep up the fantastic work!
Your enthusiasm for the subject matter shines through every word of this article; it’s contagious! Your commitment to delivering valuable insights is greatly valued, and I eagerly anticipate more of your captivating content. Keep up the exceptional work!
This article resonated with me on a personal level. Your ability to emotionally connect with your audience is truly commendable. Your words are not only informative but also heartwarming. Thank you for sharing your insights.
I am continually impressed by your ability to delve into subjects with grace and clarity. Your articles are both informative and enjoyable to read, a rare combination. Your blog is a valuable resource, and I am sincerely grateful for it.
In a world where trustworthy information is more crucial than ever, your dedication to research and the provision of reliable content is truly commendable. Your commitment to accuracy and transparency shines through in every post. Thank you for being a beacon of reliability in the online realm.
This article resonated with me on a personal level. Your ability to emotionally connect with your audience is truly commendable. Your words are not only informative but also heartwarming. Thank you for sharing your insights.
I?m impressed, I must say. Actually not often do I encounter a weblog that?s both educative and entertaining, and let me let you know, you may have hit the nail on the head. Your thought is excellent; the problem is one thing that not sufficient people are talking intelligently about. I am very happy that I stumbled throughout this in my seek for one thing regarding this.
Your enthusiasm for the subject matter shines through every word of this article; it’s contagious! Your commitment to delivering valuable insights is greatly valued, and I eagerly anticipate more of your captivating content. Keep up the exceptional work!
Your blog has rapidly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you invest in crafting each article. Your dedication to delivering high-quality content is apparent, and I eagerly await every new post.
I must applaud your talent for simplifying complex topics. Your ability to convey intricate ideas in such a relatable manner is admirable. You’ve made learning enjoyable and accessible for many, and I deeply appreciate that.
Oh my goodness! an incredible article dude. Thank you Nevertheless I’m experiencing subject with ur rss . Don?t know why Unable to subscribe to it. Is there anybody getting equivalent rss downside? Anyone who knows kindly respond. Thnkx
Your dedication to sharing knowledge is unmistakable, and your writing style is captivating. Your articles are a pleasure to read, and I consistently come away feeling enriched. Thank you for being a dependable source of inspiration and information.
I couldn’t agree more with the insightful points you’ve articulated in this article. Your profound knowledge on the subject is evident, and your unique perspective adds an invaluable dimension to the discourse. This is a must-read for anyone interested in this topic.
I am continually impressed by your ability to delve into subjects with grace and clarity. Your articles are both informative and enjoyable to read, a rare combination. Your blog is a valuable resource, and I am sincerely grateful for it.
Hi my friend! I wish to say that this article is amazing, nice written and include almost all significant infos. I?d like to see more posts like this.
sportbootführerschein binnen und see, sportbootführerschein binnen prüfungsfragen, sportbootführerschein binnen kosten, sportbootführerschein binnen online, sportbootführerschein binnen wo darf ich fahren, sportbootführerschein binnen berlin, sportbootführerschein binnen segel, sportbootführerschein kaufen, sportbootführerschein kaufen erfahrungen, sportbootführerschein kaufen schwarz, sportbootführerschein see kaufen, sportbootführerschein binnen kaufen, sportbootführerschein see kaufen ohne prüfung, bootsführerschein kaufen, bootsführerschein kaufen polen, bootsführerschein kaufen erfahrungen, bootsführerschein online kaufen, bootsführerschein tschechien kaufen. https://sportbootfuhrerscheinkaufen.com/
comprar carta de conduçao preço, comprar carta de condução verdadeira, comprar carta de conduçao, comprar carta de condução lisboa, comprar carta de condução legal, comprar carta de condução, carta de condução comprar, comprar carta de conduçao, comprar carta de condução em portugal, comprar carta, comprar carta de condução portugal, comprar carta de condução online, comprar a carta de condução, carta de condução, comprar carta de carro, imt carta de condução, comprar carta de condução no porto
https://cartadeconducaolegal.com/
comprare una patente, Comprare la patente di guida reale e registrata dal nostro sito Web senza scrivere esami o sostenere il test pratico. tutto ciò di cui abbiamo bisogno sono i tuoi dati e saranno registrati nel sistema entro i prossimi otto giorni. La patente di guida deve seguire la stessa procedura di registrazione di quelle rilasciate nelle autoscuole, l’unica differenza qui è che non dovrai sostenere gli esami, comprare patente b.
https://patentebcomprare.com/
Your blog has rapidly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you invest in crafting each article. Your dedication to delivering high-quality content is apparent, and I eagerly await every new post.
This article is a true game-changer! Your practical tips and well-thought-out suggestions hold incredible value. I’m eagerly anticipating implementing them. Thank you not only for sharing your expertise but also for making it accessible and easy to apply.
I am continually impressed by your ability to delve into subjects with grace and clarity. Your articles are both informative and enjoyable to read, a rare combination. Your blog is a valuable resource, and I am sincerely grateful for it.
This is my first time pay a quick visit at here and i am really happy to read everthing at one place
I have read several good stuff here. Certainly worth bookmarking for revisiting. I surprise how much effort you put to create such a great informative website.
I’m often to running a blog and i actually admire your content. The article has actually peaks my interest. I am going to bookmark your website and keep checking for brand spanking new information.
Your blog is a true gem in the vast expanse of the online world. Your consistent delivery of high-quality content is truly commendable. Thank you for consistently going above and beyond in providing valuable insights. Keep up the fantastic work!
Your passion and dedication to your craft radiate through every article. Your positive energy is infectious, and it’s evident that you genuinely care about your readers’ experience. Your blog brightens my day!
Your blog has rapidly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you invest in crafting each article. Your dedication to delivering high-quality content is apparent, and I eagerly await every new post.
The truth is a person charged in a crime will probably generate a half-baked deal, with no professional services of a reliable attorney. Therefore, in the event that you or a relative has been accused of carrying out a criminal activity, do not waver to get hold of one of our Orange county criminal defense law firm professionals. Our force Our firm exclusive occupy our positions because of the top rated professional minds in the neighborhood. Our team of judiciary specialists are particularly proficient in what the law states together with bureaucratic procedure which complicates a number of criminal occurrences. Our criminal defense attorney are true professional people. These law firms must not pass personal judgment on a customer faced with heinous crimes such as for instance murder, rape and even child molestation. They have to and to the best of their capability defend a customer which they may personally think to be guilty of this crime by which they truly are charged. Once again, they need to put away individual beliefs as well as ideas and protect a customer that’s been faced with committing unspeakable behaviors. Consequently, getting to be a criminal defense lawyer not just usually requires effort however true character to defending every single man or woman’s legal rights awarded beneath the law. Every circumstances shows its very own particular groups of difficulties despite which region of the court room your very own defendant is located. To all types of law you can find pros and cons, however with criminal law more seem to simply look at cons. There’s always the possibility of a unlawful judgment of conviction, a mistrial at a very crucial case, or the dangers of working with rough lawbreaker, specially his or her bread and butter and various criminal resources of large i*****. Many attorneys can agree that there clearly was a long selection of downsides, and also bad suggestions that accompany the profession, but the majority successful law firms appear to be in a position to see after dark harsh words and strategies, and therefore are in a position to start to see the good that comes out of performing criminal law. The huge verdicts just that furthermore prove your clients innocence into the public, the range of the cases and clients, plus the capacity to be cross investigating witnesses in the court room virtually every work day, usually are thought. If you want to comprehend more info on this approach focus come visit our martial arts business: [url=https://amicuslegalgroup.com/2020/11/21/hurt-by-a-distracted-driver-in-california-how-can-i-recover-compensation/[color=#000_url]why you need an attorney for a motorcycle accident around Rancho Cucamonga CA[/color][/url]
I’m really impressed with your writing skills as well as with the layout on your blog. Is this a paid theme or did you modify it yourself? Anyway keep up the nice quality writing, it?s rare to see a nice blog like this one these days..
Your blog is a true gem in the vast expanse of the online world. Your consistent delivery of high-quality content is truly commendable. Thank you for consistently going above and beyond in providing valuable insights. Keep up the fantastic work!
Your dedication to sharing knowledge is unmistakable, and your writing style is captivating. Your articles are a pleasure to read, and I consistently come away feeling enriched. Thank you for being a dependable source of inspiration and information.
Your positivity and enthusiasm are undeniably contagious! This article brightened my day and left me feeling inspired. Thank you for sharing your uplifting message and spreading positivity among your readers.
http://www.factorytapestry.com is a Trusted Online Wall Hanging Tapestry Store. We are selling online art and decor since 2008, our digital business journey started in Australia. We sell 100 made-to-order quality printed soft fabric tapestry which are just too perfect for decor and gifting. We offer Up-to 50 OFF Storewide Sale across all the Wall Hanging Tapestries. We provide Fast Shipping USA, CAN, UK, EUR, AUS, NZ, ASIA and Worldwide Delivery across 100+ countries.
This article is a true game-changer! Your practical tips and well-thought-out suggestions hold incredible value. I’m eagerly anticipating implementing them. Thank you not only for sharing your expertise but also for making it accessible and easy to apply.
Your dedication to sharing knowledge is unmistakable, and your writing style is captivating. Your articles are a pleasure to read, and I consistently come away feeling enriched. Thank you for being a dependable source of inspiration and information.
Your positivity and enthusiasm are truly infectious! This article brightened my day and left me feeling inspired. Thank you for sharing your uplifting message and spreading positivity to your readers.
I am continually impressed by your ability to delve into subjects with grace and clarity. Your articles are both informative and enjoyable to read, a rare combination. Your blog is a valuable resource, and I am sincerely grateful for it.
Your blog has rapidly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you invest in crafting each article. Your dedication to delivering high-quality content is apparent, and I eagerly await every new post.
Your dedication to sharing knowledge is evident, and your writing style is captivating. Your articles are a pleasure to read, and I always come away feeling enriched. Thank you for being a reliable source of inspiration and information.
[url=https://forfreedating.co.uk/]Adult Flirt Finder[/url] is the best option to connect with local singles who are searching for companionship.
Our web-based platform lets you connect with like-minded people whenever you want.
Become a part of our d***** network today and embark on your adventure to finding love with Flirt finder.
I have realized that car insurance organizations know the motors which are at risk of accidents and other risks. Additionally , they know what type of cars are susceptible to higher risk and the higher risk they’ve got the higher the particular premium amount. Understanding the very simple basics with car insurance will allow you to choose the right types of insurance policy that will take care of your wants in case you become involved in any accident. Many thanks for sharing your ideas on your blog.
Hi there, You’ve done an incredible job. I?ll definitely digg it and for my part recommend to my friends. I’m confident they will be benefited from this site.
Your writing style effortlessly draws me in, and I find it nearly impossible to stop reading until I’ve reached the end of your articles. Your ability to make complex subjects engaging is indeed a rare gift. Thank you for sharing your expertise!
I’m continually impressed by your ability to dive deep into subjects with grace and clarity. Your articles are both informative and enjoyable to read, a rare combination. Your blog is a valuable resource, and I’m grateful for it.
Your positivity and enthusiasm are undeniably contagious! This article brightened my day and left me feeling inspired. Thank you for sharing your uplifting message and spreading positivity among your readers.
I’ve discovered a treasure trove of knowledge in your blog. Your unwavering dedication to offering trustworthy information is truly commendable. Each visit leaves me more enlightened, and I deeply appreciate your consistent reliability.
This article resonated with me on a personal level. Your ability to emotionally connect with your audience is truly commendable. Your words are not only informative but also heartwarming. Thank you for sharing your insights.
This d***** platform opens doors to a vibrant online d***** community. Uncover the possibilities of digital r****** and connect with like-minded individuals in a accessible environment.
Establishing a captivating profile on [url=https://freeflir-online.com/]Flirt Finder D***** Site[/url] is a breeze. Upload attractive pictures, craft an intriguing bio, and engage in meaningful conversations. This platform offers a secure and exciting way to find love online. Join Flirt Finder D***** Site today and take the beginning toward a digital r****** adventure.
In a world where trustworthy information is more crucial than ever, your dedication to research and the provision of reliable content is truly commendable. Your commitment to accuracy and transparency shines through in every post. Thank you for being a beacon of reliability in the online realm.
In a world where trustworthy information is more important than ever, your commitment to research and providing reliable content is truly commendable. Your dedication to accuracy and transparency is evident in every post. Thank you for being a beacon of reliability in the online world.
I’ve discovered a treasure trove of knowledge in your blog. Your unwavering dedication to offering trustworthy information is truly commendable. Each visit leaves me more enlightened, and I deeply appreciate your consistent reliability.
I simply wanted to convey how much I’ve gleaned from this article. Your meticulous research and clear explanations make the information accessible to all readers. It’s abundantly clear that you’re committed to providing valuable content.
This article is a true game-changer! Your practical tips and well-thought-out suggestions hold incredible value. I’m eagerly anticipating implementing them. Thank you not only for sharing your expertise but also for making it accessible and easy to apply.
Your blog is a true gem in the vast expanse of the online world. Your consistent delivery of high-quality content is truly commendable. Thank you for consistently going above and beyond in providing valuable insights. Keep up the fantastic work!
Your storytelling prowess is nothing short of extraordinary. Reading this article felt like embarking on an adventure of its own. The vivid descriptions and engaging narrative transported me, and I eagerly await to see where your next story takes us. Thank you for sharing your experiences in such a captivating manner.
I can’t help but be impressed by the way you break down complex concepts into easy-to-digest information. Your writing style is not only informative but also engaging, which makes the learning experience enjoyable and memorable. It’s evident that you have a passion for sharing your knowledge, and I’m grateful for that.
Your blog is a true gem in the vast expanse of the online world. Your consistent delivery of high-quality content is truly commendable. Thank you for consistently going above and beyond in providing valuable insights. Keep up the fantastic work!
I wanted to take a moment to express my gratitude for the wealth of invaluable information you consistently provide in your articles. Your blog has become my go-to resource, and I consistently emerge with new knowledge and fresh perspectives. I’m eagerly looking forward to continuing my learning journey through your future posts.
I’ve discovered a treasure trove of knowledge in your blog. Your unwavering dedication to offering trustworthy information is truly commendable. Each visit leaves me more enlightened, and I deeply appreciate your consistent reliability.
Your positivity and enthusiasm are undeniably contagious! This article brightened my day and left me feeling inspired. Thank you for sharing your uplifting message and spreading positivity among your readers.
Your blog has rapidly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you invest in crafting each article. Your dedication to delivering high-quality content is apparent, and I eagerly await every new post.
Your blog has rapidly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you invest in crafting each article. Your dedication to delivering high-quality content is apparent, and I eagerly await every new post.
I?m impressed, I must say. Really not often do I encounter a weblog that?s both educative and entertaining, and let me let you know, you’ve hit the nail on the head. Your concept is excellent; the issue is one thing that not enough persons are talking intelligently about. I’m very joyful that I stumbled throughout this in my seek for something regarding this.
Your blog is a true gem in the vast online world. Your consistent delivery of high-quality content is admirable. Thank you for always going above and beyond in providing valuable insights. Keep up the fantastic work!
Your writing is a valuable resource for anyone seeking to understand complex topics. I appreciate your dedication to clarity and accuracy.
Your dedication to sharing knowledge is unmistakable, and your writing style is captivating. Your articles are a pleasure to read, and I consistently come away feeling enriched. Thank you for being a dependable source of inspiration and information.
I’ve discovered a treasure trove of knowledge in your blog. Your unwavering dedication to offering trustworthy information is truly commendable. Each visit leaves me more enlightened, and I deeply appreciate your consistent reliability.
This article resonated with me on a personal level. Your ability to connect with your audience emotionally is commendable. Your words are not only informative but also heartwarming. Thank you for sharing your insights.
Your enthusiasm for the subject matter shines through every word of this article; it’s contagious! Your commitment to delivering valuable insights is greatly valued, and I eagerly anticipate more of your captivating content. Keep up the exceptional work!
Your writing style effortlessly draws me in, and I find it nearly impossible to stop reading until I’ve reached the end of your articles. Your ability to make complex subjects engaging is indeed a rare gift. Thank you for sharing your expertise!
I want to express my appreciation for this insightful article. Your unique perspective and well-researched content bring a new depth to the subject matter. It’s clear you’ve put a lot of thought into this, and your ability to convey complex ideas in such a clear and understandable way is truly commendable. Thank you for sharing your knowledge and making learning enjoyable.
I was curious if you ever thought of changing the layout of your blog? Its very well written; I love what youve got to say. But maybe you could a little more in the way of content so people could connect with it better. Youve got an awful lot of text for only having 1 or 2 images. Maybe you could space it out better?
Comprehending Flirt Finders: What Are They?
Flirt finder d***** sites are a specialized niche in the world of online d*****. They cater to individuals who are looking for more than just a casual chat or a straightforward swipe right. These platforms are designed to help people find meaningful connections, whether they’re seeking a serious relationship or a fun r******. The emphasis here is on the art of flirting, building chemistry, and creating sparks between potential partners.
The Allure of Flirt Finders
A Lively Twist on D*****
One of the captivating aspects of [url=https://flklined2s.nl/]flirt finder[/url] is their cheerful approach to d*****. Unlike standard d***** platforms that primarily focus on profiles and images, flirt finders inspire users to partake in flirty conversations and clever banter. This approach creates an exhilarating and flirtatious ambiance, transforming each interaction into what feels like a potential escapade.
A Multifaceted Community
Flirt finder d***** sites frequently boast a diverse user base, simplifying the quest for someone who aligns with your desires. Whether you’re in search of a companion with specific passions or a partner with a certain way of life, these platforms offer an array of potential matches to explore.
Enhanced Communication Tools
Effective communication is essential in any successful relationship. Flirt finder sites provide a variety of tools such as video chats, virtual presents, and interactive games that enable connecting with others. These capabilities go above and beyond simple text messages and aid users in expressing themselves in artistic ways.
Compatibility Matching
Many flirt finder d***** sites utilize sophisticated algorithms to match users in accordance with compatibility factors. These algorithms factor in interests, values, and personality traits, increasing the likelihood of discovering a significant connection.
Crafting an Unforgettable Profile
Your profile is your digital initial impression on a flirt finder site. To stand out, utilize high-quality photos that showcase your personality, and compose a compelling bio that emphasizes your interests and what you’re looking for in a partner. Bear in mind, authenticity is vital.
Etiquette for Flirting
Flirting on these platforms is completely about being charming and polite. Without a doubt, join lighthearted banter and compliment your potential matches, but avoid overstepping boundaries or making anyone appear awkward. Esteem creates the core of any successful interaction.
Site: [url=https://flklined2s.nl/]https://flklined2s.nl/[/url]
Discovering Exciting Capabilities
Utilize the unique features provided by flirt finder sites. Send virtual gifts, participate in icebreaker games, and make use of video chats to become acquainted with your potential matches more effectively. These tools can help you in breaking the ice and creating unforgettable connections.
Why Opt for a Flirt Finder D***** Platform?
Infuse Your Love Journey
If your love life craves an added dose of excitement, flirt finder d***** platforms are the perfect remedy. They offer a rejuvenating respite from the monotony of standard d***** and introduce a feeling of playfulness into the experience.
Discover Kindred Spirits
These platforms attract individuals who mirror your passion for flirting and constructing romantic bonds. This shared mutual ground can lead to more profound and enjoyable interactions.
Enhanced Chances of Success
The emphasis on harmony and profound connections on flirt finder platforms frequently brings about elevated success rates when it comes to finding compatible partners. If you’re truly committed to uncovering love, these platforms might be a life-changer.
Conclusion
Flirt finder d***** sites have revolutionized the way we approach d*****. Their lighthearted style, variety of users, and cutting-edge tools offer a one-of-a-kind and thrilling path to find love or a intense connection.
So, if you’re prepared to take to the next level your d***** life and explore the world of flirting, try out flirt finder d***** sites a try.
Your next thrilling adventure in love could be just a click away.
I simply wanted to convey how much I’ve gleaned from this article. Your meticulous research and clear explanations make the information accessible to all readers. It’s abundantly clear that you’re committed to providing valuable content.
This article resonated with me on a personal level. Your ability to emotionally connect with your audience is truly commendable. Your words are not only informative but also heartwarming. Thank you for sharing your insights.
I want to express my sincere appreciation for this enlightening article. Your unique perspective and well-researched content bring a fresh depth to the subject matter. It’s evident that you’ve invested considerable thought into this, and your ability to convey complex ideas in such a clear and understandable way is truly commendable. Thank you for generously sharing your knowledge and making the learning process enjoyable.
Your positivity and enthusiasm are undeniably contagious! This article brightened my day and left me feeling inspired. Thank you for sharing your uplifting message and spreading positivity among your readers.
Your enthusiasm for the subject matter radiates through every word of this article; it’s contagious! Your commitment to delivering valuable insights is greatly valued, and I eagerly anticipate more of your captivating content. Keep up the exceptional work!
This article is a real game-changer! Your practical tips and well-thought-out suggestions are incredibly valuable. I can’t wait to put them into action. Thank you for not only sharing your expertise but also making it accessible and easy to implement.
Many thanks for sharing these wonderful content. In addition, the optimal travel and also medical insurance program can often eliminate those fears that come with travelling abroad. Your medical crisis can quickly become extremely expensive and that’s guaranteed to quickly set a financial impediment on the family’s finances. Putting in place the suitable travel insurance offer prior to setting off is well worth the time and effort. Thanks a lot
This article is a true game-changer! Your practical tips and well-thought-out suggestions hold incredible value. I’m eagerly anticipating implementing them. Thank you not only for sharing your expertise but also for making it accessible and easy to apply.
Your blog has rapidly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you invest in crafting each article. Your dedication to delivering high-quality content is apparent, and I eagerly await every new post.
http://www.factorytinsigns.com is 100 Trusted Global Metal Vintage Tin Signs Online Shop. We have been selling art and décor online worldwide since 2008, started in Sydney, Australia. 2000+ Tin Beer Signs, Outdoor Metal Wall Art, Business Tin Signs, Vintage Metal Signs to choose from, 100 Premium Quality Artwork, Up-to 40 OFF Sale Store-wide.
I couldn’t agree more with the insightful points you’ve made in this article. Your depth of knowledge on the subject is evident, and your unique perspective adds an invaluable layer to the discussion. This is a must-read for anyone interested in this topic.
I’m truly impressed by the way you effortlessly distill intricate concepts into easily digestible information. Your writing style not only imparts knowledge but also engages the reader, making the learning experience both enjoyable and memorable. Your passion for sharing your expertise is unmistakable, and for that, I am deeply grateful.
I couldn’t agree more with the insightful points you’ve articulated in this article. Your profound knowledge on the subject is evident, and your unique perspective adds an invaluable dimension to the discourse. This is a must-read for anyone interested in this topic.
I simply wanted to convey how much I’ve gleaned from this article. Your meticulous research and clear explanations make the information accessible to all readers. It’s abundantly clear that you’re committed to providing valuable content.
I am continually impressed by your ability to delve into subjects with grace and clarity. Your articles are both informative and enjoyable to read, a rare combination. Your blog is a valuable resource, and I am sincerely grateful for it.
I must applaud your talent for simplifying complex topics. Your ability to convey intricate ideas in such a relatable manner is admirable. You’ve made learning enjoyable and accessible for many, and I deeply appreciate that.
I must applaud your talent for simplifying complex topics. Your ability to convey intricate ideas in such a relatable manner is admirable. You’ve made learning enjoyable and accessible for many, and I deeply appreciate that.
Everything is very open with a clear description of the issues.
It was definitely informative. Your site is very helpful.
Many thanks for sharing!
I believe that avoiding packaged foods could be the first step in order to l**********. They will often taste good, but processed foods have got very little vitamins and minerals, making you take in more just to have enough energy to get over the day. When you are constantly eating these foods, transferring to whole grain products and other complex carbohydrates will help you have more electricity while ingesting less. Interesting blog post.
Прогон сайта с использованием программы “Хрумер” – это способ автоматизированного продвижения ресурса в поисковых системах. Этот софт позволяет оптимизировать сайт с точки зрения SEO, повышая его видимость и рейтинг в выдаче поисковых систем.
Хрумер способен выполнять множество задач, таких как автоматическое размещение комментариев, создание форумных постов, а также генерацию большого количества обратных ссылок. Эти методы могут привести к быстрому увеличению посещаемости сайта, однако их надо использовать осторожно, так как неправильное применение может привести к санкциям со стороны поисковых систем.
[url=https://kwork.ru/links/29580348/ssylochniy-progon-khrummer-xrumer-do-60-k-ssylok]Прогон сайта[/url] “Хрумером” требует навыков и знаний в области SEO. Важно помнить, что качество контента и органичность ссылок играют важную роль в ранжировании. Применение Хрумера должно быть частью комплексной стратегии продвижения, а не единственным методом.
Важно также следить за изменениями в алгоритмах поисковых систем, чтобы адаптировать свою стратегию к новым требованиям. В итоге, прогон сайта “Хрумером” может быть полезным инструментом для SEO, но его использование должно быть осмотрительным и в соответствии с лучшими практиками.
I’d like to express my heartfelt appreciation for this insightful article. Your unique perspective and well-researched content bring a fresh depth to the subject matter. It’s evident that you’ve invested considerable thought into this, and your ability to convey complex ideas in such a clear and understandable way is truly commendable. Thank you for sharing your knowledge so generously and making the learning process enjoyable.
Your positivity and enthusiasm are truly infectious! This article brightened my day and left me feeling inspired. Thank you for sharing your uplifting message and spreading positivity to your readers.
Almanya’nın en iyi medyumu haluk hoca sayesinde sizlerde güven içerisinde çalışmalar yaptırabilirsiniz, 40 yıllık uzmanlık ve tecrübesi ile sizlere en iyi medyumluk hizmeti sunuyoruz.
Howdy very cool web site!! Guy .. Excellent .. Wonderful .. I will bookmark your website and take the feeds also?I am glad to seek out numerous useful information right here within the submit, we need develop extra strategies in this regard, thank you for sharing. . . . . .
http://www.thebudgetart.com is trusted worldwide canvas wall art prints & handmade canvas paintings online store. Thebudgetart.com offers budget price & high quality artwork, up-to 50 OFF, FREE Shipping USA, AUS, NZ & Worldwide Delivery.
I’m continually impressed by your ability to dive deep into subjects with grace and clarity. Your articles are both informative and enjoyable to read, a rare combination. Your blog is a valuable resource, and I’m grateful for it.
Your blog is a true gem in the vast expanse of the online world. Your consistent delivery of high-quality content is truly commendable. Thank you for consistently going above and beyond in providing valuable insights. Keep up the fantastic work!
I wanted to take a moment to express my gratitude for the wealth of invaluable information you consistently provide in your articles. Your blog has become my go-to resource, and I consistently emerge with new knowledge and fresh perspectives. I’m eagerly looking forward to continuing my learning journey through your future posts.
Greetings! I know this is kind of off topic but I was wondering if you knew where I could get a captcha plugin for my comment form? I’m using the same blog platform as yours and I’m having problems finding one? Thanks a lot!
This actually answered my drawback, thank you!
I’m usually to blogging and i really appreciate your content. The article has actually peaks my interest. I’m going to bookmark your website and keep checking for new information.
I do consider all of the ideas you have introduced in your post. They’re really convincing and will certainly work. Nonetheless, the posts are too short for beginners. May just you please extend them a little from next time? Thanks for the post.
I know of the fact that today, more and more people are attracted to video cameras and the field of picture taking. However, being a photographer, you have to first shell out so much time frame deciding the exact model of dslr camera to buy and moving via store to store just so you could possibly buy the cheapest camera of the trademark you have decided to select. But it does not end now there. You also have to think about whether you should buy a digital photographic camera extended w*******. Thx for the good guidelines I received from your website.
I have observed that online education is getting well-known because obtaining your college degree online has developed into popular option for many people. Numerous people have not necessarily had a possible opportunity to attend an established college or university although seek the increased earning potential and career advancement that a Bachelor’s Degree offers. Still people might have a diploma in one training but wish to pursue another thing they now develop an interest in.
Great blog post. Some tips i would like to make contributions about is that pc memory ought to be purchased if the computer can’t cope with anything you do along with it. One can put in two random access memory boards with 1GB each, for example, but not one of 1GB and one with 2GB. One should look for the car maker’s documentation for the PC to make certain what type of memory space is needed.
https://louisyabcd.smblogsites.com/22895091/everything-about-massage-koreatown-los-angeles
https://zander26t9w.mdkblog.com/28140273/the-basic-principles-of-chinese-medicine-bloating
https://waylonk1k81.blog2freedom.com/22866168/top-guidelines-of-healthy-massage-norwalk-ct
Устройство пола – ключевой момент в строительстве. Стяжка пола способствует получить плоскую поверхность для дальнейших работ.
Специалисты выполняют [url=https://styazhka-pola24.ru/]стяжка пола москва[/url] с оглядкой на всех норм и правил. Выравнивание пола делается с использованием современных смесей, которые предоставляют надежное покрытие и стойкость.
Устройство пола даёт возможность создать идеальную основу для разнообразных видов облицовки. В Москве выравнивание пола выполняют квалифицированные мастера.
Hey! I’m at work browsing your blog from my new iphone 3gs! Just wanted to say I love reading through your blog and look forward to all your posts! Keep up the great work!
https://lindseyi260krb3.newsbloger.com/profile
https://mario3vvu0.ampedpages.com/the-fact-about-healthy-massage-los-angeles-that-no-one-is-suggesting-50225045
https://edwardu642byv9.wikijournalist.com/user
https://beau8vsol.signalwiki.com/364693/not_known_facts_about_korean_massage_near_me_now_open
https://bookmarkshq.com/story16970543/getting-my-chinese-medicine-journal-to-work
https://gunner4vv01.fare-blog.com/23003445/the-basic-principles-of-chinese-medicine-journal
https://elliotg9358.bloguerosa.com/22869900/what-does-chinese-medicine-cupping-mean
https://geraldo369irz4.tdlwiki.com/user
https://tyson0ln89.ageeksblog.com/22820205/fascination-about-chinese-medicine-chi
https://dante4hb59.blogdanica.com/22929099/chinese-medicine-cracked-tongue-can-be-fun-for-anyone
https://rylanr9000.blogolize.com/fascination-about-chinese-medicine-course-62122493
https://stewartz222xpg3.wikidirective.com/user
The things i have seen in terms of laptop or computer memory is always that there are requirements such as SDRAM, DDR etc, that must fit in with the features of the motherboard. If the personal computer’s motherboard is rather current while there are no operating-system issues, updating the ram literally usually takes under one hour. It’s one of the easiest laptop upgrade processes one can think about. Thanks for expressing your ideas.
Hello there, just became alert to your blog through Google, and found that it is really informative. I am going to watch out for brussels. I will appreciate if you continue this in future. Many people will be benefited from your writing. Cheers!
https://hectorj2839.blogvivi.com/23170019/little-known-facts-about-chinese-medicine-chicago
https://judah7qh21.p2blogs.com/22864200/rumored-buzz-on-chinese-medicine-certificate
https://collinb59p9.amoblog.com/the-5-second-trick-for-chinese-medicine-cooling-foods-44352807
https://carlo900vrk5.bloggadores.com/profile
https://titus9v123.bloguetechno.com/about-chinese-medicine-cooker-58056076
I haven?t checked in here for a while because I thought it was getting boring, but the last several posts are good quality so I guess I will add you back to my everyday bloglist. You deserve it my friend 🙂
https://cashillht.theblogfairy.com/22843936/a-review-of-massage-koreatown-nyc
Today, while I was at work, my sister stole my iphone and tested to see if it can survive a thirty foot drop, just so she can be a youtube sensation. My iPad is now broken and she has 83 views. I know this is entirely off topic but I had to share it with someone!
Покер – занимательное времяпрепровождение, которое популярно среди поклонников азарта и профессиональных игроков.
[url=https://landgoedcampingwesterwolde.nl/wp-content/pages/1xbet_promo_codes_free_bonus.html]https://landgoedcampingwesterwolde.nl/wp-content/pages/1xbet_promo_codes_free_bonus.html[/url]
[url=https://www.hermitmehr.at/wp-content/plugins/elements/1xbet_promo_codes_free.html]https://www.hermitmehr.at/wp-content/plugins/elements/1xbet_promo_codes_free.html[/url]
[url=https://everest.ro/wp-content/pages/1x_bet_promo_codes_free.html]https://everest.ro/wp-content/pages/1x_bet_promo_codes_free.html[/url]
[url=http://megadownload.net/MDT/pgs/?1xbet_promo_codes_free.html]http://megadownload.net/MDT/pgs/?1xbet_promo_codes_free.html[/url]
[url=http://arx.com.au/cp/pgs/1xbet_promo_codes_free.html]http://arx.com.au/cp/pgs/1xbet_promo_codes_free.html[/url]
Покер подразумевает различные вариации, что делает эту игру разнообразным и интересным. Участники могут бороться в различных форматах и завоевывать призовые.
Партейная игра в карты требует от участников проанализировать положение, стратегии и умения читать соперников. Это увлекательный аспект игры и занимательной для любого уровня игроков.
Покер признается игрой интеллекта и сноровки, и он предоставляет шанс выиграть крупные призы.
https://prussiav492yrj7.blazingblog.com/profile
https://bookmarklinx.com/story15859149/the-2-minute-rule-for-chinese-medicine-breakfast
https://rogerg555gat8.wikissl.com/user
https://brooks3rqnj.blogrelation.com/28400735/a-review-of-massage-koreatown-los-angeles
https://cruzu7429.actoblog.com/23113415/the-basic-principles-of-chinese-medicine-bloating
https://bookmark-nation.com/story15737483/rumored-buzz-on-chinese-medicine-chi
https://anatoleo160vqj8.loginblogin.com/profile
https://rowan3rr89.blogginaway.com/23098594/the-basic-principles-of-chinese-medicine-for-inflammation
https://august4iv09.blogs-service.com/53436138/the-smart-trick-of-chinese-medicine-journal-that-no-one-is-discussing
Some tips i have seen in terms of laptop or computer memory is that there are specifications such as SDRAM, DDR etc, that must fit in with the specifications of the motherboard. If the personal computer’s motherboard is kind of current and there are no operating system issues, upgrading the ram literally usually takes under an hour. It’s one of several easiest computer system upgrade processes one can picture. Thanks for discussing your ideas.
https://7prbookmarks.com/story15867051/korean-massage-bed-options
https://hectorm899w.wssblogs.com/22905482/the-5-second-trick-for-korean-massage-scrub
https://charlieblgot.activosblog.com/22787661/fascination-about-korean-massage-near-me-now-open
Группа «Каспий» родилась в конце 2012 года, в Москве, когда Володя Астапчик собрал вокруг себя группу музыкантов-единомышленников. Уже через полгода, летом 2013 года команда, названная «Каспий», дебютировала на фестивалях «Нашествие» и «Доброфест». Мелодичность, драйв и многослойная лирика текстов помогли группе стремительно завоевать Интернет- и офф-лайн аудиторию.
[url=https://kaspiymusic.ru/]звукорежиссура каспий[/url]
Can I just say what a reduction to seek out somebody who truly is aware of what theyre speaking about on the internet. You undoubtedly know learn how to deliver an issue to mild and make it important. More folks must learn this and understand this facet of the story. I cant believe youre not more common because you definitely have the gift.
https://lorenzobczu00111.p2blogs.com/22718352/the-ultimate-guide-to-chinese-medical-massage
https://carolynj677nib2.blogspothub.com/profile
https://charlie32086.activosblog.com/22840747/little-known-facts-about-chinese-medicine-chicago
Hi would you mind letting me know which hosting company you’re using? I’ve loaded your blog in 3 completely different web browsers and I must say this blog loads a lot faster then most. Can you recommend a good internet hosting provider at a honest price? Many thanks, I appreciate it!
https://jeffm257uvs9.bloggerchest.com/profile
https://august7zayv.newbigblog.com/28292195/everything-about-korean-massage-near-19002
https://dalton9zu15.shotblogs.com/a-simple-key-for-chinese-medicine-cooker-unveiled-36592303
Полусухая стяжка – метод выравнивания полок. Строительство полутвёрдой стяжки способствует создать ровную поверхность для окончательного покрытия.
[url=https://styazhka77.ru/]устройство полусухой стяжки пола[/url] Мы сделаем супер ровную стяжку пола. 7 лет опыта работы От 500 рублей за квадратный метр
Уход за полусухой стяжкой осуществляет систематический мониторинг и устранение неисправностей с применением специализированного оборудования.
Специализированные инструменты для полусухой стяжки позволяет провести монтаж с высокой точностью. Полусухая стяжка полов является отличным решением для обеспечения качественного основания для последующих работ.
Useful information. Lucky me I discovered your website by accident, and I’m surprised why this twist of fate did not took place earlier! I bookmarked it.
https://julius1pt40.review-blogger.com/44948263/what-does-chinese-medicine-certificate-mean
https://titusq7530.look4blog.com/61887886/what-does-chinese-medicine-blood-pressure-mean
https://andersonu2582.blogpostie.com/44843395/5-easy-facts-about-chinese-medicine-basics-described
Great post however , I was wondering if you could write a litte more on this topic? I’d be very thankful if you could elaborate a little bit further. Cheers!
One more thing I would like to convey is that rather than trying to suit all your online degree courses on days that you end work (considering that people are drained when they get home), try to obtain most of your classes on the saturdays and sundays and only a couple of courses in weekdays, even if it means taking some time away from your weekend break. This is beneficial because on the weekends, you will be more rested as well as concentrated upon school work. Thanks a bunch for the different points I have figured out from your blog site.
https://travisn899u.bloggactivo.com/22830436/5-easy-facts-about-korean-massage-bed-described
One thing is that often one of the most typical incentives for utilizing your credit card is a cash-back or even rebate provision. Generally, you’ll receive 1-5 back with various buying. Depending on the credit card, you may get 1 back on most expenditures, and 5 in return on acquisitions made using convenience stores, filling stations, grocery stores and ‘member merchants’.
Абузоустойчивый VPS
Виртуальные серверы VPS/VDS: Путь к Успешному Бизнесу
В мире современных технологий и онлайн-бизнеса важно иметь надежную инфраструктуру для развития проектов и обеспечения безопасности данных. В этой статье мы рассмотрим, почему виртуальные серверы VPS/VDS, предлагаемые по стартовой цене всего 13 рублей, являются ключом к успеху в современном бизнесе
Hi my friend! I want to say that this post is awesome, great written and include almost all significant infos. I would like to peer more posts like this .
Amazing write-up!
Hi, I think your blog might be having browser compatibility issues. When I look at your website in Opera, it looks fine but when opening in Internet Explorer, it has some overlapping. I just wanted to give you a quick heads up! Other then that, terrific blog!
https://medium.com/@AveryLarso17904/дешевый-выделенный-сервер-ubuntu-с-поддержкой-популярных-cms-4d9ba8c7471e
VPS SERVER
Высокоскоростной доступ в Интернет: до 1000 Мбит/с
Скорость подключения к Интернету — еще один важный фактор для успеха вашего проекта. Наши VPS/VDS-серверы, адаптированные как под Windows, так и под Linux, обеспечивают доступ в Интернет со скоростью до 1000 Мбит/с, что гарантирует быструю загрузку веб-страниц и высокую производительность онлайн-приложений на обеих операционных системах.
Hi! I know this is kind of off topic but I was wondering which blog platform are you using for this website? I’m getting sick and tired of WordPress because I’ve had issues with hackers and I’m looking at options for another platform. I would be fantastic if you could point me in the direction of a good platform.
Interesting article. It is quite unfortunate that over the last decade, the travel industry has already been able to to fight t********, SARS, tsunamis, bird flu virus, swine flu, and also the first ever true global economic downturn. Through all this the industry has really proven to be effective, resilient in addition to dynamic, acquiring new solutions to deal with misfortune. There are always fresh problems and possibilities to which the industry must again adapt and answer.
Thank you for the auspicious writeup. It in fact was a amusement account it. Look advanced to far added agreeable from you! By the way, how can we communicate?
Do you mind if I q**** a couple of your articles as long as I provide credit and sources back to your weblog? My blog site is in the exact same area of interest as yours and my visitors would definitely benefit from some of the information you provide here. Please let me know if this ok with you. Many thanks!
I’m in awe of the author’s talent to make complicated concepts understandable to readers of all backgrounds. This article is a testament to his expertise and dedication to providing useful insights. Thank you, author, for creating such an engaging and insightful piece. It has been an unforgettable experience to read!
Hello there, simply became aware of your blog through Google, and located that it’s truly informative. I am gonna be careful for brussels. I?ll be grateful when you proceed this in future. Lots of other folks might be benefited from your writing. Cheers!
Useful post
1хбет — известная букмекерская контора. Заводите профиль на официальном сайте и забирайте бонусные предложения. Поставьте на команду по душе. Получите выгодные коэффициенты.
1xbet официальный сайт
Interesting blog post. A few things i would like to add is that laptop or computer memory has to be purchased if your computer still cannot cope with what you do with it. One can put in two RAM memory boards having 1GB each, as an example, but not one of 1GB and one of 2GB. One should look for the car maker’s documentation for one’s PC to ensure what type of ram is necessary.
Attractive section of content. I just stumbled upon your web site and in accession capital to assert that I get in fact enjoyed account your blog posts. Anyway I will be subscribing to your augment and even I achievement you access consistently fast.
I have learned some important things via your post. I would also like to state that there might be situation where you will apply for a loan and don’t need a co-signer such as a National Student Support Loan. But if you are getting a loan through a regular loan provider then you need to be willing to have a co-signer ready to assist you. The lenders will probably base their very own decision over a few components but the largest will be your credit score. There are some loan merchants that will furthermore look at your work history and choose based on that but in most cases it will be based on on your rating.
I would like to thank you for the efforts you have put in writing this web site. I’m hoping the same high-grade blog post from you in the upcoming as well. In fact your creative writing abilities has encouraged me to get my own blog now. Actually the blogging is spreading its wings rapidly. Your write up is a good example of it.
Интимные спутницы из Москвы готовы подарить вам незабываемые моменты. Эксклюзивное объявление: мне 18 лет, и я готова подарить тебе невероятный минет в машине. Ощути магию настоящего наслаждения! проститутки выезд. Профессиональные куртизанки ждут вашего звонка. Узнайте, что такое настоящее удовлетворение в компании кокеток из столицы.
My brother suggested I might like this web site. He was entirely right. This post truly made my day. You can not imagine just how much time I had spent for this info! Thanks!
Обновление жилья — наша специализация. Реализация строительных работ в сфере жилья. Мы предлагаем модернизацию жилого пространства с гарантированным качеством.
[url=https://remont-kvartir-brovari.kyiv.ua/]https://remont-kvartir-brovari.kyiv.ua/[/url]
Thanks for another informative web site. Where else could I get that type of info written in such a perfect way? I’ve a project that I am just now working on, and I’ve been on the look out for such information.
F*ckin? awesome things here. I am very glad to see your post. Thanks a lot and i’m looking forward to contact you. Will you kindly drop me a e-mail?
I will immediately grab your rss feed as I can’t find your email subscription link or e-newsletter service. Do you have any? Please let me know so that I could subscribe. Thanks.
[url=https://samye-luchshie-prostitutki-moskvy.top]https://samye-luchshie-prostitutki-moskvy.top[/url]
I am often to blogging and i really recognize your content. The article has actually peaks my interest. I’m going to bookmark your website and keep checking for new information.
Another thing is that when searching for a good internet electronics retail outlet, look for web shops that are continuously updated, maintaining up-to-date with the most current products, the most effective deals, as well as helpful information on products. This will ensure you are doing business with a shop that stays ahead of the competition and gives you things to make intelligent, well-informed electronics buying. Thanks for the critical tips I have really learned through the blog.
http://www.bestartdeals.com.au is Australia’s Trusted Online Canvas Prints Art Gallery. We offer 100 percent high quality budget wall art prints online since 2009. Get 30-70 percent OFF store wide sale, Prints starts $20, FREE Delivery Australia, NZ, USA. We do Worldwide Shipping across 50+ Countries.
I couldn’t agree more with the insightful points you’ve articulated in this article. Your profound knowledge on the subject is evident, and your unique perspective adds an invaluable dimension to the discourse. This is a must-read for anyone interested in this topic.
Your writing style effortlessly draws me in, and I find it difficult to stop reading until I reach the end of your articles. Your ability to make complex subjects engaging is a true gift. Thank you for sharing your expertise!
Your positivity and enthusiasm are undeniably contagious! This article brightened my day and left me feeling inspired. Thank you for sharing your uplifting message and spreading positivity among your readers.
I really appreciate the time and effort you put into your blog posts. It’s clear that you’re passionate, and it shows. Timberland Boots
Your writing always hits home, you have a gift for connecting with your readers! I do have some recommendations for you to check out here- Penegra 100mg tablet
Heya i am for the first time here. I came across this board and I find It really useful & it helped me out a lot. I hope to give something back and aid others like you aided me.
Vous avez une manière unique de voir les choses. Merci de nous faire réfléchir.
I couldn’t agree more with the insightful points you’ve articulated in this article. Your profound knowledge on the subject is evident, and your unique perspective adds an invaluable dimension to the discourse. This is a must-read for anyone interested in this topic.
Your passion and dedication to your craft radiate through every article. Your positive energy is infectious, and it’s evident that you genuinely care about your readers’ experience. Your blog brightens my day!
I must applaud your talent for simplifying complex topics. Your ability to convey intricate ideas in such a relatable manner is admirable. You’ve made learning enjoyable and accessible for many, and I deeply appreciate that.
hey there and thank you for your info ? I have definitely picked up something new from right here. I did however expertise a few technical points using this website, since I experienced to reload the site lots of times previous to I could get it to load correctly. I had been wondering if your web host is OK? Not that I’m complaining, but sluggish loading instances times will very frequently affect your placement in google and could damage your high quality score if advertising and marketing with Adwords. Anyway I?m adding this RSS to my email and could look out for much more of your respective fascinating content. Ensure that you update this again very soon..
Your storytelling prowess is nothing short of extraordinary. Reading this article felt like embarking on an adventure of its own. The vivid descriptions and engaging narrative transported me, and I eagerly await to see where your next story takes us. Thank you for sharing your experiences in such a captivating manner.
I’m genuinely impressed by how effortlessly you distill intricate concepts into easily digestible information. Your writing style not only imparts knowledge but also engages the reader, making the learning experience both enjoyable and memorable. Your passion for sharing your expertise shines through, and for that, I’m deeply grateful.
Your storytelling prowess is nothing short of extraordinary. Reading this article felt like embarking on an adventure of its own. The vivid descriptions and engaging narrative transported me, and I eagerly await to see where your next story takes us. Thank you for sharing your experiences in such a captivating manner.
Your enthusiasm for the subject matter radiates through every word of this article; it’s contagious! Your commitment to delivering valuable insights is greatly valued, and I eagerly anticipate more of your captivating content. Keep up the exceptional work!
I must applaud your talent for simplifying complex topics. Your ability to convey intricate ideas in such a relatable manner is admirable. You’ve made learning enjoyable and accessible for many, and I deeply appreciate that.
Useful post
I couldn’t agree more with the insightful points you’ve articulated in this article. Your profound knowledge on the subject is evident, and your unique perspective adds an invaluable dimension to the discourse. This is a must-read for anyone interested in this topic.
What i do not understood is actually how you are not really much more well-liked than you might be right now. You are so intelligent. You realize thus considerably relating to this subject, made me personally consider it from numerous varied angles. Its like women and men aren’t fascinated unless it is one thing to accomplish with Lady gaga! Your own stuffs outstanding. Always maintain it up!
Nice info!
I’m genuinely impressed by how effortlessly you distill intricate concepts into easily digestible information. Your writing style not only imparts knowledge but also engages the reader, making the learning experience both enjoyable and memorable. Your passion for sharing your expertise shines through, and for that, I’m deeply grateful.
I wanted to take a moment to express my gratitude for the wealth of valuable information you provide in your articles. Your blog has become a go-to resource for me, and I always come away with new knowledge and fresh perspectives. I’m excited to continue learning from your future posts.
This article resonated with me on a personal level. Your ability to emotionally connect with your audience is truly commendable. Your words are not only informative but also heartwarming. Thank you for sharing your insights.
I’ve discovered a treasure trove of knowledge in your blog. Your unwavering dedication to offering trustworthy information is truly commendable. Each visit leaves me more enlightened, and I deeply appreciate your consistent reliability.
In a world where trustworthy information is more important than ever, your commitment to research and providing reliable content is truly commendable. Your dedication to accuracy and transparency is evident in every post. Thank you for being a beacon of reliability in the online world.
Hi, Neat post. There is a problem with your web site in internet explorer, would test this? IE still is the market leader and a large portion of people will miss your magnificent writing because of this problem.
I wanted to take a moment to express my gratitude for the wealth of invaluable information you consistently provide in your articles. Your blog has become my go-to resource, and I consistently emerge with new knowledge and fresh perspectives. I’m eagerly looking forward to continuing my learning journey through your future posts.
I’ve discovered a treasure trove of knowledge in your blog. Your unwavering dedication to offering trustworthy information is truly commendable. Each visit leaves me more enlightened, and I deeply appreciate your consistent reliability.
I’m genuinely impressed by how effortlessly you distill intricate concepts into easily digestible information. Your writing style not only imparts knowledge but also engages the reader, making the learning experience both enjoyable and memorable. Your passion for sharing your expertise shines through, and for that, I’m deeply grateful.
I’d like to express my heartfelt appreciation for this insightful article. Your unique perspective and well-researched content bring a fresh depth to the subject matter. It’s evident that you’ve invested considerable thought into this, and your ability to convey complex ideas in such a clear and understandable way is truly commendable. Thank you for sharing your knowledge so generously and making the learning process enjoyable.
Your dedication to sharing knowledge is evident, and your writing style is captivating. Your articles are a pleasure to read, and I always come away feeling enriched. Thank you for being a reliable source of inspiration and information.
I am continually impressed by your ability to delve into subjects with grace and clarity. Your articles are both informative and enjoyable to read, a rare combination. Your blog is a valuable resource, and I am sincerely grateful for it.
Wow, wonderful weblog format! How long have you been blogging for? you make blogging look easy. The full look of your site is great, let alone the content!
I’m genuinely impressed by how effortlessly you distill intricate concepts into easily digestible information. Your writing style not only imparts knowledge but also engages the reader, making the learning experience both enjoyable and memorable. Your passion for sharing your expertise is unmistakable, and for that, I am deeply appreciative.
Your storytelling prowess is nothing short of extraordinary. Reading this article felt like embarking on an adventure of its own. The vivid descriptions and engaging narrative transported me, and I eagerly await to see where your next story takes us. Thank you for sharing your experiences in such a captivating manner.
Оцифровка документов цена за лист — это наше направление. Мы предоставляем услуги сканирования бумаг с использованием технологических инноваций. Сотрудничество с нами — это быстрый способ сделать вашу документацию доступной в электронной форме.
I’ve discovered a treasure trove of knowledge in your blog. Your unwavering dedication to offering trustworthy information is truly commendable. Each visit leaves me more enlightened, and I deeply appreciate your consistent reliability.
Your enthusiasm for the subject matter radiates through every word of this article; it’s contagious! Your commitment to delivering valuable insights is greatly valued, and I eagerly anticipate more of your captivating content. Keep up the exceptional work!
Your dedication to sharing knowledge is unmistakable, and your writing style is captivating. Your articles are a pleasure to read, and I consistently come away feeling enriched. Thank you for being a dependable source of inspiration and information.
юридическая помощь бесплатно для всех вопросов о юридических вопросах|юридическое обслуживание бесплатно на законодательные темы
бесплатная помощь юриста для физических лиц и предприятий по различным вопросам заказывай бесплатную консультацию юриста от знающих специалистов|Получи бесплатное консультирование от квалифицированных юристов по любым проблемам
Получи бесплатную консультацию юриста и реши свои проблемы
бесплатная юридическая консультация по телефону круглосуточно [url=https://www.konsultaciya-yurista-499.ru/]https://www.konsultaciya-yurista-499.ru/[/url].
Your passion and dedication to your craft radiate through every article. Your positive energy is infectious, and it’s evident that you genuinely care about your readers’ experience. Your blog brightens my day!
I wanted to take a moment to express my gratitude for the wealth of valuable information you provide in your articles. Your blog has become a go-to resource for me, and I always come away with new knowledge and fresh perspectives. I’m excited to continue learning from your future posts.
You could certainly see your skills in the work you write. The sector hopes for even more passionate writers like you who are not afraid to mention how they believe. At all times follow your heart.
オンラインカジノ
オンラインカジノとオンラインギャンブルの現代的展開
オンラインカジノの世界は、技術の進歩と共に急速に進化しています。これらのプラットフォームは、従来の実際のカジノの体験をデジタル空間に移し、プレイヤーに新しい形式の娯楽を提供しています。オンラインカジノは、スロットマシン、ポーカー、ブラックジャック、ルーレットなど、さまざまなゲームを提供しており、実際のカジノの興奮を維持しながら、アクセスの容易さと利便性を提供します。
一方で、オンラインギャンブルは、より広範な概念であり、スポーツベッティング、宝くじ、バーチャルスポーツ、そしてオンラインカジノゲームまでを含んでいます。インターネットとモバイルテクノロジーの普及により、オンラインギャンブルは世界中で大きな人気を博しています。オンラインプラットフォームは、伝統的な賭博施設に比べて、より多様なゲーム選択、便利なアクセス、そしてしばしば魅力的なボーナスやプロモーションを提供しています。
安全性と規制
オンラインカジノとオンラインギャンブルの世界では、安全性と規制が非常に重要です。多くの国々では、オンラインギャンブルを規制する法律があり、安全なプレイ環境を確保するためのライセンスシステムを設けています。これにより、不正行為や詐欺からプレイヤーを守るとともに、責任ある賭博の促進が図られています。
技術の進歩
最新のテクノロジーは、オンラインカジノとオンラインギャンブルの体験を一層豊かにしています。例えば、仮想現実(VR)技術の使用は、プレイヤーに没入型のギャンブル体験を提供し、実際のカジノにいるかのような感覚を生み出しています。また、ブロックチェーン技術の導入は、より透明で安全な取引を可能にし、プレイヤーの信頼を高めています。
未来への展望
オンラインカジノとオンラインギャンブルは、今後も技術の進歩とともに進化し続けるでしょう。人工知能(AI)の更なる統合、モバイル技術の発展、さらには新しいゲームの創造により、この分野は引き続き成長し、世界中のプレイヤーに新しい娯楽の形を提供し続けることでしょう。
この記事では、オンラインカジノとオンラインギャンブルの現状、安全性、技術の影響、そして将来の展望に焦点を当てています。この分野は、技術革新によって絶えず変化し続ける魅力的な領域です。
Бесплатная помощь юриста
юридические консультации в москве [url=https://www.lawyer-uslugi.ru]https://www.lawyer-uslugi.ru[/url].
[url=https://besthost.by/virtualhosting/]виртуальный хостинг[/url]
Когда речь заходит о создании своего собственного сайта, выбор хостинга играет огромную роль. Ведь именно хостинг будет определять доступность и быстродействие вашего сайта для пользователей. Если вы находитесь в Беларуси и ищете надежного хостинг-провайдера, то BestHost.BY – это отличный выбор. BestHost.BY – одна из ведущих хостинг-компаний в Беларуси, предоставляющая высококачественные услуги уже на протяжении 15 лет.
I’m continually impressed by your ability to dive deep into subjects with grace and clarity. Your articles are both informative and enjoyable to read, a rare combination. Your blog is a valuable resource, and I’m grateful for it.
Your enthusiasm for the subject matter radiates through every word of this article; it’s contagious! Your commitment to delivering valuable insights is greatly valued, and I eagerly anticipate more of your captivating content. Keep up the exceptional work!
Your writing style effortlessly draws me in, and I find it nearly impossible to stop reading until I’ve reached the end of your articles. Your ability to make complex subjects engaging is indeed a rare gift. Thank you for sharing your expertise!
Your blog has quickly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you put into crafting each article. Your dedication to delivering high-quality content is evident, and I look forward to every new post.
Past performance is no guarantee of future results. If purchasing Wrapped Kadena (wKDA), the price should be similar to KDA as wKDA has the exact same economic characteristics of KDA. As a result, the price of wKDA should track KDA most of the time. Be aware, however, because the market for wKDA is different from KDA, there may be times where the price of wKDA does not converge with KDA. You can lend liquidity to crypto exchanges and platforms using your Kadena holdings for a fixed period of time. Based on the level of demand, liquidity, 24-hour trading volume, KDA price statistics, and the duration you lock away your KDA coins for, you can earn attractive rates of interest. KuCoin currently offers Kadena (KDA) cryptocurrency trading as well as over 300 other popular tokens. It is often the first to offer buying opportunities for new tokens.
http://www.gothicpast.com/myomeka/posters/show/69873
RocketFuel is a global provider of payment solutions via ACH bank transfers, Bitcoin, Stablecoins, and other cryptocurrencies. Internal dynamics within the Ethereum community were also at play this week. Last week, as it became increasingly clear that the merge would be successful, many fans of Ethereum bought into the token based on the belief that the transition boded well for its long-term success. Ethereum developers and boosters love throwing around the term “ultrasound money,” which describes the belief that the token’s value will be able to withstand global war, economic collapse, or other major disasters. Bitcoin has more than doubled this year, while Ether is up about sixfold. Both scaled records last week amid a fervor for digital assets driven by speculative demand and controversial arguments that they can hedge inflation risks.
オンラインカジノとオンラインギャンブルの現代的展開
オンラインカジノの世界は、技術の進歩と共に急速に進化しています。これらのプラットフォームは、従来の実際のカジノの体験をデジタル空間に移し、プレイヤーに新しい形式の娯楽を提供しています。オンラインカジノは、スロットマシン、ポーカー、ブラックジャック、ルーレットなど、さまざまなゲームを提供しており、実際のカジノの興奮を維持しながら、アクセスの容易さと利便性を提供します。
一方で、オンラインギャンブルは、より広範な概念であり、スポーツベッティング、宝くじ、バーチャルスポーツ、そしてオンラインカジノゲームまでを含んでいます。インターネットとモバイルテクノロジーの普及により、オンラインギャンブルは世界中で大きな人気を博しています。オンラインプラットフォームは、伝統的な賭博施設に比べて、より多様なゲーム選択、便利なアクセス、そしてしばしば魅力的なボーナスやプロモーションを提供しています。
安全性と規制
オンラインカジノとオンラインギャンブルの世界では、安全性と規制が非常に重要です。多くの国々では、オンラインギャンブルを規制する法律があり、安全なプレイ環境を確保するためのライセンスシステムを設けています。これにより、不正行為や詐欺からプレイヤーを守るとともに、責任ある賭博の促進が図られています。
技術の進歩
最新のテクノロジーは、オンラインカジノとオンラインギャンブルの体験を一層豊かにしています。例えば、仮想現実(VR)技術の使用は、プレイヤーに没入型のギャンブル体験を提供し、実際のカジノにいるかのような感覚を生み出しています。また、ブロックチェーン技術の導入は、より透明で安全な取引を可能にし、プレイヤーの信頼を高めています。
未来への展望
オンラインカジノとオンラインギャンブルは、今後も技術の進歩とともに進化し続けるでしょう。人工知能(AI)の更なる統合、モバイル技術の発展、さらには新しいゲームの創造により、この分野は引き続き成長し、世界中のプレイヤーに新しい娯楽の形を提供し続けることでしょう。
この記事では、オンラインカジノとオンラインギャンブルの現状、安全性、技術の影響、そして将来の展望に焦点を当てています。この分野は、技術革新によって絶えず変化し続ける魅力的な領域です。
[url=https://afishkasochi.ru]1xbet зеркало рабочее на сегодня прямо[/url] – это популярная букмекерская компания, предлагающая широкий выбор ставок на спорт, казино и многое другое. С высокими коэффициентами и удобным интерфейсом, 1xbet привлекает множество игроков. Он также предоставляет возможность онлайн-трансляций событий. 1xbet создает захватывающий игровой опыт для своих пользователей.
Your positivity and enthusiasm are truly infectious! This article brightened my day and left me feeling inspired. Thank you for sharing your uplifting message and spreading positivity to your readers.
[url=https://30palomnik.ru]зеркало 1хбет[/url] – это популярная букмекерская компания, предлагающая широкий выбор ставок на спорт, казино и многое другое. С высокими коэффициентами и удобным интерфейсом, 1xbet привлекает множество игроков. Он также предоставляет возможность онлайн-трансляций событий. 1xbet создает захватывающий игровой опыт для своих пользователей.
I want to express my sincere appreciation for this enlightening article. Your unique perspective and well-researched content bring a fresh depth to the subject matter. It’s evident that you’ve invested considerable thought into this, and your ability to convey complex ideas in such a clear and understandable way is truly commendable. Thank you for generously sharing your knowledge and making the learning process enjoyable.
I must commend your talent for simplifying complex topics. Your ability to convey intricate ideas in such a relatable way is admirable. You’ve made learning enjoyable and accessible for many, and I appreciate that.
Your unique approach to tackling challenging subjects is a breath of fresh air. Your articles stand out with their clarity and grace, making them a joy to read. Your blog is now my go-to for insightful content.
I wanted to take a moment to express my gratitude for the wealth of valuable information you provide in your articles. Your blog has become a go-to resource for me, and I always come away with new knowledge and fresh perspectives. I’m excited to continue learning from your future posts.
виртуальный выделенный сервер vps
Абузоустойчивый сервер для работы с Хрумером, GSA и всевозможными скриптами!
Есть дополнительная системах скидок, читайте описание в разделе оплата
Высокоскоростной Интернет: До 1000 Мбит/с
Скорость интернет-соединения играет решающую роль в успешной работе вашего проекта. Наши VPS/VDS серверы, поддерживающие Windows и Linux, обеспечивают доступ к интернету со скоростью до 1000 Мбит/с. Это гарантирует быструю загрузку веб-страниц и высокую производительность онлайн-приложений на обеих операционных системах.
Итак, при выборе виртуального выделенного сервера VPS, обеспечьте своему проекту надежность, высокую производительность и защиту от DDoS. Получите доступ к качественной инфраструктуре с поддержкой Windows и Linux уже от 13 рублей
Аренда мощного дедика (VPS): Абузоустойчивость, Эффективность, Надежность и Защита от DDoS от 13 рублей
Выбор виртуального сервера – это важный этап в создании успешной инфраструктуры для вашего проекта. Наши VPS серверы предоставляют аренду как под операционные системы Windows, так и Linux, с доступом к накопителям SSD eMLC. Эти накопители гарантируют высокую производительность и надежность, обеспечивая бесперебойную работу ваших приложений независимо от выбранной операционной системы.
I have not checked in here for a while as I thought it was getting boring, but the last several posts are good quality so I guess I will add you back to my daily bloglist. You deserve it my friend 🙂
Your dedication to sharing knowledge is unmistakable, and your writing style is captivating. Your articles are a pleasure to read, and I consistently come away feeling enriched. Thank you for being a dependable source of inspiration and information.
Your dedication to sharing knowledge is unmistakable, and your writing style is captivating. Your articles are a pleasure to read, and I consistently come away feeling enriched. Thank you for being a dependable source of inspiration and information.
Pretty section of content. I just stumbled upon your blog and in accession capital to assert that I acquire actually enjoyed account your blog posts. Any way I will be subscribing to your feeds and even I achievement you access consistently fast.
Your positivity and enthusiasm are truly infectious! This article brightened my day and left me feeling inspired. Thank you for sharing your uplifting message and spreading positivity to your readers.
Your passion and dedication to your craft radiate through every article. Your positive energy is infectious, and it’s evident that you genuinely care about your readers’ experience. Your blog brightens my day!
My brother recommended I might like this blog. He was totally right. This post truly made my day. You can not imagine just how much time I had spent for this info! Thanks!
Абузоустойчивый сервер для работы с Хрумером, GSA и всевозможными скриптами!
Есть дополнительная системах скидок, читайте описание в разделе оплата
Виртуальные сервера (VPS/VDS) и Дедик Сервер: Оптимальное Решение для Вашего Проекта
В мире современных вычислений виртуальные сервера (VPS/VDS) и дедик сервера становятся ключевыми элементами успешного бизнеса и онлайн-проектов. Выбор оптимальной операционной системы и типа сервера являются решающими шагами в создании надежной и эффективной инфраструктуры. Наши VPS/VDS серверы Windows и Linux, доступные от 13 рублей, а также дедик серверы, предлагают целый ряд преимуществ, делая их неотъемлемыми инструментами для развития вашего проекта.
I’m genuinely impressed by how effortlessly you distill intricate concepts into easily digestible information. Your writing style not only imparts knowledge but also engages the reader, making the learning experience both enjoyable and memorable. Your passion for sharing your expertise shines through, and for that, I’m deeply grateful.
Your dedication to sharing knowledge is unmistakable, and your writing style is captivating. Your articles are a pleasure to read, and I consistently come away feeling enriched. Thank you for being a dependable source of inspiration and information.
Your writing style effortlessly draws me in, and I find it nearly impossible to stop reading until I’ve reached the end of your articles. Your ability to make complex subjects engaging is indeed a rare gift. Thank you for sharing your expertise!
Your writing style effortlessly draws me in, and I find it nearly impossible to stop reading until I’ve reached the end of your articles. Your ability to make complex subjects engaging is indeed a rare gift. Thank you for sharing your expertise!
Your unique approach to addressing challenging subjects is like a breath of fresh air. Your articles stand out with their clarity and grace, making them a pure joy to read. Your blog has now become my go-to source for insightful content.
Your unique approach to addressing challenging subjects is like a breath of fresh air. Your articles stand out with their clarity and grace, making them a pure joy to read. Your blog has now become my go-to source for insightful content.
Your passion and dedication to your craft radiate through every article. Your positive energy is infectious, and it’s evident that you genuinely care about your readers’ experience. Your blog brightens my day!
Your storytelling prowess is nothing short of extraordinary. Reading this article felt like embarking on an adventure of its own. The vivid descriptions and engaging narrative transported me, and I eagerly await to see where your next story takes us. Thank you for sharing your experiences in such a captivating manner.
Your blog has rapidly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you invest in crafting each article. Your dedication to delivering high-quality content is apparent, and I eagerly await every new post.
Your dedication to sharing knowledge is evident, and your writing style is captivating. Your articles are a pleasure to read, and I always come away feeling enriched. Thank you for being a reliable source of inspiration and information.
This article resonated with me on a personal level. Your ability to emotionally connect with your audience is truly commendable. Your words are not only informative but also heartwarming. Thank you for sharing your insights.
I’m genuinely impressed by how effortlessly you distill intricate concepts into easily digestible information. Your writing style not only imparts knowledge but also engages the reader, making the learning experience both enjoyable and memorable. Your passion for sharing your expertise shines through, and for that, I’m deeply grateful.
Your blog has quickly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you put into crafting each article. Your dedication to delivering high-quality content is evident, and I look forward to every new post.
I couldn’t agree more with the insightful points you’ve made in this article. Your depth of knowledge on the subject is evident, and your unique perspective adds an invaluable layer to the discussion. This is a must-read for anyone interested in this topic.
посоветуйте vps
осоветуйте vps
Абузоустойчивый сервер для работы с Хрумером и GSA и различными скриптами!
Есть дополнительная системах скидок, читайте описание в разделе оплата
Виртуальные сервера VPS/VDS и Дедик Сервер: Оптимальное Решение для Вашего Проекта
В мире современных вычислений виртуальные сервера VPS/VDS и дедик сервера становятся ключевыми элементами успешного бизнеса и онлайн-проектов. Выбор оптимальной операционной системы и типа сервера являются решающими шагами в создании надежной и эффективной инфраструктуры. Наши VPS/VDS серверы Windows и Linux, доступные от 13 рублей, а также дедик серверы, предлагают целый ряд преимуществ, делая их неотъемлемыми инструментами для развития вашего проекта.
Your storytelling prowess is nothing short of extraordinary. Reading this article felt like embarking on an adventure of its own. The vivid descriptions and engaging narrative transported me, and I eagerly await to see where your next story takes us. Thank you for sharing your experiences in such a captivating manner.
I’d like to express my heartfelt appreciation for this enlightening article. Your distinct perspective and meticulously researched content bring a fresh depth to the subject matter. It’s evident that you’ve invested a great deal of thought into this, and your ability to articulate complex ideas in such a clear and comprehensible manner is truly commendable. Thank you for generously sharing your knowledge and making the process of learning so enjoyable.
Your dedication to sharing knowledge is unmistakable, and your writing style is captivating. Your articles are a pleasure to read, and I consistently come away feeling enriched. Thank you for being a dependable source of inspiration and information.
This article resonated with me on a personal level. Your ability to emotionally connect with your audience is truly commendable. Your words are not only informative but also heartwarming. Thank you for sharing your insights.
民調
Your unique approach to addressing challenging subjects is like a breath of fresh air. Your articles stand out with their clarity and grace, making them a pure joy to read. Your blog has now become my go-to source for insightful content.
Your enthusiasm for the subject matter shines through every word of this article; it’s contagious! Your commitment to delivering valuable insights is greatly valued, and I eagerly anticipate more of your captivating content. Keep up the exceptional work!
Your dedication to sharing knowledge is unmistakable, and your writing style is captivating. Your articles are a pleasure to read, and I consistently come away feeling enriched. Thank you for being a dependable source of inspiration and information.
In a world where trustworthy information is more crucial than ever, your dedication to research and the provision of reliable content is truly commendable. Your commitment to accuracy and transparency shines through in every post. Thank you for being a beacon of reliability in the online realm.
總統民調
2024總統大選民調
民意調查是什麼?民調什麼意思?
民意調查又稱為輿論調查或民意測驗,簡稱民調。一般而言,民調是一種為了解公眾對某些政治、社會問題與政策的意見和態度,由專業民調公司或媒體進行的調查方法。
目的在於通過網路、電話、或書面等媒介,對大量樣本的問卷調查抽樣,利用統計學的抽樣理論來推斷較為客觀,且能較為精確地推論社會輿論或民意動向的一種方法。
以下是民意調查的一些基本特點和重要性:
抽樣:由於不可能向每一個人詢問意見,所以調查者會選擇一個代表性的樣本進行調查。這樣本的大小和抽樣方法都會影響調查的準確性和可靠性。
問卷設計:為了確保獲得可靠的結果,問卷必須經過精心設計,問題要清晰、不帶偏見,且易於理解。
數據分析:收集到的數據將被分析以得出結論。這可能包括計算百分比、平均值、標準差等,以及更複雜的統計分析。
多種用途:民意調查可以用於各種目的,包括政策制定、選舉預測、市場研究、社會科學研究等。
限制:雖然民意調查是一個有價值的工具,但它也有其限制。例如,樣本可能不完全代表目標人群,或者問卷的設計可能導致偏見。
影響決策:民意調查的結果常常被政府、企業和其他組織用來影響其決策。
透明度和誠實:為了維護調查的可信度,調查組織應該提供其調查方法、樣本大小、抽樣方法和可能的誤差範圍等詳細資訊。
民調是怎麼調查的?
民意調查(輿論調查)的意義是指為瞭解大多數民眾的看法、意見、利益與需求,以科學、系統與公正的資料,蒐集可以代表全部群眾(母體)的部分群眾(抽樣),設計問卷題目後,以人工或電腦詢問部分民眾對特定議題的看法與評價,利用抽樣出來部分民眾的意見與看法,來推論目前全部民眾的意見與看法,藉以衡量社會與政治的狀態。
以下是進行民調調查的基本步驟:
定義目標和目的:首先,調查者需要明確調查的目的。是要了解公眾對某個政策的看法?還是要評估某個政治候選人的支持率?
設計問卷:根據調查目的,研究者會設計一份問卷。問卷應該包含清晰、不帶偏見的問題,並避免導向性的語言。
選擇樣本:因為通常不可能調查所有人,所以會選擇一部分人作為代表。這部分人被稱為“樣本”。最理想的情況是使用隨機抽樣,以確保每個人都有被選中的機會。
收集數據:有多種方法可以收集數據,如面對面訪問、電話訪問、郵件調查或在線調查。
數據分析:一旦數據被收集,研究者會使用統計工具和技術進行分析,得出結論或洞見。
報告結果:分析完數據後,研究者會編寫報告或發布結果。報告通常會提供調查方法、樣本大小、誤差範圍和主要發現。
解釋誤差範圍:多數民調報告都會提供誤差範圍,例如“±3%”。這表示實際的結果有可能在報告結果的3%範圍內上下浮動。
民調調查的質量和可信度很大程度上取決於其設計和實施的方法。若是由專業和無偏見的組織進行,且使用科學的方法,那麼民調結果往往較為可靠。但即使是最高質量的民調也會有一定的誤差,因此解讀時應保持批判性思考。
為什麼要做民調?
民調提供了一種系統性的方式來了解大眾的意見、態度和信念。進行民調的原因多種多樣,以下是一些主要的動機:
政策制定和評估:政府和政策制定者進行民調,以了解公眾對某一議題或政策的看法。這有助於制定或調整政策,以反映大眾的需求和意見。
選舉和政治活動:政黨和候選人通常使用民調來評估自己在選舉中的地位,了解哪些議題對選民最重要,以及如何調整策略以吸引更多支持。
市場研究:企業和組織進行民調以了解消費者對產品、服務或品牌的態度,從而制定或調整市場策略。
社會科學研究:學者和研究者使用民調來了解人們的社會、文化和心理特征,以及其與行為的關係。
公眾與媒體的期望:民調提供了一種方式,使公眾、政府和企業得以了解社會的整體趨勢和態度。媒體也經常報導民調結果,提供公眾對當前議題的見解。
提供反饋和評估:無論是企業還是政府,都可以透過民調了解其表現、服務或政策的效果,並根據反饋進行改進。
預測和趨勢分析:民調可以幫助預測某些趨勢或行為的未來發展,如選舉結果、市場需求等。
教育和提高公眾意識:通過進行和公布民調,可以促使公眾對某一議題或問題有更深入的了解和討論。
民調可信嗎?
民意調查的結果數據隨處可見,尤其是政治性民調結果幾乎可說是天天在新聞上放送,對總統的滿意度下降了多少百分比,然而大家又信多少?
在景美市場的訪問中,我們了解到民眾對民調有一些普遍的觀點。大多數受訪者表示,他們對民調的可信度存有疑慮,主要原因是他們擔心政府可能會在調查中進行操控,以符合特定政治目標。
受訪者還提到,民意調查的結果通常不會對他們的投票意願產生影響。換句話說,他們的選擇通常受到更多因素的影響,例如候選人的政策立場和政府做事的認真與否,而不是單純依賴民調結果。
從訪問中我們可以得出的結論是,大多數民眾對民調持謹慎態度,並認為它們對他們的投票決策影響有限。
民意調查是什麼?民調什麼意思?
民意調查又稱為輿論調查或民意測驗,簡稱民調。一般而言,民調是一種為了解公眾對某些政治、社會問題與政策的意見和態度,由專業民調公司或媒體進行的調查方法。
目的在於通過網路、電話、或書面等媒介,對大量樣本的問卷調查抽樣,利用統計學的抽樣理論來推斷較為客觀,且能較為精確地推論社會輿論或民意動向的一種方法。
以下是民意調查的一些基本特點和重要性:
抽樣:由於不可能向每一個人詢問意見,所以調查者會選擇一個代表性的樣本進行調查。這樣本的大小和抽樣方法都會影響調查的準確性和可靠性。
問卷設計:為了確保獲得可靠的結果,問卷必須經過精心設計,問題要清晰、不帶偏見,且易於理解。
數據分析:收集到的數據將被分析以得出結論。這可能包括計算百分比、平均值、標準差等,以及更複雜的統計分析。
多種用途:民意調查可以用於各種目的,包括政策制定、選舉預測、市場研究、社會科學研究等。
限制:雖然民意調查是一個有價值的工具,但它也有其限制。例如,樣本可能不完全代表目標人群,或者問卷的設計可能導致偏見。
影響決策:民意調查的結果常常被政府、企業和其他組織用來影響其決策。
透明度和誠實:為了維護調查的可信度,調查組織應該提供其調查方法、樣本大小、抽樣方法和可能的誤差範圍等詳細資訊。
民調是怎麼調查的?
民意調查(輿論調查)的意義是指為瞭解大多數民眾的看法、意見、利益與需求,以科學、系統與公正的資料,蒐集可以代表全部群眾(母體)的部分群眾(抽樣),設計問卷題目後,以人工或電腦詢問部分民眾對特定議題的看法與評價,利用抽樣出來部分民眾的意見與看法,來推論目前全部民眾的意見與看法,藉以衡量社會與政治的狀態。
以下是進行民調調查的基本步驟:
定義目標和目的:首先,調查者需要明確調查的目的。是要了解公眾對某個政策的看法?還是要評估某個政治候選人的支持率?
設計問卷:根據調查目的,研究者會設計一份問卷。問卷應該包含清晰、不帶偏見的問題,並避免導向性的語言。
選擇樣本:因為通常不可能調查所有人,所以會選擇一部分人作為代表。這部分人被稱為“樣本”。最理想的情況是使用隨機抽樣,以確保每個人都有被選中的機會。
收集數據:有多種方法可以收集數據,如面對面訪問、電話訪問、郵件調查或在線調查。
數據分析:一旦數據被收集,研究者會使用統計工具和技術進行分析,得出結論或洞見。
報告結果:分析完數據後,研究者會編寫報告或發布結果。報告通常會提供調查方法、樣本大小、誤差範圍和主要發現。
解釋誤差範圍:多數民調報告都會提供誤差範圍,例如“±3%”。這表示實際的結果有可能在報告結果的3%範圍內上下浮動。
民調調查的質量和可信度很大程度上取決於其設計和實施的方法。若是由專業和無偏見的組織進行,且使用科學的方法,那麼民調結果往往較為可靠。但即使是最高質量的民調也會有一定的誤差,因此解讀時應保持批判性思考。
為什麼要做民調?
民調提供了一種系統性的方式來了解大眾的意見、態度和信念。進行民調的原因多種多樣,以下是一些主要的動機:
政策制定和評估:政府和政策制定者進行民調,以了解公眾對某一議題或政策的看法。這有助於制定或調整政策,以反映大眾的需求和意見。
選舉和政治活動:政黨和候選人通常使用民調來評估自己在選舉中的地位,了解哪些議題對選民最重要,以及如何調整策略以吸引更多支持。
市場研究:企業和組織進行民調以了解消費者對產品、服務或品牌的態度,從而制定或調整市場策略。
社會科學研究:學者和研究者使用民調來了解人們的社會、文化和心理特征,以及其與行為的關係。
公眾與媒體的期望:民調提供了一種方式,使公眾、政府和企業得以了解社會的整體趨勢和態度。媒體也經常報導民調結果,提供公眾對當前議題的見解。
提供反饋和評估:無論是企業還是政府,都可以透過民調了解其表現、服務或政策的效果,並根據反饋進行改進。
預測和趨勢分析:民調可以幫助預測某些趨勢或行為的未來發展,如選舉結果、市場需求等。
教育和提高公眾意識:通過進行和公布民調,可以促使公眾對某一議題或問題有更深入的了解和討論。
民調可信嗎?
民意調查的結果數據隨處可見,尤其是政治性民調結果幾乎可說是天天在新聞上放送,對總統的滿意度下降了多少百分比,然而大家又信多少?
在景美市場的訪問中,我們了解到民眾對民調有一些普遍的觀點。大多數受訪者表示,他們對民調的可信度存有疑慮,主要原因是他們擔心政府可能會在調查中進行操控,以符合特定政治目標。
受訪者還提到,民意調查的結果通常不會對他們的投票意願產生影響。換句話說,他們的選擇通常受到更多因素的影響,例如候選人的政策立場和政府做事的認真與否,而不是單純依賴民調結果。
從訪問中我們可以得出的結論是,大多數民眾對民調持謹慎態度,並認為它們對他們的投票決策影響有限。
I’m curious to find out what blog platform you are using? I’m having some minor security issues with my latest blog and I’d like to find something more r********. Do you have any solutions?
Your unique approach to addressing challenging subjects is like a breath of fresh air. Your articles stand out with their clarity and grace, making them a pure joy to read. Your blog has now become my go-to source for insightful content.
Your positivity and enthusiasm are truly infectious! This article brightened my day and left me feeling inspired. Thank you for sharing your uplifting message and spreading positivity to your readers.
I’m genuinely impressed by how effortlessly you distill intricate concepts into easily digestible information. Your writing style not only imparts knowledge but also engages the reader, making the learning experience both enjoyable and memorable. Your passion for sharing your expertise shines through, and for that, I’m deeply grateful.
民調
民意調查是什麼?民調什麼意思?
民意調查又稱為輿論調查或民意測驗,簡稱民調。一般而言,民調是一種為了解公眾對某些政治、社會問題與政策的意見和態度,由專業民調公司或媒體進行的調查方法。
目的在於通過網路、電話、或書面等媒介,對大量樣本的問卷調查抽樣,利用統計學的抽樣理論來推斷較為客觀,且能較為精確地推論社會輿論或民意動向的一種方法。
以下是民意調查的一些基本特點和重要性:
抽樣:由於不可能向每一個人詢問意見,所以調查者會選擇一個代表性的樣本進行調查。這樣本的大小和抽樣方法都會影響調查的準確性和可靠性。
問卷設計:為了確保獲得可靠的結果,問卷必須經過精心設計,問題要清晰、不帶偏見,且易於理解。
數據分析:收集到的數據將被分析以得出結論。這可能包括計算百分比、平均值、標準差等,以及更複雜的統計分析。
多種用途:民意調查可以用於各種目的,包括政策制定、選舉預測、市場研究、社會科學研究等。
限制:雖然民意調查是一個有價值的工具,但它也有其限制。例如,樣本可能不完全代表目標人群,或者問卷的設計可能導致偏見。
影響決策:民意調查的結果常常被政府、企業和其他組織用來影響其決策。
透明度和誠實:為了維護調查的可信度,調查組織應該提供其調查方法、樣本大小、抽樣方法和可能的誤差範圍等詳細資訊。
民調是怎麼調查的?
民意調查(輿論調查)的意義是指為瞭解大多數民眾的看法、意見、利益與需求,以科學、系統與公正的資料,蒐集可以代表全部群眾(母體)的部分群眾(抽樣),設計問卷題目後,以人工或電腦詢問部分民眾對特定議題的看法與評價,利用抽樣出來部分民眾的意見與看法,來推論目前全部民眾的意見與看法,藉以衡量社會與政治的狀態。
以下是進行民調調查的基本步驟:
定義目標和目的:首先,調查者需要明確調查的目的。是要了解公眾對某個政策的看法?還是要評估某個政治候選人的支持率?
設計問卷:根據調查目的,研究者會設計一份問卷。問卷應該包含清晰、不帶偏見的問題,並避免導向性的語言。
選擇樣本:因為通常不可能調查所有人,所以會選擇一部分人作為代表。這部分人被稱為“樣本”。最理想的情況是使用隨機抽樣,以確保每個人都有被選中的機會。
收集數據:有多種方法可以收集數據,如面對面訪問、電話訪問、郵件調查或在線調查。
數據分析:一旦數據被收集,研究者會使用統計工具和技術進行分析,得出結論或洞見。
報告結果:分析完數據後,研究者會編寫報告或發布結果。報告通常會提供調查方法、樣本大小、誤差範圍和主要發現。
解釋誤差範圍:多數民調報告都會提供誤差範圍,例如“±3%”。這表示實際的結果有可能在報告結果的3%範圍內上下浮動。
民調調查的質量和可信度很大程度上取決於其設計和實施的方法。若是由專業和無偏見的組織進行,且使用科學的方法,那麼民調結果往往較為可靠。但即使是最高質量的民調也會有一定的誤差,因此解讀時應保持批判性思考。
為什麼要做民調?
民調提供了一種系統性的方式來了解大眾的意見、態度和信念。進行民調的原因多種多樣,以下是一些主要的動機:
政策制定和評估:政府和政策制定者進行民調,以了解公眾對某一議題或政策的看法。這有助於制定或調整政策,以反映大眾的需求和意見。
選舉和政治活動:政黨和候選人通常使用民調來評估自己在選舉中的地位,了解哪些議題對選民最重要,以及如何調整策略以吸引更多支持。
市場研究:企業和組織進行民調以了解消費者對產品、服務或品牌的態度,從而制定或調整市場策略。
社會科學研究:學者和研究者使用民調來了解人們的社會、文化和心理特征,以及其與行為的關係。
公眾與媒體的期望:民調提供了一種方式,使公眾、政府和企業得以了解社會的整體趨勢和態度。媒體也經常報導民調結果,提供公眾對當前議題的見解。
提供反饋和評估:無論是企業還是政府,都可以透過民調了解其表現、服務或政策的效果,並根據反饋進行改進。
預測和趨勢分析:民調可以幫助預測某些趨勢或行為的未來發展,如選舉結果、市場需求等。
教育和提高公眾意識:通過進行和公布民調,可以促使公眾對某一議題或問題有更深入的了解和討論。
民調可信嗎?
民意調查的結果數據隨處可見,尤其是政治性民調結果幾乎可說是天天在新聞上放送,對總統的滿意度下降了多少百分比,然而大家又信多少?
在景美市場的訪問中,我們了解到民眾對民調有一些普遍的觀點。大多數受訪者表示,他們對民調的可信度存有疑慮,主要原因是他們擔心政府可能會在調查中進行操控,以符合特定政治目標。
受訪者還提到,民意調查的結果通常不會對他們的投票意願產生影響。換句話說,他們的選擇通常受到更多因素的影響,例如候選人的政策立場和政府做事的認真與否,而不是單純依賴民調結果。
從訪問中我們可以得出的結論是,大多數民眾對民調持謹慎態度,並認為它們對他們的投票決策影響有限。
Your positivity and enthusiasm are undeniably contagious! This article brightened my day and left me feeling inspired. Thank you for sharing your uplifting message and spreading positivity among your readers.
I am continually impressed by your ability to delve into subjects with grace and clarity. Your articles are both informative and enjoyable to read, a rare combination. Your blog is a valuable resource, and I am sincerely grateful for it.
Your blog has rapidly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you invest in crafting each article. Your dedication to delivering high-quality content is apparent, and I eagerly await every new post.
I couldn’t agree more with the insightful points you’ve articulated in this article. Your profound knowledge on the subject is evident, and your unique perspective adds an invaluable dimension to the discourse. This is a must-read for anyone interested in this topic.
This article is a real game-changer! Your practical tips and well-thought-out suggestions are incredibly valuable. I can’t wait to put them into action. Thank you for not only sharing your expertise but also making it accessible and easy to implement.
In a world where trustworthy information is more crucial than ever, your dedication to research and the provision of reliable content is truly commendable. Your commitment to accuracy and transparency shines through in every post. Thank you for being a beacon of reliability in the online realm.
Your blog has rapidly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you invest in crafting each article. Your dedication to delivering high-quality content is apparent, and I eagerly await every new post.
Your writing style effortlessly draws me in, and I find it difficult to stop reading until I reach the end of your articles. Your ability to make complex subjects engaging is a true gift. Thank you for sharing your expertise!
I must applaud your talent for simplifying complex topics. Your ability to convey intricate ideas in such a relatable manner is admirable. You’ve made learning enjoyable and accessible for many, and I deeply appreciate that.
Wow! This can be one particular of the most beneficial blogs We’ve ever arrive across on this subject. Actually Fantastic. I am also an expert in this topic so I can understand your hard work.
I couldn’t agree more with the insightful points you’ve articulated in this article. Your profound knowledge on the subject is evident, and your unique perspective adds an invaluable dimension to the discourse. This is a must-read for anyone interested in this topic.
I must applaud your talent for simplifying complex topics. Your ability to convey intricate ideas in such a relatable manner is admirable. You’ve made learning enjoyable and accessible for many, and I deeply appreciate that.
Your blog has rapidly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you invest in crafting each article. Your dedication to delivering high-quality content is apparent, and I eagerly await every new post.
This article resonated with me on a personal level. Your ability to emotionally connect with your audience is truly commendable. Your words are not only informative but also heartwarming. Thank you for sharing your insights.
I’m genuinely impressed by how effortlessly you distill intricate concepts into easily digestible information. Your writing style not only imparts knowledge but also engages the reader, making the learning experience both enjoyable and memorable. Your passion for sharing your expertise shines through, and for that, I’m deeply grateful.
Your positivity and enthusiasm are undeniably contagious! This article brightened my day and left me feeling inspired. Thank you for sharing your uplifting message and spreading positivity among your readers.
Your passion and dedication to your craft radiate through every article. Your positive energy is infectious, and it’s evident that you genuinely care about your readers’ experience. Your blog brightens my day!
I’ve discovered a treasure trove of knowledge in your blog. Your unwavering dedication to offering trustworthy information is truly commendable. Each visit leaves me more enlightened, and I deeply appreciate your consistent reliability.
You made some good points there. I looked on the web to learn more about the issue and found most individuals will go along with your views on this web site.
I wanted to take a moment to express my gratitude for the wealth of invaluable information you consistently provide in your articles. Your blog has become my go-to resource, and I consistently emerge with new knowledge and fresh perspectives. I’m eagerly looking forward to continuing my learning journey through your future posts.
Your unique approach to tackling challenging subjects is a breath of fresh air. Your articles stand out with their clarity and grace, making them a joy to read. Your blog is now my go-to for insightful content.
Your unique approach to tackling challenging subjects is a breath of fresh air. Your articles stand out with their clarity and grace, making them a joy to read. Your blog is now my go-to for insightful content.
I am continually impressed by your ability to delve into subjects with grace and clarity. Your articles are both informative and enjoyable to read, a rare combination. Your blog is a valuable resource, and I am sincerely grateful for it.
This article resonated with me on a personal level. Your ability to emotionally connect with your audience is truly commendable. Your words are not only informative but also heartwarming. Thank you for sharing your insights.
You could definitely see your skills in the work you write. The world hopes for more passionate writers like you who aren’t afraid to say how they believe. Always follow your heart.
Your passion and dedication to your craft radiate through every article. Your positive energy is infectious, and it’s evident that you genuinely care about your readers’ experience. Your blog brightens my day!
I’ve discovered a treasure trove of knowledge in your blog. Your unwavering dedication to offering trustworthy information is truly commendable. Each visit leaves me more enlightened, and I deeply appreciate your consistent reliability.
This article resonated with me on a personal level. Your ability to emotionally connect with your audience is truly commendable. Your words are not only informative but also heartwarming. Thank you for sharing your insights.
I must applaud your talent for simplifying complex topics. Your ability to convey intricate ideas in such a relatable manner is admirable. You’ve made learning enjoyable and accessible for many, and I deeply appreciate that.
Your writing style effortlessly draws me in, and I find it nearly impossible to stop reading until I’ve reached the end of your articles. Your ability to make complex subjects engaging is indeed a rare gift. Thank you for sharing your expertise!
Your dedication to sharing knowledge is unmistakable, and your writing style is captivating. Your articles are a pleasure to read, and I consistently come away feeling enriched. Thank you for being a dependable source of inspiration and information.
I really like it when folks come together and share ideas. Great blog, stick with it.
🌌 Wow, blog ini seperti roket meluncurkan ke galaksi dari keajaiban! 🌌 Konten yang menarik di sini adalah perjalanan rollercoaster yang mendebarkan bagi pikiran, memicu ketertarikan setiap saat. 💫 Baik itu gayahidup, blog ini adalah harta karun wawasan yang mendebarkan! 🌟 Berangkat ke dalam pengalaman menegangkan ini dari imajinasi dan biarkan pikiran Anda melayang! 🌈 Jangan hanya membaca, rasakan kegembiraan ini! 🌈 Pikiran Anda akan berterima kasih untuk perjalanan mendebarkan ini melalui ranah keajaiban yang menakjubkan! 🚀
I need to to thank you for this wonderful read!! I absolutely loved every bit of it. I’ve got you bookmarked to check out new stuff you post…
You have made some decent points there. I looked on the internet for more info about the issue and found most people will go along with your views on this website.
I want to express my appreciation for this insightful article. Your unique perspective and well-researched content bring a new depth to the subject matter. It’s clear you’ve put a lot of thought into this, and your ability to convey complex ideas in such a clear and understandable way is truly commendable. Thank you for sharing your knowledge and making learning enjoyable.
Your passion and dedication to your craft radiate through every article. Your positive energy is infectious, and it’s evident that you genuinely care about your readers’ experience. Your blog brightens my day!
I wanted to take a moment to express my gratitude for the wealth of invaluable information you consistently provide in your articles. Your blog has become my go-to resource, and I consistently emerge with new knowledge and fresh perspectives. I’m eagerly looking forward to continuing my learning journey through your future posts.
I wanted to take a moment to express my gratitude for the wealth of invaluable information you consistently provide in your articles. Your blog has become my go-to resource, and I consistently emerge with new knowledge and fresh perspectives. I’m eagerly looking forward to continuing my learning journey through your future posts.
This article is a refreshing change! The author’s unique perspective and thoughtful analysis have made this a truly fascinating read. I’m thankful for the effort he has put into creating such an educational and provocative piece. Thank you, author, for offering your expertise and igniting meaningful discussions through your brilliant writing!
An outstanding share! I have just forwarded this onto a colleague who has been doing a little homework on this. And he actually bought me breakfast simply because I discovered it for him… lol. So allow me to reword this…. Thanks for the meal!! But yeah, thanks for spending the time to talk about this matter here on your blog.
I was able to find good information from your blog posts.
Right here is the perfect webpage for anybody who hopes to find out about this topic. You understand a whole lot its almost hard to argue with you (not that I really will need to…HaHa). You definitely put a brand new spin on a subject that’s been discussed for ages. Excellent stuff, just wonderful.
I must applaud your talent for simplifying complex topics. Your ability to convey intricate ideas in such a relatable manner is admirable. You’ve made learning enjoyable and accessible for many, and I deeply appreciate that.
It’s hard to find educated people on this subject, but you seem like you know what you’re talking about! Thanks
Hello there! I could have sworn I’ve been to this website before but after browsing through many of the articles I realized it’s new to me. Regardless, I’m definitely happy I found it and I’ll be book-marking it and checking back regularly.
娛樂城
Hello there! I could have sworn I’ve been to this site before but after browsing through many of the posts I realized it’s new to me. Anyhow, I’m certainly happy I discovered it and I’ll be bookmarking it and checking back frequently.
Spot on with this write-up, I actually think this web site needs far more attention. I’ll probably be returning to read through more, thanks for the advice.
Very good info. Lucky me I found your site by accident (stumbleupon). I’ve bookmarked it for later.
SightCare supports overall eye health, enhances vision, and protects against oxidative stress. Take control of your eye health and enjoy the benefits of clear and vibrant eyesight with Sight Care. https://sightcarebuynow.us/
Great blog you’ve got here.. It’s hard to find quality writing like yours these days. I truly appreciate individuals like you! Take care!!
Your unique approach to addressing challenging subjects is like a breath of fresh air. Your articles stand out with their clarity and grace, making them a pure joy to read. Your blog has now become my go-to source for insightful content.
I gave [url=https://www.cornbreadhemp.com/products/cbd-sleep-gummies ]cbd gummy for sleep[/url] a prove payment the cardinal habits, and I’m amazed! They tasted distinguished and provided a be under the impression that of calmness and relaxation. My emphasis melted away, and I slept well-advised too. These gummies are a game-changer an eye to me, and I extremely endorse them to anyone seeking natural emphasis relief and improved sleep.
Way cool! Some very valid points! I appreciate you writing this post and the rest of the website is really good.
Good info. Lucky me I ran across your blog by chance (stumbleupon). I have saved it for later.
You are so awesome! I don’t believe I have read anything like this before. So nice to discover somebody with genuine thoughts on this topic. Seriously.. thanks for starting this up. This web site is something that is needed on the internet, someone with a little originality.
Can I simply say what a comfort to uncover an individual who truly knows what they are talking about over the internet. You actually understand how to bring an issue to light and make it important. More people must look at this and understand this side of the story. It’s surprising you are not more popular because you certainly possess the gift.
Aizen Power is an all-natural supplement designed to improve male health. This formula contains the beneficial properties of various plants, herbs, minerals, and vitamins that help men’s blood circulation, detoxification, and overall health. https://aizenpowerbuynow.us/
You need to take part in a contest for one of the most useful sites on the web. I’m going to recommend this site!
Excellent write-up. I certainly love this site. Continue the good work!
Your storytelling prowess is nothing short of extraordinary. Reading this article felt like embarking on an adventure of its own. The vivid descriptions and engaging narrative transported me, and I eagerly await to see where your next story takes us. Thank you for sharing your experiences in such a captivating manner.
I can’t help but be impressed by the way you break down complex concepts into easy-to-digest information. Your writing style is not only informative but also engaging, which makes the learning experience enjoyable and memorable. It’s evident that you have a passion for sharing your knowledge, and I’m grateful for that.
Your dedication to sharing knowledge is unmistakable, and your writing style is captivating. Your articles are a pleasure to read, and I consistently come away feeling enriched. Thank you for being a dependable source of inspiration and information.
FlowForce Max is an innovative, natural and effective way to address your prostate problems, while addressing your energy, libido, and vitality. https://flowforcemaxbuynow.us/
Way cool! Some very valid points! I appreciate you writing this article and the rest of the website is also really good.
This article resonated with me on a personal level. Your ability to emotionally connect with your audience is truly commendable. Your words are not only informative but also heartwarming. Thank you for sharing your insights.
This article is a real game-changer! Your practical tips and well-thought-out suggestions are incredibly valuable. I can’t wait to put them into action. Thank you for not only sharing your expertise but also making it accessible and easy to implement.
bookmarked!!, I really like your website!
Hi there, I think your web site may be having internet browser compatibility problems. When I look at your website in Safari, it looks fine but when opening in Internet Explorer, it’s got some overlapping issues. I merely wanted to give you a quick heads up! Apart from that, fantastic blog!
Good article! We will be linking to this great article on our site. Keep up the great writing.
I want to express my appreciation for this insightful article. Your unique perspective and well-researched content bring a new depth to the subject matter. It’s clear you’ve put a lot of thought into this, and your ability to convey complex ideas in such a clear and understandable way is truly commendable. Thank you for sharing your knowledge and making learning enjoyable.
I’ve discovered a treasure trove of knowledge in your blog. Your unwavering dedication to offering trustworthy information is truly commendable. Each visit leaves me more enlightened, and I deeply appreciate your consistent reliability.
An outstanding share! I’ve just forwarded this onto a colleague who was doing a little research on this. And he actually ordered me dinner due to the fact that I discovered it for him… lol. So allow me to reword this…. Thanks for the meal!! But yeah, thanks for spending time to talk about this subject here on your web page.
I absolutely love your blog.. Very nice colors & theme. Did you build this amazing site yourself? Please reply back as I’m attempting to create my very own site and would love to learn where you got this from or what the theme is named. Kudos!
Simply wish to say your article is as astounding. The clearness in your post is just spectacular and i can assume you are an expert on this subject. Well with your permission allow me to grab your feed to keep up to date with forthcoming post. Thanks a million and please keep up the rewarding work.
Your blog has rapidly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you invest in crafting each article. Your dedication to delivering high-quality content is apparent, and I eagerly await every new post.
I wish to express my deep gratitude for this enlightening article. Your distinct perspective and meticulously researched content bring fresh depth to the subject matter. It’s evident that you’ve invested a significant amount of thought into this, and your ability to convey complex ideas in such a clear and understandable manner is truly praiseworthy. Thank you for generously sharing your knowledge and making the learning process so enjoyable.
I must applaud your talent for simplifying complex topics. Your ability to convey intricate ideas in such a relatable manner is admirable. You’ve made learning enjoyable and accessible for many, and I deeply appreciate that.
I must applaud your talent for simplifying complex topics. Your ability to convey intricate ideas in such a relatable manner is admirable. You’ve made learning enjoyable and accessible for many, and I deeply appreciate that.
In a world where trustworthy information is more crucial than ever, your dedication to research and the provision of reliable content is truly commendable. Your commitment to accuracy and transparency shines through in every post. Thank you for being a beacon of reliability in the online realm.
I wish to express my deep gratitude for this enlightening article. Your distinct perspective and meticulously researched content bring fresh depth to the subject matter. It’s evident that you’ve invested a significant amount of thought into this, and your ability to convey complex ideas in such a clear and understandable manner is truly praiseworthy. Thank you for generously sharing your knowledge and making the learning process so enjoyable.
I wanted to take a moment to express my gratitude for the wealth of valuable information you provide in your articles. Your blog has become a go-to resource for me, and I always come away with new knowledge and fresh perspectives. I’m excited to continue learning from your future posts.
I could not refrain from commenting. Well written.
Hi, I do think this is an excellent blog. I stumbledupon it 😉 I am going to revisit once again since I saved as a favorite it. Money and freedom is the greatest way to change, may you be rich and continue to guide other people.
Your storytelling prowess is nothing short of extraordinary. Reading this article felt like embarking on an adventure of its own. The vivid descriptions and engaging narrative transported me, and I eagerly await to see where your next story takes us. Thank you for sharing your experiences in such a captivating manner.
This article resonated with me on a personal level. Your ability to emotionally connect with your audience is truly commendable. Your words are not only informative but also heartwarming. Thank you for sharing your insights.
Your blog has quickly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you put into crafting each article. Your dedication to delivering high-quality content is evident, and I look forward to every new post.
Your passion and dedication to your craft radiate through every article. Your positive energy is infectious, and it’s evident that you genuinely care about your readers’ experience. Your blog brightens my day!
Digestyl™ is natural, potent and effective mixture, in the form of a powerful pill that would detoxify the gut and rejuvenate the whole organism in order to properly digest and get rid of the Clostridium Perfringens. https://digestylbuynow.us/
LeanBliss is a unique w********** formula that promotes optimal weight and balanced blood sugar levels while curbing your appetite, detoxifying, and boosting your metabolism. https://leanblissbuynow.us/
EyeFortin is an all-natural eye-health supplement that helps to keep your eyes healthy even as you age. It prevents infections and detoxifies your eyes while also being stimulant-free. This makes it a great choice for those who are looking for a natural way to improve their eye health. https://eyefortinbuynow.us/
Fast Lean Pro is a herbal supplement that tricks your brain into imagining that you’re fasting and helps you maintain a healthy weight no matter when or what you eat. It offers a novel approach to reducing fat accumulation and promoting long-term weight management. https://fastleanprobuynow.us/
EndoPump is a dietary supplement for men’s health. This supplement is said to improve the strength and stamina required by your body to perform various physical tasks. Because the supplement addresses issues associated with aging, it also provides support for a variety of other age-related issues that may affect the body. https://endopumpbuynow.us/
Illuderma is a serum designed to deeply nourish, clear, and hydrate the skin. The goal of this solution began with dark spots, which were previously thought to be a natural symptom of ageing. The creators of Illuderma were certain that blue modern radiation is the source of dark spots after conducting extensive research. https://illudermabuynow.us/
Java Burn is a proprietary blend of metabolism-boosting ingredients that work together to promote w********** in your body. https://javaburnbuynow.us/
I wanted to take a moment to express my gratitude for the wealth of valuable information you provide in your articles. Your blog has become a go-to resource for me, and I always come away with new knowledge and fresh perspectives. I’m excited to continue learning from your future posts.
long term car rental Dubai
Dubai, a city known for its opulence and modernity, demands a mode of transportation that reflects its grandeur. For those seeking a cost-effective and reliable long-term solution, Somonion Rent Car LLC emerges as the premier choice for monthly car rentals in Dubai. With a diverse fleet ranging from compact cars to premium vehicles, the company promises an unmatched blend of affordability, flexibility, and personalized service.
Favorable Rental Conditions:
Understanding the potential financial strain of long-term car rentals, Somonion Rent Car LLC aims to make your journey more economical. The company offers flexible rental terms coupled with exclusive discounts for loyal customers. This commitment to affordability extends beyond the rental cost, as additional services such as insurance, maintenance, and repair ensure your safety and peace of mind throughout the duration of your rental.
A Plethora of Options:
Somonion Rent Car LLC boasts an extensive selection of vehicles to cater to diverse preferences and budgets. Whether you’re in the market for a sleek sedan or a spacious crossover, the company has the perfect car to complement your needs. The transparency in pricing, coupled with the ease of booking through their online platform, makes Somonion Rent Car LLC a hassle-free solution for those embarking on a long-term adventure in Dubai.
Car Rental Services Tailored for You:
Somonion Rent Car LLC doesn’t just offer cars; it provides a comprehensive range of rental services tailored to suit various occasions. From daily and weekly rentals to airport transfers and business travel, the company ensures that your stay in Dubai is not only comfortable but also exudes prestige. The fleet includes popular models such as the Nissan Altima 2018, KIA Forte 2018, Hyundai Elantra 2018, and the Toyota Camry Sport Edition 2020, all available for monthly rentals at competitive rates.
Featured Deals and Specials:
Somonion Rent Car LLC constantly updates its offerings to provide customers with the best deals. Featured cars like the Hyundai Sonata 2018 and Hyundai Santa Fe 2018 add a touch of l***** to your rental experience, with daily rates starting as low as AED 100. The company’s commitment to affordable l***** is further emphasized by the online booking system, allowing customers to secure the best deals in real-time through their website or by contacting the experts via phone or WhatsApp.
Conclusion:
Whether you’re a tourist looking to explore Dubai at your pace or a business traveler in need of a reliable and prestigious mode of transportation, Somonion Rent Car LLC stands as the go-to choice for monthly car rentals in Dubai. Unlock the ultimate mobility experience with Somonion, where affordability meets excellence, ensuring your journey through Dubai is as seamless and luxurious as the city itself. Contact Somonion Rent Car LLC today and embark on a journey where every mile is a testament to comfort, style, and unmatched service.
Hi, I do think this is an excellent blog. I stumbledupon it 😉 I may come back once again since I book-marked it. Money and freedom is the greatest way to change, may you be rich and continue to help other people.
Your blog is a true gem in the vast online world. Your consistent delivery of high-quality content is admirable. Thank you for always going above and beyond in providing valuable insights. Keep up the fantastic work!
I was more than happy to discover this great site. I want to to thank you for your time just for this wonderful read!! I definitely loved every little bit of it and i also have you book marked to see new things on your site.
One important thing is that if you find yourself searching for a student loan you may find that you’ll want a co-signer. There are many cases where this is correct because you will find that you do not have a past credit score so the mortgage lender will require that you’ve got someone cosign the money for you. Good post.
I must thank you for the efforts you have put in penning this blog. I am hoping to view the same high-grade blog posts from you in the future as well. In fact, your creative writing abilities has motivated me to get my own, personal website now 😉
Pretty! This was a really wonderful article. Many thanks for supplying this information.
You’re so interesting! I do not suppose I’ve read anything like this before. So wonderful to find somebody with a few original thoughts on this subject matter. Seriously.. thank you for starting this up. This site is something that is required on the internet, someone with a little originality.
Your style is unique compared to other people I’ve read stuff from. Many thanks for posting when you’ve got the opportunity, Guess I will just book mark this site.
Your storytelling abilities are nothing short of incredible. Reading this article felt like embarking on an adventure of its own. The vivid descriptions and engaging narrative transported me, and I can’t wait to see where your next story takes us. Thank you for sharing your experiences in such a captivating way.
I am continually impressed by your ability to delve into subjects with grace and clarity. Your articles are both informative and enjoyable to read, a rare combination. Your blog is a valuable resource, and I am sincerely grateful for it.
You ought to be a part of a contest for one of the best websites on the internet. I most certainly will recommend this site!
After looking into a handful of the articles on your web page, I honestly like your way of writing a blog. I book-marked it to my bookmark website list and will be checking back soon. Please visit my website too and tell me your opinion.
I simply wanted to convey how much I’ve gleaned from this article. Your meticulous research and clear explanations make the information accessible to all readers. It’s abundantly clear that you’re committed to providing valuable content.
I’m genuinely impressed by how effortlessly you distill intricate concepts into easily digestible information. Your writing style not only imparts knowledge but also engages the reader, making the learning experience both enjoyable and memorable. Your passion for sharing your expertise shines through, and for that, I’m deeply grateful.
I am continually impressed by your ability to delve into subjects with grace and clarity. Your articles are both informative and enjoyable to read, a rare combination. Your blog is a valuable resource, and I am sincerely grateful for it.
Very good info. Lucky me I recently found your site by chance (stumbleupon). I’ve book marked it for later!
Excellent site you have got here.. It’s hard to find excellent writing like yours these days. I honestly appreciate people like you! Take care!!
Spot on with this write-up, I seriously believe that this site needs a great deal more attention. I’ll probably be returning to read through more, thanks for the advice.
I simply wanted to convey how much I’ve gleaned from this article. Your meticulous research and clear explanations make the information accessible to all readers. It’s abundantly clear that you’re committed to providing valuable content.
In a world where trustworthy information is more crucial than ever, your dedication to research and the provision of reliable content is truly commendable. Your commitment to accuracy and transparency shines through in every post. Thank you for being a beacon of reliability in the online realm.
Your unique approach to addressing challenging subjects is like a breath of fresh air. Your articles stand out with their clarity and grace, making them a pure joy to read. Your blog has now become my go-to source for insightful content.
Excellent post. I’m going through many of these issues as well..
I used to be able to find good advice from your blog posts.
Деревянные дома под ключ
Дома АВС – Ваш уютный уголок
Мы строим не просто дома, мы создаем пространство, где каждый уголок будет наполнен комфортом и радостью жизни. Наш приоритет – не просто предоставить место для проживания, а создать настоящий дом, где вы будете чувствовать себя счастливыми и уютно.
В нашем информационном разделе “ПРОЕКТЫ” вы всегда найдете вдохновение и новые идеи для строительства вашего будущего дома. Мы постоянно работаем над тем, чтобы предложить вам самые инновационные и стильные проекты.
Мы убеждены, что основа хорошего дома – это его дизайн. Поэтому мы предоставляем услуги опытных дизайнеров-архитекторов, которые помогут вам воплотить все ваши идеи в жизнь. Наши архитекторы и персональные консультанты всегда готовы поделиться своим опытом и предложить функциональные и комфортные решения для вашего будущего дома.
Мы стремимся сделать весь процесс строительства максимально комфортным для вас. Наша команда предоставляет детализированные сметы, разрабатывает четкие этапы строительства и осуществляет контроль качества на каждом этапе.
Для тех, кто ценит экологичность и близость к природе, мы предлагаем деревянные дома премиум-класса. Используя клееный брус и оцилиндрованное бревно, мы создаем уникальные и здоровые условия для вашего проживания.
Тем, кто предпочитает надежность и многообразие форм, мы предлагаем дома из камня, блоков и кирпичной кладки.
Для практичных и ценящих свое время людей у нас есть быстровозводимые каркасные дома и эконом-класса. Эти решения обеспечат вас комфортным проживанием в кратчайшие сроки.
С Домами АВС создайте свой уютный уголок, где каждый момент жизни будет наполнен радостью и удовлетворением
ATG戰神賽特
2024全新上線❰戰神賽特老虎機❱ – ATG賽特玩法說明介紹
❰戰神賽特老虎機❱是由ATG電子獨家開發的古埃及風格線上老虎機,在傳說中戰神賽特是「力量之神」與奈芙蒂斯女神結成連理,共同守護古埃及的奇幻秘寶,只有被選中的冒險者才能進入探險。
❰戰神賽特老虎機❱ – ATG賽特介紹
2024最新老虎機【戰神塞特】- ATG電子 X 富遊娛樂城
❰戰神賽特老虎機❱ – ATG電子
線上老虎機系統 : ATG電子
發行年分 : 2024年1月
最大倍數 : 51000倍
返還率 : 95.89%
支付方式 : 全盤倍數、消除掉落
最低投注金額 : 0.4元
最高投注金額 : 2000元
可否選台 : 是
可選台台數 : 350台
免費遊戲 : 選轉觸發+購買特色
❰戰神賽特老虎機❱ 賠率說明
戰神塞特老虎機賠率算法非常簡單,玩家們只需要不斷的轉動老虎機,成功消除物件即可贏分,得分賠率依賠率表計算。
當盤面上沒有物件可以消除時,倍數符號將會相加形成總倍數!該次旋轉的總贏分即為 : 贏分 X 總倍數。
積分方式如下 :
贏分=(單次押注額/20) X 物件賠率
EX : 單次押注額為1,盤面獲得12個戰神賽特倍數符號法老魔眼
贏分= (1/20) X 1000=50
以下為各個得分符號數量之獎金賠率 :
得分符號 獎金倍數 得分符號 獎金倍數
戰神賽特倍數符號聖甲蟲 6 2000
5 100
4 60 戰神賽特倍數符號黃寶石 12+ 200
10-11 30
8-9 20
戰神賽特倍數符號荷魯斯之眼 12+ 1000
10-11 500
8-9 200 戰神賽特倍數符號紅寶石 12+ 160
10-11 24
8-9 16
戰神賽特倍數符號眼鏡蛇 12+ 500
10-11 200
8-9 50 戰神賽特倍數符號紫鑽石 12+ 100
10-11 20
8-9 10
戰神賽特倍數符號神箭 12+ 300
10-11 100
8-9 40 戰神賽特倍數符號藍寶石 12+ 80
10-11 18
8-9 8
戰神賽特倍數符號屠鐮刀 12+ 240
10-11 40
8-9 30 戰神賽特倍數符號綠寶石 12+ 40
10-11 15
8-9 5
❰戰神賽特老虎機❱ 賠率說明(橘色數值為獲得數量、黑色數值為得分賠率)
ATG賽特 – 特色說明
ATG賽特 – 倍數符號獎金加乘
玩家們在看到盤面上出現倍數符號時,務必把握機會加速轉動ATG賽特老虎機,倍數符號會隨機出現2到500倍的隨機倍數。
當盤面無法在消除時,這些倍數總和會相加,乘上當時累積之獎金,即為最後得分總額。
倍數符號會出現在主遊戲和免費遊戲當中,玩家們千萬別錯過這個可以瞬間將得獎金額拉高的好機會!
ATG賽特 – 倍數符號獎金加乘
ATG賽特 – 倍數符號圖示
ATG賽特 – 進入神秘金字塔開啟免費遊戲
戰神賽特倍數符號聖甲蟲
❰戰神賽特老虎機❱ 免費遊戲符號
在古埃及神話中,聖甲蟲又稱為「死亡之蟲」,它被當成了天球及重生的象徵,守護古埃及的奇幻秘寶。
當玩家在盤面上,看見越來越多的聖甲蟲時,千萬不要膽怯,只需在牌面上斬殺4~6個ATG賽特免費遊戲符號,就可以進入15場免費遊戲!
在免費遊戲中若轉出3~6個聖甲蟲免費遊戲符號,可額外獲得5次免費遊戲,最高可達100次。
當玩家的累積贏分且盤面有倍數物件時,盤面上的所有倍數將會加入總倍數!
ATG賽特 – 選台模式贏在起跑線
為避免神聖的寶物被盜墓者奪走,富有智慧的法老王將金子塔內佈滿迷宮,有的設滿機關讓盜墓者寸步難行,有的暗藏機關可以直接前往存放神秘寶物的暗房。
ATG賽特老虎機設有350個機檯供玩家選擇,這是連魔龍老虎機、忍老虎機都給不出的機台數量,為的就是讓玩家,可以隨時進入神秘的古埃及的寶藏聖域,挖掘長眠已久的神祕寶藏。
【戰神塞特老虎機】選台模式
❰戰神賽特老虎機❱ 選台模式
ATG賽特 – 購買免費遊戲挖掘秘寶
玩家們可以使用當前投注額的100倍購買免費遊戲!進入免費遊戲再也不是虛幻。獎勵與一般遊戲相同,且購買後遊戲將自動開始,直到場次和獎金發放完畢為止。
有購買免費遊戲需求的玩家們,立即點擊「開始」,啟動神秘金字塔裡的古埃及祕寶吧!
【戰神塞特老虎機】購買特色
❰戰神賽特老虎機❱ 購買特色
戰神賽特試玩推薦
看完了❰戰神賽特老虎機❱介紹之後,玩家們是否也蓄勢待發要進入古埃及的世界,一探神奇秘寶探險之旅。
本次ATG賽特與線上娛樂城推薦第一名的富遊娛樂城合作,只需要加入會員,即可領取到168體驗金,免費試玩420轉!
You made some really good points there. I checked on the internet for more information about the issue and found most people will go along with your views on this site.
Your style is so unique compared to other folks I’ve read stuff from. Many thanks for posting when you have the opportunity, Guess I will just bookmark this page.
Hi, I do think this is a great website. I stumbledupon it 😉 I may revisit yet again since I book-marked it. Money and freedom is the best way to change, may you be rich and continue to help others.
Wow, this piece of writing is pleasant, my sister is analyzing
these kinds of things, so I am going to inform her.
Hi there! This article could not be written much better! Reading through this post reminds me of my previous roommate! He always kept preaching about this. I will forward this information to him. Fairly certain he’s going to have a good read. Thanks for sharing!
I’m genuinely impressed by how effortlessly you distill intricate concepts into easily digestible information. Your writing style not only imparts knowledge but also engages the reader, making the learning experience both enjoyable and memorable. Your passion for sharing your expertise is unmistakable, and for that, I am deeply appreciative.
Your best source for free and live chat with adults in a sexually charged environment. Over the years and even more recently, s** chat usage has increased significantly. Users are in search of a platform that allows adults to gather together in one common setting. There, they can make new friends or satisfy their deepest sexual fantasies. Are you tired of the typical adult chat rooms you see on internet? Are you looking for something more unique with hundreds of people logged in at all times? Enjoy your free time here : https://bit.ly/Free-Adult-Webcams
I wanted to take a moment to express my gratitude for the wealth of valuable information you provide in your articles. Your blog has become a go-to resource for me, and I always come away with new knowledge and fresh perspectives. I’m excited to continue learning from your future posts.
Оформить заказ онлайн и [URL=http://diplom-sale.ru]купить диплом ссср[/URL] без предоплаты поможет компания http://diplom-sale.ru.
It is my belief that mesothelioma is actually the most deadly cancer. It contains unusual traits. The more I look at it the more I am assured it does not work like a real solid cells cancer. When mesothelioma is usually a rogue viral infection, therefore there is the chance for developing a vaccine and offering vaccination for asbestos open people who are at high risk of developing long term asbestos linked malignancies. Thanks for expressing your ideas on this important ailment.
I blog quite often and I truly appreciate your content. This great article has truly peaked my interest. I will take a note of your site and keep checking for new details about once per week. I opted in for your RSS feed too.
I couldn’t agree more with the insightful points you’ve made in this article. Your depth of knowledge on the subject is evident, and your unique perspective adds an invaluable layer to the discussion. This is a must-read for anyone interested in this topic.
Your dedication to sharing knowledge is unmistakable, and your writing style is captivating. Your articles are a pleasure to read, and I consistently come away feeling enriched. Thank you for being a dependable source of inspiration and information.
Your dedication to sharing knowledge is unmistakable, and your writing style is captivating. Your articles are a pleasure to read, and I consistently come away feeling enriched. Thank you for being a dependable source of inspiration and information.
modernkarachi.com
Hongzhi 황제는 고개를 끄덕이며 “내 앞에서 가져 와서 페이지별로 보여주세요. “라고 말했습니다.Hongzhi 황제는 고개를 끄덕이며 “이 단순한 드라마는 너무 강력합니다. “라고 말했습니다.
This is amazing, love the content , Thank you!
Great site you have got here.. It’s hard to find high-quality writing like yours nowadays. I really appreciate people like you! Take care!!
Your writing style effortlessly draws me in, and I find it nearly impossible to stop reading until I’ve reached the end of your articles. Your ability to make complex subjects engaging is indeed a rare gift. Thank you for sharing your expertise!
I must applaud your talent for simplifying complex topics. Your ability to convey intricate ideas in such a relatable manner is admirable. You’ve made learning enjoyable and accessible for many, and I deeply appreciate that.
This article is a real game-changer! Your practical tips and well-thought-out suggestions are incredibly valuable. I can’t wait to put them into action. Thank you for not only sharing your expertise but also making it accessible and easy to implement.
I’ve discovered a treasure trove of knowledge in your blog. Your unwavering dedication to offering trustworthy information is truly commendable. Each visit leaves me more enlightened, and I deeply appreciate your consistent reliability.
This is a topic that is near to my heart… Best wishes! Exactly where are your contact details though?
Your blog has quickly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you put into crafting each article. Your dedication to delivering high-quality content is evident, and I look forward to every new post.
Play online slots and win real money at Tuskcasino. No deposit bonus and more than 4.000 games for your entertainment. Nothing beats the excitement of online c***** slot machines and the countless options it includes. PlayLive! C***** has a limited number of banking options at the moment, with just PayPal, PlayLive Play Plus Card, and ACH e-check from you bank account as payment methods. Withdrawal methods are the same plus paper checks. We hope that they might add some other deposit methods in the near future, like cash at the c***** cage, bank transfer, or debit cards, but for now you must make due with these fast c***** payment options. You can choose your preferred payment method and deposit limits as you deposit funds. PlayLive! is offering up to a 125% first-deposit match bonus (worth up to $500!). This online real money c***** also offers a no-deposit bonus (that’s worth a little less than the deposit-match bonus but is still worth using).
https://wiki-byte.win/index.php?title=Bitcoin_poker_android_app
A no deposit bonus requires players to play eligible games and make bets with the bonus funds in order to meet the wagering requirements. You must know that some casinos require you to wager a no deposit bonus using real funds, so you will need to make a deposit to wager the bonus. Considering the t******************* of the bonus is highly recommended, since they provide clear information regarding the eligible games, contribution percentages, and any time limits imposed on the no deposit bonus. Unlock a generous $25 no deposit bonus at BetMGM C***** with the exclusive promo code: ATSSPINS. Simply enter this code upon registration to enjoy the free bonus. For those interested in further play, the same code grants a 100% match on your first deposit, up to $1,000, to enhance your gaming experience. Secure your bonus today and start playing at BetMGM C*****.
I wanted to take a moment to express my gratitude for the wealth of invaluable information you consistently provide in your articles. Your blog has become my go-to resource, and I consistently emerge with new knowledge and fresh perspectives. I’m eagerly looking forward to continuing my learning journey through your future posts.
Your blog has rapidly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you invest in crafting each article. Your dedication to delivering high-quality content is apparent, and I eagerly await every new post.
agonaga.com
Hongzhi 황제는 “당신은 그것을 읽을 필요가 없습니다. 저는 Xu Qing의 가족을 믿습니다. “라고 웃었습니다.
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
Your storytelling prowess is nothing short of extraordinary. Reading this article felt like embarking on an adventure of its own. The vivid descriptions and engaging narrative transported me, and I eagerly await to see where your next story takes us. Thank you for sharing your experiences in such a captivating manner.
May I simply just say what a comfort to discover someone who truly knows what they’re talking about over the internet. You definitely know how to bring a problem to light and make it important. A lot more people have to read this and understand this side of your story. It’s surprising you are not more popular given that you definitely have the gift.
This article resonated with me on a personal level. Your ability to connect with your audience emotionally is commendable. Your words are not only informative but also heartwarming. Thank you for sharing your insights.
I seriously love your site.. Very nice colors & theme. Did you build this web site yourself? Please reply back as I’m wanting to create my own personal blog and want to learn where you got this from or just what the theme is named. Cheers.
Wonderful post! We are linking to this great article on our website. Keep up the good writing.
I’m impressed, I must say. Rarely do I come across a blog that’s both educative and engaging, and let me tell you, you’ve hit the nail on the head. The issue is something which not enough men and women are speaking intelligently about. Now i’m very happy that I found this in my hunt for something regarding this.
кракен kraken kraken darknet top
Темная сторона интернета, это, анонимную, платформу, на, сети, подключение к этой сети, получается, через, специальные, программы плюс, технологии, предоставляющие, невидимость пользовательские данных. Из числа, этих, средств, представляется, Тор браузер, который позволяет, обеспечивает защиту, приватное, подключение к сети, к сети Даркнет. С, его же, пользователи, имеют шанс, безопасно, посещать, веб-сайты, не индексируемые, традиционными, поисками, что делает возможным, обстановку, для проведения, различных, противоправных активностей.
Крупнейшая торговая площадка, соответственно, часто упоминается в контексте, темной стороной интернета, как, площадка, для, киберугрозами. На этой площадке, можно, купить, разнообразные, непозволительные, услуги, начиная от, препаратов и огнестрельного оружия, заканчивая, хакерскими услугами. Система, предоставляет, высокую степень, криптографической защиты, и, защиты личной информации, что, делает, ее, желанной, для тех, кто, намерен, предотвратить, преследований, со стороны законопослушных органов.
I’ve discovered a treasure trove of knowledge in your blog. Your unwavering dedication to offering trustworthy information is truly commendable. Each visit leaves me more enlightened, and I deeply appreciate your consistent reliability.
I must applaud your talent for simplifying complex topics. Your ability to convey intricate ideas in such a relatable manner is admirable. You’ve made learning enjoyable and accessible for many, and I deeply appreciate that.
Your passion and dedication to your craft radiate through every article. Your positive energy is infectious, and it’s evident that you genuinely care about your readers’ experience. Your blog brightens my day!
I simply wanted to convey how much I’ve gleaned from this article. Your meticulous research and clear explanations make the information accessible to all readers. It’s abundantly clear that you’re committed to providing valuable content.
This article resonated with me on a personal level. Your ability to emotionally connect with your audience is truly commendable. Your words are not only informative but also heartwarming. Thank you for sharing your insights.
I’m impressed, I have to admit. Rarely do I encounter a blog that’s both equally educative and entertaining, and without a doubt, you’ve hit the nail on the head. The problem is something not enough folks are speaking intelligently about. I’m very happy that I stumbled across this during my hunt for something concerning this.
Today is a reminder to find joy in the little things, and your post is a perfect example of that.
I’m truly impressed by the way you effortlessly distill intricate concepts into easily digestible information. Your writing style not only imparts knowledge but also engages the reader, making the learning experience both enjoyable and memorable. Your passion for sharing your expertise is unmistakable, and for that, I am deeply grateful.
I’ve discovered a treasure trove of knowledge in your blog. Your unwavering dedication to offering trustworthy information is truly commendable. Each visit leaves me more enlightened, and I deeply appreciate your consistent reliability.
restaurant-lenvol.net
원제(文帝)의 군대가 안난(安南)에 들어갔을 때 그들은 지쳐 죽을 지경이었다.
Great information. Lucky me I came across your site by accident (stumbleupon). I have bookmarked it for later.
The globally famous G******* Commission is responsible for monitoring and regulating top online casinos in the UK. Adherence to UK g******* laws and regulations is their primary focal point. The UKGC makes sure that the best online poker sites UK operate legally and pay out regularly. But, how do you pick top online UK casinos? This is where BestCasinos can help. The UK G******* Commission oversees most aspects of land-based and online g******* in the United Kingdom. The commissioner regulates land casinos, online and mobile casinos, sportsbooks, bet exchanges, and Internet poker sites. Non-c***** gaming like bingo is also regulated by the G******* Commission. All of the best EU casinos that accept UK players hold a valid UK G******* Commission (UKGC) licence. The following are our recommended EU casinos online for British players: C***** Planet, LeoVegas, CasinoLuck and Casumo. You’ll find many excellent top casinos online on this page which legally accept players from the United Kingdom.
https://affinity-space.com/community/profile/6890cdlviii1874/
You’ve read everything there is to know on online g******* with Siru Mobile, so now it’s time to join our #1 c***** that supports the payment method. This Siru c***** has been chosen by our experts for its excellent security measures, top games lobby, and generous c***** bonuses. Join today to claim your welcome package! Käyttöä koskevat tietyt rajoitukset: maksimissaan Siru Mobilen kautta voi tehdä talletuksia 300 euron edestä kuukautta kohden. Kotiutuksia Siru Mobile ei valitettavasti mahdollista lainkaan, mutta Siru Mobile c***** tarjoaa tätä varten muita, turvallisia maksuvälineitä. Talletuksissa Siru Mobile on kuitenkin mitä kätevin maksuväline. The main goal of Siru was to streamline transactions made on mobile phones. Therefore, it is a given that deposits via Siru are made easy at mobile-optimised pay by phone c***** sites. Check out our list of the best mobile casinos to find your favourite!
Hi! I could have sworn I’ve been to your blog before but after looking at many of the posts I realized it’s new to me. Regardless, I’m definitely delighted I stumbled upon it and I’ll be bookmarking it and checking back frequently!
It’s nearly impossible to find educated people on this topic, however, you sound like you know what you’re talking about! Thanks
Attractive element of content. I just stumbled upon your web site and in accession capital to assert that I get actually enjoyed account your blog posts. Anyway I will be subscribing for your augment or even I fulfillment you access persistently rapidly.
Your unique approach to addressing challenging subjects is like a breath of fresh air. Your articles stand out with their clarity and grace, making them a pure joy to read. Your blog has now become my go-to source for insightful content.
I was more than happy to discover this web site. I want to to thank you for ones time due to this fantastic read!! I definitely savored every bit of it and i also have you book-marked to check out new things in your blog.
Your passion and dedication to your craft radiate through every article. Your positive energy is infectious, and it’s evident that you genuinely care about your readers’ experience. Your blog brightens my day!
Your enthusiasm for the subject matter shines through every word of this article; it’s infectious! Your commitment to delivering valuable insights is greatly valued, and I eagerly anticipate more of your captivating content. Keep up the exceptional work!
Your enthusiasm for the subject matter radiates through every word of this article; it’s contagious! Your commitment to delivering valuable insights is greatly valued, and I eagerly anticipate more of your captivating content. Keep up the exceptional work!
This article resonated with me on a personal level. Your ability to emotionally connect with your audience is truly commendable. Your words are not only informative but also heartwarming. Thank you for sharing your insights.
Your style is really unique in comparison to other folks I’ve read stuff from. I appreciate you for posting when you have the opportunity, Guess I will just bookmark this web site.
After I initially commented I appear to have clicked the -Notify me when new comments are added- checkbox and now every time a comment is added I get 4 emails with the exact same comment. Is there a way you are able to remove me from that service? Cheers.
2024全新上線❰戰神賽特老虎機❱ – ATG賽特玩法說明介紹
❰戰神賽特老虎機❱是由ATG電子獨家開發的古埃及風格線上老虎機,在傳說中戰神賽特是「力量之神」與奈芙蒂斯女神結成連理,共同守護古埃及的奇幻秘寶,只有被選中的冒險者才能進入探險。
❰戰神賽特老虎機❱ – ATG賽特介紹
2024最新老虎機【戰神塞特】- ATG電子 X 富遊娛樂城
❰戰神賽特老虎機❱ – ATG電子
線上老虎機系統 : ATG電子
發行年分 : 2024年1月
最大倍數 : 51000倍
返還率 : 95.89%
支付方式 : 全盤倍數、消除掉落
最低投注金額 : 0.4元
最高投注金額 : 2000元
可否選台 : 是
可選台台數 : 350台
免費遊戲 : 選轉觸發+購買特色
❰戰神賽特老虎機❱ 賠率說明
戰神塞特老虎機賠率算法非常簡單,玩家們只需要不斷的轉動老虎機,成功消除物件即可贏分,得分賠率依賠率表計算。
當盤面上沒有物件可以消除時,倍數符號將會相加形成總倍數!該次旋轉的總贏分即為 : 贏分 X 總倍數。
積分方式如下 :
贏分=(單次押注額/20) X 物件賠率
EX : 單次押注額為1,盤面獲得12個戰神賽特倍數符號法老魔眼
贏分= (1/20) X 1000=50
以下為各個得分符號數量之獎金賠率 :
得分符號 獎金倍數 得分符號 獎金倍數
戰神賽特倍數符號聖甲蟲 6 2000
5 100
4 60 戰神賽特倍數符號黃寶石 12+ 200
10-11 30
8-9 20
戰神賽特倍數符號荷魯斯之眼 12+ 1000
10-11 500
8-9 200 戰神賽特倍數符號紅寶石 12+ 160
10-11 24
8-9 16
戰神賽特倍數符號眼鏡蛇 12+ 500
10-11 200
8-9 50 戰神賽特倍數符號紫鑽石 12+ 100
10-11 20
8-9 10
戰神賽特倍數符號神箭 12+ 300
10-11 100
8-9 40 戰神賽特倍數符號藍寶石 12+ 80
10-11 18
8-9 8
戰神賽特倍數符號屠鐮刀 12+ 240
10-11 40
8-9 30 戰神賽特倍數符號綠寶石 12+ 40
10-11 15
8-9 5
❰戰神賽特老虎機❱ 賠率說明(橘色數值為獲得數量、黑色數值為得分賠率)
ATG賽特 – 特色說明
ATG賽特 – 倍數符號獎金加乘
玩家們在看到盤面上出現倍數符號時,務必把握機會加速轉動ATG賽特老虎機,倍數符號會隨機出現2到500倍的隨機倍數。
當盤面無法在消除時,這些倍數總和會相加,乘上當時累積之獎金,即為最後得分總額。
倍數符號會出現在主遊戲和免費遊戲當中,玩家們千萬別錯過這個可以瞬間將得獎金額拉高的好機會!
ATG賽特 – 倍數符號獎金加乘
ATG賽特 – 倍數符號圖示
ATG賽特 – 進入神秘金字塔開啟免費遊戲
戰神賽特倍數符號聖甲蟲
❰戰神賽特老虎機❱ 免費遊戲符號
在古埃及神話中,聖甲蟲又稱為「死亡之蟲」,它被當成了天球及重生的象徵,守護古埃及的奇幻秘寶。
當玩家在盤面上,看見越來越多的聖甲蟲時,千萬不要膽怯,只需在牌面上斬殺4~6個ATG賽特免費遊戲符號,就可以進入15場免費遊戲!
在免費遊戲中若轉出3~6個聖甲蟲免費遊戲符號,可額外獲得5次免費遊戲,最高可達100次。
當玩家的累積贏分且盤面有倍數物件時,盤面上的所有倍數將會加入總倍數!
ATG賽特 – 選台模式贏在起跑線
為避免神聖的寶物被盜墓者奪走,富有智慧的法老王將金子塔內佈滿迷宮,有的設滿機關讓盜墓者寸步難行,有的暗藏機關可以直接前往存放神秘寶物的暗房。
ATG賽特老虎機設有350個機檯供玩家選擇,這是連魔龍老虎機、忍老虎機都給不出的機台數量,為的就是讓玩家,可以隨時進入神秘的古埃及的寶藏聖域,挖掘長眠已久的神祕寶藏。
【戰神塞特老虎機】選台模式
❰戰神賽特老虎機❱ 選台模式
ATG賽特 – 購買免費遊戲挖掘秘寶
玩家們可以使用當前投注額的100倍購買免費遊戲!進入免費遊戲再也不是虛幻。獎勵與一般遊戲相同,且購買後遊戲將自動開始,直到場次和獎金發放完畢為止。
有購買免費遊戲需求的玩家們,立即點擊「開始」,啟動神秘金字塔裡的古埃及祕寶吧!
【戰神塞特老虎機】購買特色
❰戰神賽特老虎機❱ 購買特色
This site definitely has all of the information and facts I wanted concerning this subject and didn’t know who to ask.
Do you mind if I q**** a few of your posts as long as I provide credit
and sources back to your blog? My website is in the exact same niche as yours and my
visitors would really benefit from some of the information you provide here.
Please let me know if this okay with you.
Regards!
I love it whenever people get together and share opinions. Great site, stick with it.
There’s certainly a lot to learn about this subject. I love all of the points you have made.
I want to express my sincere appreciation for this enlightening article. Your unique perspective and well-researched content bring a fresh depth to the subject matter. It’s evident that you’ve invested considerable thought into this, and your ability to convey complex ideas in such a clear and understandable way is truly commendable. Thank you for generously sharing your knowledge and making the learning process enjoyable.
I’m more than happy to uncover this website. I need to to thank you for ones time for this fantastic read!! I definitely loved every part of it and I have you saved to fav to look at new stuff in your website.
Your storytelling prowess is nothing short of extraordinary. Reading this article felt like embarking on an adventure of its own. The vivid descriptions and engaging narrative transported me, and I eagerly await to see where your next story takes us. Thank you for sharing your experiences in such a captivating manner.
An interesting discussion is worth comment. I do think that you should publish more on this subject matter, it might not be a taboo matter but typically people don’t speak about these topics. To the next! Many thanks!
Даркнет сайты
Темная сторона интернета – скрытая зона всемирной паутины, избегающая взоров обыденных поисковых систем и требующая специальных средств для доступа. Этот несканируемый уголок сети обильно насыщен сайтами, предоставляя доступ к разнообразным товарам и услугам через свои даркнет списки и каталоги. Давайте ближе рассмотрим, что представляют собой эти реестры и какие тайны они сокрывают.
Даркнет Списки: Ворота в Скрытый Мир
Индексы веб-ресурсов в темной части интернета – это своего рода порталы в невидимый мир интернета. Каталоги и индексы веб-ресурсов в даркнете, они позволяют пользователям отыскивать разнообразные услуги, товары и информацию. Варьируя от форумов и магазинов до ресурсов, уделяющих внимание аспектам анонимности и криптовалютам, эти списки предоставляют нам возможность заглянуть в таинственный мир даркнета.
Категории и Возможности
Теневой Рынок:
Даркнет часто связывается с незаконными сделками, где доступны разнообразные товары и услуги – от наркотиков и оружия до краденых данных и услуг наемных убийц. Списки ресурсов в подобной категории облегчают пользователям находить нужные предложения без лишних усилий.
Форумы и Сообщества:
Даркнет также предоставляет площадку для анонимного общения. Форумы и сообщества, представленные в реестрах даркнета, затрагивают различные темы – от информационной безопасности и взлома до политических вопросов и философских идей.
Информационные Ресурсы:
На даркнете есть ресурсы, предоставляющие данные и указания по обходу цензуры, защите конфиденциальности и другим темам, интересным тем, кто хочет сохранить свою конфиденциальность.
Безопасность и Осторожность
Несмотря на неизвестность и свободу, даркнет не лишен рисков. Мошенничество, кибератаки и незаконные сделки присущи этому миру. Взаимодействуя с реестрами даркнета, пользователи должны соблюдать высший уровень бдительности и придерживаться мер безопасности.
Заключение
Реестры даркнета – это врата в неизведанный мир, где сокрыты тайны и возможности. Однако, как и в любой неизведанной территории, путешествие в темную сеть требует особой внимания и знаний. Не всегда можно полагаться на анонимность, и использование даркнета требует осмысленного подхода. Независимо от ваших интересов – будь то технические детали в области кибербезопасности, поиск необычных товаров или исследование новых возможностей в интернете – реестры даркнета предоставляют ключ
lfchungary.com
강빈은 배를 차고 노란 물을 뱉었다.
st666
В последнее период стали известными запросы о заливах без предоплат – предложениях, предоставляемых в интернете, где клиентам обещают осуществление задачи или предоставление товара перед оплаты. Впрочем, за данной привлекающей внимание возможностью могут скрываться значительные опасности и негативные следствия.
Привлекательность безоплатных заливов:
Привлекательность концепции переводов без предварительной оплаты заключается в том, что заказчики приобретают сервис или продукцию, не выплачивая первоначально деньги. Данное условие может показаться прибыльным и удобным, особенно для тех, кто избегает ставить под риск финансами или остаться обманутым. Тем не менее, прежде чем вовлечься в сферу безоплатных переводов, следует принять во внимание ряд существенных аспектов.
Риски и негативные следствия:
Обман и обман:
За честными предложениями без предварительной оплаты скрываются мошеннические схемы, готовые использовать уважение потребителей. Попав в их ловушку, вы можете потерять не только это, услуги финансов.
Низкое качество выполнения работ:
Без обеспечения оплаты исполнителю может быть недостаточно стимула оказать высококачественную услугу или продукт. В результате клиент останется недовольным, а поставщик услуг не подвергнется серьезными санкциями.
Утрата информации и защиты:
При передаче персональных данных или информации о банковских счетах для безоплатных заливов существует опасность утечки информации и последующего их неправомерного использования.
Советы по надежным заливам:
Поиск информации:
До подбором бесплатных заливов проведите комплексное исследование исполнителя. Мнения, рейтинговые оценки и популярность могут хорошим критерием.
Оплата вперед:
По возможности, старайтесь согласовать часть оплаты заранее. Это способен сделать соглашение более безопасной и обеспечит вам больший управления.
Достоверные платформы:
Отдавайте предпочтение использованию надежных платформ и сервисов для переводов. Это уменьшит опасность обмана и повысит вероятность на получение наилучших качественных услуг.
Заключение:
Несмотря на видимую привлекательность, безвозмездные переводы без предварительной оплаты сопряжены опасности и угрозы. Внимание и осмотрительность при выборе исполнителя или площадки способны предупредить нежелательные последствия. Существенно помнить, что безоплатные заливы могут стать причиной проблем, и разумное принятие решений способствует предотвратить возможных неприятностей
pragmatic-ko.com
“급한 일입니다. 황제에게 보고하러 왔습니다.” 젊은 스승이 말했다.
This article is a true game-changer! Your practical tips and well-thought-out suggestions hold incredible value. I’m eagerly anticipating implementing them. Thank you not only for sharing your expertise but also for making it accessible and easy to apply.
Your storytelling prowess is nothing short of extraordinary. Reading this article felt like embarking on an adventure of its own. The vivid descriptions and engaging narrative transported me, and I eagerly await to see where your next story takes us. Thank you for sharing your experiences in such a captivating manner.
sm-slot.com
귀주(貴州)의 총사령관, 귀주(貴州)의 총사령관, 진의위(晉實威) 천호의 관리.
взлом whatsapp
Взлом Вотсап: Реальность и Легенды
WhatsApp – один из известных мессенджеров в мире, широко используемый для обмена сообщениями и файлами. Он прославился своей шифрованной системой обмена данными и обеспечением конфиденциальности пользователей. Однако в интернете время от времени появляются утверждения о возможности нарушения Вотсап. Давайте разберемся, насколько эти утверждения соответствуют фактичности и почему тема взлома WhatsApp вызывает столько дискуссий.
Шифрование в Вотсап: Защита Личной Информации
WhatsApp применяет точка-точка кодирование, что означает, что только отправитель и получатель могут понимать сообщения. Это стало основой для доверия многих пользователей мессенджера к сохранению их личной информации.
Мифы о Нарушении Вотсап: По какой причине Они Появляются?
Сеть периодически заполняют слухи о нарушении Вотсап и возможном доступе к переписке. Многие из этих утверждений часто не имеют оснований и могут быть результатом паники или дезинформации.
Фактические Угрозы: Кибератаки и Безопасность
Хотя взлом Вотсап является трудной задачей, существуют реальные угрозы, такие как кибератаки на отдельные аккаунты, фишинг и вредоносные программы. Исполнение мер охраны важно для минимизации этих рисков.
Охрана Личной Информации: Советы Пользователям
Для укрепления охраны своего аккаунта в Вотсап пользователи могут использовать двухэтапную проверку, регулярно обновлять приложение, избегать сомнительных ссылок и следить за конфиденциальностью своего устройства.
Итог: Реальность и Осторожность
Взлом Вотсап, как обычно, оказывается сложным и маловероятным сценарием. Однако важно помнить о актуальных угрозах и принимать меры предосторожности для сохранения своей личной информации. Исполнение рекомендаций по безопасности помогает поддерживать конфиденциальность и уверенность в использовании мессенджера.
pchelografiya.com
예를 들어, 이 전월 대비 2월은 1월에 비해 1.25% 증가했습니다.
pragmatic-ko.com
내가 어찌 감히 천주님과 나란히 섰느냐 하는 것은 주군을 속이고 조상을 멸망시키는 일이다.
I want to express my sincere appreciation for this enlightening article. Your unique perspective and well-researched content bring a fresh depth to the subject matter. It’s evident that you’ve invested considerable thought into this, and your ability to convey complex ideas in such a clear and understandable way is truly commendable. Thank you for generously sharing your knowledge and making the learning process enjoyable.
I’m genuinely impressed by how effortlessly you distill intricate concepts into easily digestible information. Your writing style not only imparts knowledge but also engages the reader, making the learning experience both enjoyable and memorable. Your passion for sharing your expertise is unmistakable, and for that, I am deeply appreciative.
I recently tried Organic Body Essentials https://organicbodyessentials.com/blogs/cbd-blog/does-cbd-show-up-on-a-drug-test and was pleasantly surprised. Their CBD oil provided intelligent contrast instead of my anxiety without any palpable side effects. The flavor was kind and not overpowering. Additionally, their bloke waiting was excellent, addressing my queries promptly. Overall, I effectively recommend Organic Body Essentials CBD fit anyone seeking high-quality CBD products.
After going over a number of the blog posts on your blog, I truly appreciate your technique of blogging. I saved it to my bookmark website list and will be checking back in the near future. Please visit my web site too and let me know how you feel.
lfchungary.com
그러자 다리가 부러지는 것을 두려워한 류문산과 장첸이 직접 끌고 갔다.
Crypto Payment Gateway Development Company 2024
I enjoy looking through an article that will make people think. Also, thank you for permitting me to comment.
yangsfitness.com
반 아들은 고사하고 개를 때리는 것은 주인에게 달려 있습니다.
I blog quite often and I really thank you for your information. This great article has really peaked my interest. I am going to bookmark your site and keep checking for new information about once per week. I opted in for your Feed too.
The information shared is of top quality which has to get appreciated at all levels. Well done…
An outstanding share! I’ve just forwarded this onto a coworker who had been conducting a little research on this. And he actually bought me lunch because I stumbled upon it for him… lol. So let me reword this…. Thanks for the meal!! But yeah, thanx for spending some time to talk about this matter here on your blog.
Умение осмысливать сущности и опасностей ассоциированных с обналом кредитных карт может помочь людям предотвращать атак и обеспечивать защиту свои финансовые ресурсы. Обнал (отмывание) кредитных карт — это процесс использования украденных или неправомерно приобретенных кредитных карт для осуществления финансовых транзакций с целью скрыть их происхождение и заблокировать отслеживание.
Вот несколько способов, которые могут содействовать в избежании обнала кредитных карт:
Защита личной информации: Будьте осторожными в отношении предоставления личной информации, особенно онлайн. Избегайте предоставления картовых номеров, кодов безопасности и других конфиденциальных данных на непроверенных сайтах.
Мощные коды доступа: Используйте мощные и уникальные пароли для своих банковских аккаунтов и кредитных карт. Регулярно изменяйте пароли.
Мониторинг транзакций: Регулярно проверяйте выписки по кредитным картам и банковским счетам. Это способствует своевременному выявлению подозрительных транзакций.
Защита от вирусов: Используйте антивирусное программное обеспечение и вносите обновления его регулярно. Это поможет защитить от вредоносные программы, которые могут быть использованы для кражи данных.
Осмотрительное поведение в социальных медиа: Будьте осторожными в социальных сетях, избегайте публикации чувствительной информации, которая может быть использована для взлома вашего аккаунта.
Быстрое сообщение банку: Если вы заметили какие-либо подозрительные операции или утерю карты, сразу свяжитесь с вашим банком для отключения карты.
Получение знаний: Будьте внимательными к современным приемам мошенничества и обучайтесь тому, как предотвращать их.
Избегая легковерия и проявляя предельную осторожность, вы можете уменьшить риск стать жертвой обнала кредитных карт.
st666
ST666️ – Trang Chủ Chính Thức Số 1️⃣ Của Nhà Cái ST666
ST666 đã nhanh chóng trở thành điểm đến giải trí cá độ thể thao được yêu thích nhất hiện nay. Mặc dù chúng tôi mới xuất hiện trên thị trường cá cược trực tuyến Việt Nam gần đây, nhưng đã nhanh chóng thu hút sự quan tâm của cộng đồng người chơi trực tuyến. Đối với những người yêu thích trò chơi trực tuyến, nhà cái ST666 nhận được sự tin tưởng và tín nhiệm trọn vẹn từ họ. ST666 được coi là thiên đường cho những người chơi tham gia.
Giới Thiệu Nhà Cái ST666
ST666.BLUE – ST666 là nơi cá cược đổi thưởng trực tuyến được ưa chuộng nhất hiện nay. Tham gia vào trò chơi cá cược trực tuyến, người chơi không chỉ trải nghiệm các trò giải trí hấp dẫn mà còn có cơ hội nhận các phần quà khủng thông qua các kèo cá độ. Với những phần thưởng lớn, người chơi có thể thay đổi cuộc sống của mình.
Giới Thiệu Nhà Cái ST666 BLUE
Thông tin về nhà cái ST666
ST666 là Gì?
Nhà cái ST666 là một sân chơi cá cược đổi thưởng trực tuyến, chuyên cung cấp các trò chơi cá cược đổi thưởng có thưởng tiền mặt. Điều này bao gồm các sản phẩm như c*****, bắn cá, thể thao, esports… Người chơi có thể tham gia nhiều trò chơi hấp dẫn khi đăng ký, đặt cược và có cơ hội nhận thưởng lớn nếu chiến thắng hoặc mất số tiền cược nếu thất bại.
Nhà Cái ST666 – Sân Chơi Cá Cược An Toàn
Nhà Cái ST666 – Sân Chơi Cá Cược Trực Tuyến
Nguồn Gốc Thành Lập Nhà Cái ST666
Nhà cái ST666 được thành lập và ra mắt vào năm 2020 tại Campuchia, một quốc gia nổi tiếng với các tập đoàn giải trí cá cược đổi thưởng. Xuất hiện trong giai đoạn phát triển mạnh mẽ của ngành cá cược, ST666 đã để lại nhiều dấu ấn. Được bảo trợ tài chính bởi tập đoàn danh tiếng Venus C*****, thương hiệu đã mở rộng hoạt động khắp Đông Nam Á và lan tỏa sang cả các quốc gia Châu Á, bao gồm cả Trung Quốc
[url=https://baimless.com/forums/topic/19676-sports/]sports[/url] 4956d02
купить фальшивые рубли
Фальшивые рубли, в большинстве случаев, подделывают с целью мошенничества и незаконного обогащения. Шулеры занимаются клонированием российских рублей, создавая поддельные банкноты различных номиналов. В основном, воспроизводят банкноты с более высокими номиналами, вроде 1 000 и 5 000 рублей, поскольку это позволяет им зарабатывать крупные суммы при уменьшенном числе фальшивых денег.
Процесс фальсификации рублей включает в себя применение высокотехнологичного оборудования, специализированных печатающих устройств и специально подготовленных материалов. Преступники стремятся наиболее точно воспроизвести средства защиты, водяные знаки, металлическую защиту, микроскопический текст и другие характеристики, чтобы затруднить определение поддельных купюр.
Поддельные денежные средства часто попадают в обращение через торговые площадки, банки или прочие учреждения, где они могут быть легко спрятаны среди реальных денежных средств. Это порождает серьезные затруднения для экономической системы, так как фальшивые деньги могут порождать потерям как для банков, так и для населения.
Необходимо подчеркнуть, что имение и применение поддельных средств являются уголовными преступлениями и могут быть наказаны в соответствии с законодательством Российской Федерации. Власти энергично противостоят с такими преступлениями, предпринимая меры по выявлению и пресечению деятельности банд преступников, вовлеченных в подделкой российских рублей
sm-online-game.com
이때 주후조는 “그럼 내 아들은 은퇴하겠다”고 말했다.
Hi! I could have sworn I’ve visited this web site before but after browsing through many of the articles I realized it’s new to me. Anyhow, I’m definitely happy I came across it and I’ll be book-marking it and checking back regularly.
A great post without any doubt.
rikvip
Oh my goodness! Impressive article dude! Thank you, However I am going through troubles with your RSS. I don’t understand why I can’t subscribe to it. Is there anybody else getting similar RSS problems? Anyone that knows the answer can you kindly respond? Thanx!
I gave cbd products a prove with a view the maiden time, and I’m amazed! They tasted smashing and provided a sense of calmness and relaxation. My lay stress melted away, and I slept well-advised too. These gummies are a game-changer on the side of me, and I extremely put forward them to anyone seeking unconstrained worry alleviation and well-advised sleep.
hoki1881permainan
You ought to take part in a contest for one of the best sites online. I most certainly will highly recommend this website!
KANTORBOLA situs gamin online terbaik 2024 yang menyediakan beragam permainan judi online easy to win , mulai dari permainan slot online , taruhan judi bola , taruhan live c***** , dan toto macau . Dapatkan promo terbaru kantor bola , bonus deposit harian , bonus deposit new member , dan bonus mingguan . Kunjungi link kantorbola untuk melakukan pendaftaran .
smcasino-game.com
Zhu Zaimo는 엄숙하게 절했습니다. “학생 여러분, 선생님에게 실망하라고 가르치지 마십시오.”
🌎 Others are joining the chorus of admiration for the author’s outstanding writing.
Saved as a favorite, I love your website!
Your words have the power to uplift and inspire. Thank you for sharing your light with the world.
Scrap Copper recovery Expanded copper recycling Scrap metal recycling center
Copper cable recycling news, Metal scrap management, Recycling scrap Copper wire
Your kindness is evident in every word you write. Thank you for spreading positivity.
Your post reminded me that it’s okay to not be okay sometimes. Thank you for your honesty.
Your post reminded me that I am stronger than I think. Thank you for your encouragement.
Link Alternatif Ngamenjitu
Portal Judi: Situs Lotere Online Terbesar dan Terjamin
Ngamenjitu telah menjadi salah satu situs judi daring terluas dan terpercaya di Indonesia. Dengan bervariasi pasaran yang disediakan dari Semar Group, Portal Judi menawarkan pengalaman bermain togel yang tak tertandingi kepada para penggemar judi daring.
Market Terbaik dan Terpenuhi
Dengan total 56 pasaran, Portal Judi menampilkan beberapa opsi terbaik dari market togel di seluruh dunia. Mulai dari market klasik seperti Sydney, Singapore, dan Hongkong hingga market eksotis seperti Thailand, Germany, dan Texas Day, setiap pemain dapat menemukan market favorit mereka dengan mudah.
Cara Main yang Mudah
Situs Judi menyediakan tutorial cara main yang sederhana dipahami bagi para pemula maupun penggemar togel berpengalaman. Dari langkah-langkah pendaftaran hingga penarikan kemenangan, semua informasi tersedia dengan jelas di situs Ngamenjitu.
Hasil Terakhir dan Info Terkini
Pemain dapat mengakses hasil terakhir dari setiap pasaran secara real-time di Ngamenjitu. Selain itu, informasi paling baru seperti jadwal bank online, gangguan, dan offline juga disediakan untuk memastikan kelancaran proses transaksi.
Berbagai Jenis Permainan
Selain togel, Portal Judi juga menawarkan bervariasi jenis permainan kasino dan judi lainnya. Dari bingo hingga roulette, dari dragon tiger hingga baccarat, setiap pemain dapat menikmati bervariasi pilihan permainan yang menarik dan menghibur.
Security dan Kenyamanan Pelanggan Dijamin
Ngamenjitu mengutamakan keamanan dan kepuasan pelanggan. Dengan sistem keamanan terbaru dan layanan pelanggan yang responsif, setiap pemain dapat bermain dengan nyaman dan tenang di platform ini.
Promosi-Promosi dan Bonus Menarik
Portal Judi juga menawarkan bervariasi promosi dan hadiah istimewa bagi para pemain setia maupun yang baru bergabung. Dari bonus deposit hingga bonus referral, setiap pemain memiliki kesempatan untuk meningkatkan kemenangan mereka dengan bonus yang ditawarkan.
Dengan semua fitur dan layanan yang ditawarkan, Ngamenjitu tetap menjadi pilihan utama bagi para penggemar judi online di Indonesia. Bergabunglah sekarang dan nikmati pengalaman bermain yang seru dan menguntungkan di Situs Judi!
Thank you for sharing indeed great looking !
Greetings! Very useful advice in this particular post! It is the little changes that will make the greatest changes. Thanks for sharing!
Thank you so much for sharing this wonderful post with us.
Portal Judi: Situs Lotere Online Terbesar dan Terjamin
Portal Judi telah menjadi salah satu portal judi online terbesar dan terpercaya di Indonesia. Dengan bervariasi market yang disediakan dari Grup Semar, Ngamenjitu menawarkan sensasi bermain togel yang tak tertandingi kepada para penggemar judi daring.
Pasaran Terunggul dan Terpenuhi
Dengan total 56 pasaran, Situs Judi menampilkan beberapa opsi terunggul dari pasaran togel di seluruh dunia. Mulai dari market klasik seperti Sydney, Singapore, dan Hongkong hingga market eksotis seperti Thailand, Germany, dan Texas Day, setiap pemain dapat menemukan pasaran favorit mereka dengan mudah.
Metode Bermain yang Sederhana
Portal Judi menyediakan tutorial cara bermain yang sederhana dipahami bagi para pemula maupun penggemar togel berpengalaman. Dari langkah-langkah pendaftaran hingga penarikan kemenangan, semua informasi tersedia dengan jelas di situs Portal Judi.
Ringkasan Terakhir dan Informasi Paling Baru
Pemain dapat mengakses hasil terakhir dari setiap pasaran secara real-time di Portal Judi. Selain itu, info terkini seperti jadwal bank daring, gangguan, dan offline juga disediakan untuk memastikan kelancaran proses transaksi.
Berbagai Jenis Game
Selain togel, Portal Judi juga menawarkan berbagai jenis permainan kasino dan judi lainnya. Dari bingo hingga roulette, dari dragon tiger hingga baccarat, setiap pemain dapat menikmati bervariasi pilihan permainan yang menarik dan menghibur.
Security dan Kepuasan Pelanggan Terjamin
Portal Judi mengutamakan security dan kepuasan pelanggan. Dengan sistem keamanan terbaru dan layanan pelanggan yang responsif, setiap pemain dapat bermain dengan nyaman dan tenang di platform ini.
Promosi-Promosi dan Bonus Istimewa
Portal Judi juga menawarkan berbagai promosi dan hadiah menarik bagi para pemain setia maupun yang baru bergabung. Dari hadiah deposit hingga bonus referral, setiap pemain memiliki kesempatan untuk meningkatkan kemenangan mereka dengan hadiah yang ditawarkan.
Dengan semua fitur dan pelayanan yang ditawarkan, Situs Judi tetap menjadi pilihan utama bagi para penggemar judi online di Indonesia. Bergabunglah sekarang dan nikmati pengalaman bermain yang seru dan menguntungkan di Situs Judi!
I really like it when people get together and share views. Great website, continue the good work.
Great info. Lucky me I discovered your website by accident (stumbleupon). I’ve saved it for later.
crazyslot1.com
이 불가피한 단어는 항상 그들의 눈에 나타납니다.
Понимание сущности и опасностей связанных с обналом кредитных карт может помочь людям избегать подобных атак и обеспечивать защиту свои финансовые ресурсы. Обнал (отмывание) кредитных карт — это процедура использования украденных или нелегально добытых кредитных карт для осуществления финансовых транзакций с целью скрыть их происхождения и пресечь отслеживание.
Вот несколько способов, которые могут содействовать в предотвращении обнала кредитных карт:
Сохранение личной информации: Будьте осторожными в контексте предоставления персональной информации, особенно онлайн. Избегайте предоставления банковских карт, кодов безопасности и дополнительных конфиденциальных данных на ненадежных сайтах.
Сильные пароли: Используйте надежные и уникальные пароли для своих банковских аккаунтов и кредитных карт. Регулярно изменяйте пароли.
Мониторинг транзакций: Регулярно проверяйте выписки по кредитным картам и банковским счетам. Это позволит своевременно обнаруживать подозрительных транзакций.
Антивирусная защита: Используйте антивирусное программное обеспечение и актуализируйте его регулярно. Это поможет защитить от вредоносные программы, которые могут быть использованы для изъятия данных.
Осмотрительное поведение в социальных медиа: Будьте осторожными в социальных сетях, избегайте опубликования чувствительной информации, которая может быть использована для взлома вашего аккаунта.
Уведомление банка: Если вы заметили какие-либо подозрительные операции или утерю карты, сразу свяжитесь с вашим банком для отключения карты.
Образование: Будьте внимательными к инновационным подходам мошенничества и обучайтесь тому, как противостоять их.
Избегая легковерия и проявляя предельную осторожность, вы можете уменьшить риск стать жертвой обнала кредитных карт.
Опасности поддельными 5000 рублей: Распространение поддельных купюр и его консеквенции
В современном обществе, где виртуальные платежи становятся все более расширенными, мошенники не оставляют без внимания и классические методы недобросовестных действий, такие как распространение поддельных банкнот. В последнее время стало известно о неправомерной сбыте поддельных 5000 рублевых купюр, что представляет значительную потенциальную опасность для финансовой инфраструктуры и населения в целом.
Способы передачи:
Нарушители активно используют тайные трассы сети для торговли недостоверных 5000 рублей. На скрытых веб-ресурсах и противозаконных форумах можно обнаружить прошения недостоверных банкнот. К сожалению, это создает хорошие условия для распространения поддельных денег среди населения.
Консеквенции для сообщества:
Наличие недостоверных денег в обращении может иметь важные результаты для финансовой системы и доверенности к рублю. Люди, не замечая, что получили поддельные купюры, могут использовать их в разнообразных ситуациях, что в последней инстанции приводит к потере кредитоспособности к банкнотам некоего номинала.
Опасности для граждан:
Население становятся потенциальными пострадавшими мошенников, когда они случайным образом получают фальшивые деньги в сделках или при покупках. В результате, они могут столкнуться с нелестными ситуациями, такими как отклонение торговцев принять поддельные купюры или даже возможность привлечения к ответственности за пробу расплаты недостоверными деньгами.
Борьба с дистрибуцией фальшивых денег:
В интересах гарантирования граждан от подобных преступлений необходимо укрепить процедуры по обнаружению и предотвращению производства фальшивых денег. Это включает в себя работу в партнерстве между полицейскими и финансовыми институтами, а также повышение степени подготовки населения относительно характеристик поддельных банкнот и способов их обнаружения.
Завершение:
Диффузия фальшивых 5000 рублей – это весомая опасность для финансового благополучия и безопасности общества. Гарантирование доверия к рублю требует единых действий со с участием сторон правительства, банков и каждого. Важно быть внимательным и информированным, чтобы предотвратить раскрутку недостоверных денег и защитить финансовые средства общества.
Покупка фальшивых банкнот представляет собой недозволенным и опасительным актом, что имеет возможность повлечь за собой важным правовым санкциям или постраданию личной денежной стабильности. Вот несколько других приводов, по какой причине получение лживых банкнот считается опасной иначе неуместной:
Нарушение законов:
Закупка и использование лживых денег являются преступлением, нарушающим правила страны. Вас имеют возможность подвергнуть юридическим последствиям, которое может повлечь за собой тюремному заключению, финансовым санкциям или постановлению под стражу.
Ущерб доверию:
Лживые банкноты ухудшают доверие в денежной организации. Их применение формирует опасность для порядочных людей и организаций, которые в состоянии столкнуться с неожиданными потерями.
Экономический ущерб:
Распространение контрафактных банкнот оказывает воздействие на финансовую систему, вызывая рост цен что ухудшает глобальную финансовую устойчивость. Это может привести к потере доверия в денежной системе.
Риск обмана:
Лица, кто, осуществляют созданием фальшивых банкнот, не обязаны поддерживать какие-либо нормы степени. Контрафактные бумажные деньги могут стать легко распознаны, что, в итоге повлечь за собой потерям для тех, кто собирается их использовать.
Юридические последствия:
При событии задержания при воспользовании поддельных банкнот, вас имеют возможность взыскать штраф, и вы столкнетесь с юридическими трудностями. Это может повлиять на вашем будущем, с учетом трудности с трудоустройством и кредитной историей.
Общественное и личное благополучие основываются на правдивости и доверии в финансовой деятельности. Приобретение поддельных купюр нарушает эти принципы и может представлять серьезные последствия. Рекомендуется держаться законов и заниматься исключительно законными финансовыми транзакциями.
Greetings! Very helpful advice within this post! It is the little changes which will make the most important changes. Thanks a lot for sharing!
why should I be shy to show what chat with cam girls live wasnt ashamed to create?
I couldn’t agree more with the insightful points you’ve articulated in this article. Your profound knowledge on the subject is evident, and your unique perspective adds an invaluable dimension to the discourse. This is a must-read for anyone interested in this topic.
Your positivity and enthusiasm are truly infectious! This article brightened my day and left me feeling inspired. Thank you for sharing your uplifting message and spreading positivity to your readers.
Your blog is a true gem in the vast expanse of the online world. Your consistent delivery of high-quality content is truly commendable. Thank you for consistently going above and beyond in providing valuable insights. Keep up the fantastic work!
Купил фальшивые рубли
Покупка лживых денег приравнивается к недозволенным или опасительным актом, что имеет возможность послать в важным юридическим воздействиям либо постраданию своей денежной стабильности. Вот некоторые другие причин, почему приобретение контрафактных денег считается рискованной иначе неуместной:
Нарушение законов:
Приобретение или использование фальшивых купюр являются правонарушением, нарушающим правила государства. Вас могут подвергнуть себя судебному преследованию, что возможно привести к лишению свободы, взысканиям и приводу в тюрьму.
Ущерб доверию:
Поддельные деньги нарушают доверие к финансовой системе. Их использование порождает угрозу для благоприятных людей и бизнесов, которые способны попасть в неожиданными расходами.
Экономический ущерб:
Расширение поддельных купюр осуществляет воздействие на экономику, вызывая распределение денег и ухудшающая глобальную финансовую стабильность. Это в состоянии послать в утрате уважения к национальной валюте.
Риск обмана:
Лица, какие, осуществляют созданием поддельных купюр, не обязаны соблюдать какие-либо уровни уровня. Поддельные купюры могут оказаться легко распознаны, что, в итоге повлечь за собой убыткам для тех, кто пытается применять их.
Юридические последствия:
При случае попадания под арест при применении контрафактных купюр, вас имеют возможность оштрафовать, и вы столкнетесь с юридическими трудностями. Это может повлиять на вашем будущем, в том числе сложности с поиском работы с кредитной историей.
Общественное и индивидуальное благосостояние основываются на честности и доверии в финансовой сфере. Покупка контрафактных банкнот противоречит этим принципам и может иметь серьезные последствия. Советуем придерживаться правил и осуществлять только законными финансовыми действиями.
This article is a true game-changer! Your practical tips and well-thought-out suggestions hold incredible value. I’m eagerly anticipating implementing them. Thank you not only for sharing your expertise but also for making it accessible and easy to apply.
Your enthusiasm for the subject matter shines through in every word of this article. It’s infectious! Your dedication to delivering valuable insights is greatly appreciated, and I’m looking forward to more of your captivating content. Keep up the excellent work!
Your blog has rapidly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you invest in crafting each article. Your dedication to delivering high-quality content is apparent, and I eagerly await every new post.
Your blog has rapidly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you invest in crafting each article. Your dedication to delivering high-quality content is apparent, and I eagerly await every new post.
Excellent post. I absolutely appreciate this site. Keep it up!
Your post reminded me that there is always a reason to keep fighting. Thank you for your bravery.
купить фальшивые деньги
Покупка поддельных купюр является противозаконным либо опасным поступком, которое может закончиться важным юридическими воздействиям или повреждению личной денежной благосостояния. Вот некоторые другие приводов, вследствие чего покупка лживых денег приравнивается к рискованной или недопустимой:
Нарушение законов:
Закупка и эксплуатация поддельных банкнот приравниваются к преступлением, противоречащим положения страны. Вас способны подвергнуть уголовной ответственности, что потенциально послать в тюремному заключению, штрафам и тюремному заключению.
Ущерб доверию:
Контрафактные банкноты ослабляют доверенность по отношению к денежной организации. Их применение порождает опасность для благоприятных личностей и коммерческих структур, которые имеют возможность столкнуться с внезапными перебоями.
Экономический ущерб:
Разведение контрафактных банкнот влияет на экономику, инициируя распределение денег и ухудшая всеобщую денежную устойчивость. Это способно привести к потере доверия в национальной валюте.
Риск обмана:
Лица, кто, осуществляют изготовлением поддельных купюр, не обязаны соблюдать какие-нибудь параметры характеристики. Фальшивые банкноты могут быть легко распознаваемы, что, в конечном итоге приведет к потерям для тех, кто собирается применять их.
Юридические последствия:
При случае захвата при использовании контрафактных банкнот, вас могут наказать штрафом, и вы столкнетесь с юридическими трудностями. Это может сказаться на вашем будущем, с учетом сложности с трудоустройством с кредитной историей.
Общественное и личное благополучие зависят от правдивости и доверии в денежной области. Приобретение контрафактных банкнот не соответствует этим принципам и может обладать серьезные последствия. Предлагается держаться законов и заниматься исключительно правомерными финансовыми сделками.
Your unique approach to addressing challenging subjects is like a breath of fresh air. Your articles stand out with their clarity and grace, making them a pure joy to read. Your blog has now become my go-to source for insightful content.
Your writing style effortlessly draws me in, and I find it difficult to stop reading until I reach the end of your articles. Your ability to make complex subjects engaging is a true gift. Thank you for sharing your expertise!
Your enthusiasm for the subject matter radiates through every word of this article; it’s contagious! Your commitment to delivering valuable insights is greatly valued, and I eagerly anticipate more of your captivating content. Keep up the exceptional work!
магазин фальшивых денег купить
Покупка фальшивых банкнот является незаконным и потенциально опасным поступком, которое способно послать в серьезным правовым воздействиям либо повреждению вашей финансовой надежности. Вот некоторые причин, вследствие чего получение лживых купюр является потенциально опасной иначе недопустимой:
Нарушение законов:
Покупка либо воспользование поддельных купюр считаются противоправным деянием, противоречащим законы территории. Вас способны подвергнуться наказанию, что потенциально закончиться тюремному заключению, денежным наказаниям либо лишению свободы.
Ущерб доверию:
Лживые купюры ослабляют доверие по отношению к денежной организации. Их обращение возникает возможность для честных личностей и коммерческих структур, которые имеют возможность столкнуться с неожиданными расходами.
Экономический ущерб:
Распространение лживых купюр влияет на финансовую систему, вызывая инфляцию что ухудшает общественную денежную устойчивость. Это в состоянии привести к утрате уважения к денежной единице.
Риск обмана:
Те, какие, осуществляют созданием лживых купюр, не обязаны соблюдать какие-то нормы качества. Лживые купюры могут быть легко обнаружены, что, в конечном итоге приведет к убыткам для тех, кто собирается применять их.
Юридические последствия:
При событии захвата при воспользовании фальшивых банкнот, вас имеют возможность оштрафовать, и вы столкнетесь с юридическими проблемами. Это может оказать воздействие на вашем будущем, включая трудности с трудоустройством и историей кредита.
Общественное и индивидуальное благосостояние зависят от правдивости и уважении в финансовых отношениях. Получение фальшивых купюр нарушает эти принципы и может иметь серьезные последствия. Рекомендуем придерживаться правил и заниматься исключительно законными финансовыми сделками.
Good info. Lucky me I ran across your blog by accident (stumbleupon). I’ve saved it for later!
Обналичивание карт – это незаконная деятельность, становящаяся все более популярной в нашем современном мире электронных платежей. Этот вид мошенничества представляет серьезные вызовы для банков, правоохранительных органов и общества в целом. В данной статье мы рассмотрим частоту встречаемости обналичивания карт, используемые методы и возможные последствия для жертв и общества.
Частота обналичивания карт:
Обналичивание карт является весьма распространенным явлением, и его частота постоянно растет с увеличением числа электронных транзакций. Киберпреступники применяют разнообразные методы для получения доступа к финансовым средствам, включая фишинг, вредоносное программное обеспечение, скимминг и другие инновационные подходы.
Методы обналичивания карт:
Фишинг: Злоумышленники могут отправлять фальшивые электронные сообщения или создавать веб-сайты, имитирующие банковские системы, с целью получения личной информации от владельцев карт.
Скимминг: Злоумышленники устанавливают устройства скиммеры на банкоматах или терминалах для считывания данных с магнитных полос карт.
Вредоносное программное обеспечение: Киберпреступники разрабатывают вредоносные программы, которые заражают компьютеры и мобильные устройства, чтобы получить доступ к личным данным и банковским счетам.
Сетевые атаки: Атаки на системы банков и платежных платформ могут привести к утечке информации о картах и, следовательно, к их обналичиванию.
Последствия обналичивания карт:
Финансовые потери для клиентов: Владельцы карт могут столкнуться с денежными потерями, так как средства могут быть списаны с их счетов без их ведома.
Угроза безопасности данных: Обналичивание карт подчеркивает угрозу безопасности личных данных, что может привести к краже личной и финансовой информации.
Ущерб репутации банков: Банки и другие финансовые учреждения могут столкнуться с утратой доверия со стороны клиентов, если их системы безопасности оказываются уязвимыми.
Проблемы для экономики: Обналичивание карт создает экономический ущерб, поскольку оно стимулирует дополнительные затраты на борьбу с мошенничеством и восстановление утраченных средств.
Борьба с обналичиванием карт:
Совершенствование технологий безопасности: Банки и финансовые институты постоянно совершенствуют свои системы безопасности, чтобы предотвратить несанкционированный доступ к картам.
Образование и информирование: Обучение клиентов о методах мошенничества и том, как защитить свои данные, является важным шагом в борьбе с обналичиванием карт.
Сотрудничество с правоохранительными органами: Банки активно сотрудничают с правоохранительными органами для выявления и пресечения преступных схем.
Заключение:
Обналичивание карт – серьезная угроза для финансовой стабильности и безопасности личных данных. Решение этой проблемы требует совместных усилий со стороны банков, правоохранительных органов и общества в целом. Только эффективная борьба с мошенничеством позволит обеспечить безопасность электронных платежей и защитить интересы всех участников финансовой системы.
sm-online-game.com
이 왕복 티켓은… 바닥이 없는 구덩이입니다.
I simply wanted to convey how much I’ve gleaned from this article. Your meticulous research and clear explanations make the information accessible to all readers. It’s abundantly clear that you’re committed to providing valuable content.
I’d like to express my heartfelt appreciation for this enlightening article. Your distinct perspective and meticulously researched content bring a fresh depth to the subject matter. It’s evident that you’ve invested a great deal of thought into this, and your ability to articulate complex ideas in such a clear and comprehensible manner is truly commendable. Thank you for generously sharing your knowledge and making the process of learning so enjoyable.
Your unique approach to addressing challenging subjects is like a breath of fresh air. Your articles stand out with their clarity and grace, making them a pure joy to read. Your blog has now become my go-to source for insightful content.
Thank you so much for sharing this wonderful post with us.
Oh my goodness! Amazing article dude! Thanks, However I am experiencing troubles with your RSS. I don’t know why I cannot subscribe to it. Is there anybody having similar RSS problems? Anyone that knows the solution will you kindly respond? Thanx!
Aw, this was a very good post. Taking the time and actual effort to create a great article… but what can I say… I hesitate a whole lot and don’t manage to get nearly anything done.
Good post! We will be linking to this particularly great article on our site. Keep up the great writing.
gdzie mozna kupic prawo jazdy z wpisem do rejestru, kupić prawo jazdy, legalne prawo jazdy do kupienia, kupię prawo jazdy, jak załatwić prawo jazdy, bez egzaminu, jak kupić prawo jazdy, czy można kupić prawo jazdy, legalne prawo jazdy do kupienia 2022, pomogę zdać egzamin na prawo jazdy, prawo jazdy bez egzaminu, gdzie kupić prawo jazdy bez egzaminu, gdzie kupić prawo jazdy na lewo, jak kupić prawo jazdy w niemczech, gdzie kupic prawo jazdy legalnie, kupić prawo jazdy b
.,mn
comprar carta de conduçao preço, comprar carta de condução verdadeira, comprar carta de conduçao, comprar carta de condução lisboa, comprar carta de condução legal, comprar carta de condução, carta de condução comprar, comprar carta de conduçao, comprar carta de condução em Portugal, comprar carta, comprar carta de condução portugal, comprar carta de condução online, comprar a carta de condução, carta de condução, comprar carta de carro, imt carta de condução, comprar carta de condução no porto
sjdke
Your kindness is a gift to the world. Thank you for being you.
sportbootführerschein binnen und see, sportbootführerschein binnen prüfungsfragen, sportbootführerschein binnen kosten, sportbootführerschein binnen online, sportbootführerschein binnen wo darf ich fahren, sportbootführerschein binnen berlin, sportbootführerschein binnen segel, sportbootführerschein kaufen, sportbootführerschein kaufen erfahrungen, sportbootführerschein kaufen schwarz, sportbootführerschein see kaufen, sportbootführerschein binnen kaufen, sportbootführerschein see kaufen ohne prüfung, bootsführerschein kaufen, bootsführerschein kaufen polen, bootsführerschein kaufen erfahrungen, bootsführerschein online kaufen, bootsführerschein tschechien kaufen.
‘;lkm
Your kindness knows no bounds. Thank you for being a source of love and support.
e legale comprare la patente, comprare una patente napoli, patente originale, comprare patente c, acquisto patente b, comprare patente prezzo, compro patente, acquistare patente b napoli, dove posso comprare la patente b, compra patente online, comprare patente b online, comprare la patente a napoli, dove si può comprare la patente, quanto costa comprare la patente, comprare patente di guida, comprare patente senza esame, patente comprata prezzo, come comprare patente b napoli, comprare patente a, patente online comprare, quanto costa la patente a napoli, patente Nautica.
;lkjngh
motorrad führerschein kaufen , lkw führerschein kaufen ohne prüfung österreich, bus führerschein kosten österreich. führerschein online kaufen, auto c ohne prüfung köln, führerschein klasse b kaufen, deutschen registrierten führerschein kaufen berlin, österreich führerschein kaufen legal in deutschland, führerschein in deutschland kaufen, PKW führerschein kaufen österreich, deutschen führerschein legal kaufen in österreich, kaufe deutschen führerschein, eu-führerschein kaufen,wie viel kostet der führerschein in österreich.
‘;lkjh
It’s nearly impossible to find experienced people in this particular topic, however, you seem like you know what you’re talking about! Thanks
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
I’m grateful to have come across this content. It illuminated my day in a unique way. Keep shining!
This post made my heart smile. Thank you for brightening my day and bringing so much joy!
hoki 1881
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
smcasino-game.com
두 번째 장이 전달되고 호랑이는 월간 패스를 요구합니다 전투는 치열합니다.
Today needed a positive boost, and your post came at the right time. Keep filling our days with that positivity!
Kantorbola adalah situs slot gacor terbaik di indonesia , kunjungi situs RTP kantor bola untuk mendapatkan informasi akurat slot dengan rtp diatas 95% . Kunjungi juga link alternatif kami di kantorbola77 dan kantorbola99 .
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
What a wonderful post! It truly illuminated my day and made everything lighter. Keep spreading that positivity!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
Today was a bit down, but your content completely changed my mood. Keep those amazing posts coming!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
What a wonderful post! It truly illuminated my day and made everything lighter. Keep spreading that positivity!
Your post is like a beam of light amidst dark clouds. Keep spreading that light to all of us!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
This content brightened up my day, keep creating posts like this!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
Hello there! This article couldn’t be written any better! Going through this article reminds me of my previous roommate! He continually kept preaching about this. I am going to forward this article to him. Fairly certain he’s going to have a good read. Many thanks for sharing!
I never imagined a post could have so much power to brighten my day. Keep the magic alive in your content!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
I needed something to lift my spirits, and your post did just that. Keep up the incredible work!
hoki1881
This article is a true game-changer! Your practical tips and well-thought-out suggestions hold incredible value. I’m eagerly anticipating implementing them. Thank you not only for sharing your expertise but also for making it accessible and easy to apply.
Your enthusiasm for the subject matter shines through every word of this article; it’s contagious! Your commitment to delivering valuable insights is greatly valued, and I eagerly anticipate more of your captivating content. Keep up the exceptional work!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
I could not resist commenting. Exceptionally well written.
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
Today was a bit down, but your content completely changed my mood. Keep those amazing posts coming!
I never imagined a post could have so much power to brighten my day. Keep the magic alive in your content!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
What a wonderful post! It truly illuminated my day and made everything lighter. Keep spreading that positivity!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
Way cool! Some very valid points! I appreciate you writing this post and also the rest of the website is extremely good.
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
Your post brought a genuine smile to my face. Keep filling our days with that contagious joy!
Today needed a positive boost, and your post came at the right time. Keep filling our days with that positivity!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
That is a great tip particularly to those new to the blogosphere. Brief but very accurate information… Thank you for sharing this one. A must read post.
I needed something to lift my spirits, and your post did just that. Keep up the incredible work!
zinmanga
I’m on the same page as those above – this post is a delightful masterpiece!
I blog quite often and I truly thank you for your content. This article has truly peaked my interest. I will take a note of your blog and keep checking for new details about once per week. I opted in for your Feed too.
Echoing the sentiments above – this post is a true gem!
Echoing the sentiments above – this post is a true gem!
Couldn’t agree more – this post is an absolute pleasure to read!
Your unique approach to addressing challenging subjects is like a breath of fresh air. Your articles stand out with their clarity and grace, making them a pure joy to read. Your blog has now become my go-to source for insightful content.
I echo the sentiments above – this post is an absolute delight!
Couldn’t agree more with the praises above; this post is wonderful!
I’m on the same page as those above – this post is a delightful masterpiece!
Completely in agreement with the sentiments expressed above – this post is superb!
Fully resonate with the sentiments shared above – this post is a gem!
Completely aligned with the opinions above – this post is a true gem!
Couldn’t agree more with the praises above; this post is wonderful!
Couldn’t agree more – this post is an absolute pleasure to read!
I echo the sentiments above – this post is an absolute delight!
Couldn’t agree more – this post is an absolute pleasure to read!
I echo the sentiments above – this post is an absolute delight!
Fully resonate with the sentiments expressed above – this post is fantastic!
Echoing the sentiments above – this post is a true gem!
Couldn’t agree more with the praises above; this post is wonderful!
טלגראס כיוונים מרכז
מרכז המידע עבור רֶּקַע כיוונים (Telegrass), הידוע גם בשמות “רֶּקַע” או “גַּרְגִּירֵים כיוונים”, היא אתר הספק מידע, לינקים, קישורים, מדריכים והסברים בנושאי קנאביס בתוך הארץ. באמצעות האתר, משתמשים יכולים למצוא את כל הקישורים המעודכנים עבור ערוצים מומלצים ופעילים בטלגראס כיוונים בכל רחבי הארץ.
טלגראס כיוונים הוא אתר ובוט בתוך פלטפורמת טלגראס, מספק דרכי תקשורת ושירותים שונים בתחום רכישת קנאביס וקשורים. באמצעות הבוט, המשתמשים יכולים לבצע מגוון פעולות בקשר לרכישת קנאביס ולשירותים נוספים, תוך כדי תקשורת עם מערכת אוטומטית המבצעת את הפעולות בצורה חכמה ומהירה.
בוט הטלגראס (Telegrass Bot) מציע מגוון פעולות שימושיות למשתמשות: רכישה קנאביס: בצע רכישה דרך הבוט על ידי בחירת סוגי הקנאביס, כמות וכתובת למשלוח.
שאלות ותמיכה: קבל מידע על המוצרים והשירותים, תמיכה טכנית ותשובות לשאלות שונות.
בחינה מלאי: בדוק את המלאי הזמין של קנאביס ובצע הזמנה תוך כדי הקשת הבדיקה.
הצבת ביקורות: הוסף ביקורות ודירוגים למוצרים שרכשת, כדי לעזור למשתמשים אחרים.
הכנסת מוצרים חדשים: הוסף מוצרים חדשים לפלטפורמה והצג אותם למשתמשים.
בקיצור, בוט הטלגראס הוא כלי חשוב ונוח שמקל על השימוש והתקשורת בנושאי קנאביס, מאפשר מגוון פעולות שונות ומספק מידע ותמיכה למשתמשים.
Your blog has quickly become my trusted source of inspiration and knowledge. I genuinely appreciate the effort you put into crafting each article. Your dedication to delivering high-quality content is evident, and I look forward to every new post.
ttbslot.com
이 미용실에는 고위 관리들과 유명인사들뿐만 아니라 교사들과 왕족들이 이곳에 모였습니다.
Your positivity and enthusiasm are undeniably contagious! This article brightened my day and left me feeling inspired. Thank you for sharing your uplifting message and spreading positivity among your readers.
qiyezp.com
“…” Fang Jifan은 잠시 침묵했다가 웃으며 “나는 달라!”
I couldn’t refrain from commenting. Perfectly written!
hoki 1881
This site was… how do I say it? Relevant!! Finally I’ve found something that helped me. Kudos!
Your post reminded me that I am stronger than I think. Thank you for your encouragement.
Your kindness is a gift to the world. Thank you for being you.
Your resilience is a testament to the power of the human spirit. Thank you for sharing your journey.
Your words of encouragement were just what I needed to hear today. Thank you for your support.
sandyterrace.com
앞으로… 의례부가 뿌듯함을 느낄 수 있을 것 같습니다.
Your words of wisdom came at just the right time. Thank you for sharing your insight.
Your post gave me the strength to face another day with hope in my heart. Thank you.
Your post reminded me to be grateful, even on the toughest days. Thank you for the perspective shift.
даркнет площадки
Теневые площадки, или теневые рынки, есть веб-платформы, доступные лишь через даркнет – интернет-сеть, скрытая для обыкновенных поисковиков. Такие платформы дают возможность участникам торговать разными товарными единицами или услугами, наиболее часто противоправного типа, такими как наркотические препараты, оружие, данные, похищенные из систем, фальшивки а прочие запрещенные либо незаконные товары или услуги.
Подпольные площадки снабжают скрытность их собственных пользователей посредством использования особенных программного обеспечения и параметров, такие как The Onion Router, те скрывают IP-адреса а маршрутизируют интернет-трафик с помощью разнообразные узловые соединения, что делает непростым отслеживание деятельности полицейскими.
Эти торговые площадки иногда попадают объектом внимания правоохранительных органов, какие борются противодействуют ними в рамках борьбе против интернет-преступностью а незаконной продажей.
Today feels like a day filled with warmth, and your post is like a cozy blanket on a chilly morning.
nice content!nice history!! boba 😀
государстве, как и в других территориях, даркнет является собой отрезок интернета, неприступную для обычного поискавания и просмотра через стандартные браузеры. В противоположность от общедоступной поверхностной соединения, даркнет является неизвестным фрагментом интернета, выход к какому обычно проводится через эксклюзивные программы, подобные как Tor Browser, и неизвестные сети, такие как Tor.
В скрытой части интернета собраны различные источники, включая дискуссии, рынки, журналы и прочие сайты, которые могут быть недоступны или пресечены в регулярной инфраструктуре. Здесь возможно найти различные продукты и услуги, включая нелегальные, например наркотические препараты, оружие, компрометированные сведения, а также послуги компьютерных взломщиков и другие.
В государстве даркнет как и применяется для преодоления цензуры и мониторинга со партии. Некоторые участники могут применять его для передачи информацией в условиях, когда воля слова замкнута или информационные ресурсы подвергнуты цензуре. Однако, также рекомендуется отметить, что в даркнете присутствует много не Законной деятельности и потенциально опасных положений, включая мошенничество и киберпреступления
wow, amazing
nice content!nice history!! boba 😀
I quite like reading through a post that will make men and women think. Also, thank you for allowing me to comment.
I enjoy looking through a post that will make men and women think. Also, many thanks for allowing me to comment.
otraresacamas.com
生活に直接役立つ実用的な情報が満載で、大変感謝しています。
What a picturesque day it is today, made even more delightful by your heartfelt post.
Даркнет заказать
Экзистенция подпольных онлайн-рынков – это феномен, что привлекает громадный заинтересованность или обсуждения в современном обществе. Подпольная часть веба, или подпольная область сети, отображает тайную сеть, доступные тольково через специальные программы а настройки, снабжающие неузнаваемость пользовательских аккаунтов. По этой данной скрытой платформе находятся даркнет-маркеты – интернет-ресурсы, где-нибудь торгуются различные вещи а сервисы, чаще всего противозаконного характера.
На теневых электронных базарах легко обнаружить самые различные вещи: наркотики, оружие, похищенная информация, уязвимые аккаунты, фальшивки и и многое многое другое. Такие же площадки часто притягивают восторг и правонарушителей, и обыкновенных пользовательских аккаунтов, хотящих обходить право или даже получить возможность доступа к вещам и послугам, какие именно в обычном всемирной сети могли бы быть недосягаемы.
Однако стоит помнить, как практика по даркнет-маркетах представляет собой неправомерный степень и имеет возможность повлечь за собой серьезные юридические последствия по закону. Полицейские настойчиво сопротивляются против подобными маркетами, но по причине анонимности скрытой сети это обстоятельство далеко не постоянно легко.
Следовательно, наличие теневых электронных базаров является действительностью, но все же эти площадки пребывают сферой серьезных потенциальных угроз как и для пользовательских аккаунтов, и для таких социума в общем.
Today is a reminder that even amidst challenges, there is still beauty to be found. Your post is a testament to that.
Today is a reminder to appreciate the beauty around us, and your post is a beautiful example of that.
Today feels like a day full of endless possibilities, and stumbling upon your post adds to the excitement.
It’s a gorgeous day outside, but nothing compares to the warmth and positivity of your post.
даркнет покупки
Покупки в темном интернете: Иллюзии и Реальность
Подпольная сеть, таинственная секция сети, манит интерес участников своим тайностью и возможностью заказать различные вещи и сервисы без излишних действий. Однако, погружение в этот мрак темных площадок сопряжено с рядом опасностей и сложностей, о чём необходимо понимать перед осуществлением покупок.
Что такое скрытая часть веба и как он работает?
Для того, кто не знаком с этим понятием, темный интернет – это сектор интернета, невидимая от обычных поисковиков. В темном интернете существуют уникальные онлайн-рынки, где можно найти возможность почти все виды : от наркотиков и оружия до взломанных аккаунтов и фальшивых документов.
Мифы о приобретении товаров в скрытой части веба
Скрытность защищена: При всём том, использование анонимных технологий, например Tor, может помочь скрыть от глаз свою действия в сети, тайность в скрытой части веба не является полной. Существует возможность, что может ваша информацию о вас могут выявить обманщики или даже сотрудники правоохранительных органов.
Все товары – качественные: В подпольной сети можно найти множество поставщиков, предоставляющих продукты и сервисы. Однако, нельзя гарантировать качество или подлинность товара, так как невозможно проверить до совершения покупки.
Легальные транзакции без последствий: Многие пользователи неправильно думают, что приобретая товары в темном интернете, они подвергают себя риску низкому риску, чем в реальной жизни. Однако, заказывая противоправные продукцию или услуги, вы рискуете привлечения к уголовной ответственности.
Реальность покупок в подпольной сети
Негативные стороны обмана и мошенничества: В Даркнете многочисленные аферисты, предрасположены к мошенничеству недостаточно осторожных пользователей. Они могут предложить поддельную продукцию или просто исчезнуть с вашими деньгами.
Опасность правоохранительных органов: Пользователи темного интернета подвергают себя риску к уголовной ответственности за покупку и заказ противозаконных.
Непредвиденность выходов: Не каждая сделка в подпольной сети завершаются благополучно. Качество вещей может оказаться низким, а сам процесс приобретения может послужить источником неприятностей.
Советы для безопасных транзакций в Даркнете
Проводите тщательное исследование поставщика и продукции перед приобретением.
Используйте безопасные программы и сервисы для обеспечения анонимности и безопасности.
Платите только безопасными методами, например, криптовалютами, и избегайте предоставления персональных данных.
Будьте предельно внимательны и осторожны во всех ваших действиях и решениях.
Заключение
Сделки в подпольной сети могут быть как интересным, так и опасным опытом. Понимание рисков и принятие соответствующих мер предосторожности помогут уменьшить риск негативных последствий и гарантировать безопасные покупки в этом непознанном уголке сети.
thephotoretouch.com
Fang Jifan은 이것을 듣고 Hongzhi 황제가 의미하는 바를 이해했습니다.
The sun is shining, the flowers are blooming, and your post is like a breath of fresh air.
The sun is shining, the birds are chirping, and your post is music to my soul.
Today is a masterpiece waiting to unfold, and your post is the first stroke of brilliance.
Today feels like a day filled with endless opportunities, and your post is the perfect motivation.
That is a great tip especially to those new to the blogosphere. Short but very precise info… Thanks for sharing this one. A must read article!
Amidst the chaos of life, your post is a reminder to find peace and joy in every moment.
Today feels like a day filled with warmth, and your post is like a cozy blanket on a chilly morning.
This site was… how do I say it? Relevant!! Finally I’ve found something which helped me. Thank you!
Today feels like a day filled with endless possibilities, and your post is the perfect inspiration.
The sun is casting its golden glow, and your post is equally radiant. Thank you for brightening my day.
Today is a reminder that even in the darkest moments, there is still beauty to be found. Your post exemplifies that.
Today feels like a day filled with endless possibilities, and your post is the perfect start.
Today feels like a day filled with endless opportunities, and your post is the perfect motivation.
The sun is casting its golden glow, and your post is equally radiant. Thank you for brightening my day.
I truly love your website.. Pleasant colors & theme. Did you make this website yourself? Please reply back as I’m attempting to create my own personal blog and would love to know where you got this from or what the theme is named. Many thanks.
Today is a reminder to find joy in the little things, and your post is a perfect example of that.
After I initially commented I appear to have clicked on the -Notify me when new comments are added- checkbox and now whenever a comment is added I recieve four emails with the exact same comment. There has to be an easy method you are able to remove me from that service? Thank you.
blobloblu
blublabla
Good info. Lucky me I found your blog by chance (stumbleupon). I have book marked it for later.
elementor
elementor
blublabla
blablablu
I blog quite often and I really appreciate your information. This great article has really peaked my interest. I will book mark your blog and keep checking for new details about once a week. I subscribed to your Feed as well.
blobloblu
i love danatoto
You’re so interesting! I don’t suppose I’ve read through anything like that before. So good to discover someone with some original thoughts on this subject matter. Seriously.. thanks for starting this up. This web site is one thing that is needed on the internet, someone with a bit of originality.
Howdy! I simply would like to offer you a big thumbs up for the excellent information you’ve got right here on this post. I am coming back to your blog for more soon.
bmipas.com
この記事を読んで、たくさんのインスピレーションを受けました。ありがとうございます。
Aw, this was a very good post. Taking the time and actual effort to create a top notch article… but what can I say… I hesitate a lot and don’t seem to get nearly anything done.
Hello, I do believe your website might be having internet browser compatibility problems. Whenever I take a look at your blog in Safari, it looks fine however, when opening in IE, it’s got some overlapping issues. I just wanted to provide you with a quick heads up! Besides that, wonderful blog!
Next time I read a blog, I hope that it won’t fail me just as much as this one. I mean, Yes, it was my choice to read through, but I really thought you would have something useful to say. All I hear is a bunch of moaning about something you could possibly fix if you were not too busy looking for attention.
Thank you so much for sharing this wonderful post with us.
exprimegranada.com
いつも興味深い内容で、読むのが待ち遠しいです。
Today, while I was at work, my sister stole my iphone and tested to see if it can survive a 40 foot drop, just so she can be a youtube sensation. My iPad is now broken and she has 83 views. I know this is totally off topic but I had to share it with someone!
I’m not that much of a online reader to be honest but your sites really nice, keep it up! I’ll go ahead and bookmark your site to come back in the future. All the best
Your post gave me hope when I needed it most. Thank you for your courage.
Your kindness knows no bounds. Thank you for being a source of love and support.
exprimegranada.com
この記事は本当に役に立ちます。大変感謝しています。
Your kindness is a gift to the world. Thank you for being you.
Your resilience in the face of challenges is remarkable. Thank you for sharing your journey.
gdzie mozna kupic prawo jazdy z wpisem do rejestru, kupić prawo jazdy, legalne prawo jazdy do kupienia, kupię prawo jazdy, jak załatwić prawo jazdy, bez egzaminu, jak kupić prawo jazdy, czy można kupić prawo jazdy, legalne prawo jazdy do kupienia 2022, pomogę zdać egzamin na prawo jazdy, prawo jazdy bez egzaminu, gdzie kupić prawo jazdy bez egzaminu, gdzie kupić prawo jazdy na lewo, jak kupić prawo jazdy w niemczech, gdzie kupic prawo jazdy legalnie, kupić prawo jazdy b
kupic prawo jazdy
Informasi RTP Live Hari Ini Dari Situs RTPKANTORBOLA
Situs RTPKANTORBOLA merupakan salah satu situs yang menyediakan informasi lengkap mengenai RTP (Return to Player) live hari ini. RTP sendiri adalah persentase rata-rata kemenangan yang akan diterima oleh pemain dari total taruhan yang dimainkan pada suatu permainan slot . Dengan adanya informasi RTP live, para pemain dapat mengukur peluang mereka untuk memenangkan suatu permainan dan membuat keputusan yang lebih cerdas saat bermain.
Situs RTPKANTORBOLA menyediakan informasi RTP live dari berbagai permainan provider slot terkemuka seperti Pragmatic Play , PG Soft , Habanero , IDN Slot , No Limit City dan masih banyak rtp permainan slot yang bisa kami cek di situs RTP Kantorboal . Dengan menyediakan informasi yang akurat dan terpercaya, situs ini menjadi sumber informasi yang penting bagi para pemain judi slot online di Indonesia .
Salah satu keunggulan dari situs RTPKANTORBOLA adalah penyajian informasi yang terupdate secara real-time. Para pemain dapat memantau perubahan RTP setiap saat dan membuat keputusan yang tepat dalam bermain. Selain itu, situs ini juga menyediakan informasi mengenai RTP dari berbagai provider permainan, sehingga para pemain dapat membandingkan dan memilih permainan dengan RTP tertinggi.
Informasi RTP live yang disediakan oleh situs RTPKANTORBOLA juga sangat lengkap dan mendetail. Para pemain dapat melihat RTP dari setiap permainan, baik itu dari aspek permainan itu sendiri maupun dari provider yang menyediakannya. Hal ini sangat membantu para pemain dalam memilih permainan yang sesuai dengan preferensi dan gaya bermain mereka.
Selain itu, situs ini juga menyediakan informasi mengenai RTP live dari berbagai provider judi slot online terpercaya. Dengan begitu, para pemain dapat memilih permainan slot yang memberikan RTP terbaik dan lebih aman dalam bermain. Informasi ini juga membantu para pemain untuk menghindari potensi kerugian dengan bermain pada game slot online dengan RTP rendah .
Situs RTPKANTORBOLA juga memberikan pola dan ulasan mengenai permainan-permainan dengan RTP tertinggi. Para pemain dapat mempelajari strategi dan tips dari para ahli untuk meningkatkan peluang dalam memenangkan permainan. Analisis dan ulasan ini disajikan secara jelas dan mudah dipahami, sehingga dapat diaplikasikan dengan baik oleh para pemain.
Informasi RTP live yang disediakan oleh situs RTPKANTORBOLA juga dapat membantu para pemain dalam mengelola keuangan mereka. Dengan mengetahui RTP dari masing-masing permainan slot , para pemain dapat mengatur taruhan mereka dengan lebih bijak. Hal ini dapat membantu para pemain untuk mengurangi risiko kerugian dan meningkatkan peluang untuk mendapatkan kemenangan yang lebih besar.
Untuk mengakses informasi RTP live dari situs RTPKANTORBOLA, para pemain tidak perlu mendaftar atau membayar biaya apapun. Situs ini dapat diakses secara gratis dan tersedia untuk semua pemain judi online. Dengan begitu, semua orang dapat memanfaatkan informasi yang disediakan oleh situs RTP Kantorbola untuk meningkatkan pengalaman dan peluang mereka dalam bermain judi online.
Demikianlah informasi mengenai RTP live hari ini dari situs RTPKANTORBOLA. Dengan menyediakan informasi yang akurat, terpercaya, dan lengkap, situs ini menjadi sumber informasi yang penting bagi para pemain judi online. Dengan memanfaatkan informasi yang disediakan, para pemain dapat membuat keputusan yang lebih cerdas dan meningkatkan peluang mereka untuk memenangkan permainan. Selamat bermain dan semoga sukses!
Почему наши сигналы на вход – ваш идеальный путь:
Наша группа 24 часа в сутки на волне текущих направлений и событий, которые воздействуют на криптовалюты. Это дает возможность группе сразу действовать и предоставлять свежие подачи.
Наш состав обладает глубоким понимание анализа по графику и умеет выделить крепкие и слабые поля для входа в сделку. Это способствует снижению рисков и способствует для растущей прибыли.
Мы применяем собственные боты-анализаторы для изучения графиков на все периодах времени. Это содействует нашим специалистам доставать понятную картину рынка.
Перед опубликованием сигнал в нашем Telegram команда осуществляем тщательную проверку все аспектов и подтверждаем возможный лонг или период короткой торговли. Это обеспечивает предсказуемость и качественные показатели наших подач.
Присоединяйтесь к нашей группе прямо сейчас и достаньте доступ к проверенным торговым подачам, которые содействуют вам добиться успеха в финансах на рынке криптовалют!
https://t.me/Investsany_bot
Почему наши сигналы – твой оптимальный выбор:
Наша группа постоянно в курсе актуальных трендов и ситуаций, которые влияют на криптовалюты. Это способствует команде сразу действовать и подавать новые сообщения.
Наш состав обладает глубинным понимание анализа и умеет выделить мощные и незащищенные поля для вступления в сделку. Это способствует для снижения потерь и повышению прибыли.
Вместе с командой мы применяем личные боты для анализа для анализа графиков на любых временных промежутках. Это содействует нам доставать понятную картину рынка.
Перед подачей сигнала в нашем Telegram мы осуществляем тщательную проверку всех аспектов и подтверждаем допустимый длинный или шорт. Это обеспечивает достоверность и качественность наших подач.
Присоединяйтесь к нашему прямо сейчас и достаньте доступ к проверенным торговым сигналам, которые помогут вам вам добиться успеха в финансах на рынке криптовалют!
https://t.me/Investsany_bot
Итак почему наши сигналы – всегда идеальный выбор:
Наша команда все время на волне текущих трендов и событий, которые воздействуют на криптовалюты. Это позволяет команде быстро реагировать и предоставлять новые трейды.
Наш состав владеет глубинным знание технического анализа и может выделить устойчивые и слабые стороны для вступления в сделку. Это способствует уменьшению рисков и способствует для растущей прибыли.
Мы применяем собственные боты-анализаторы для изучения графиков на всех интервалах. Это способствует нам завоевать полную картину рынка.
Прежде опубликованием подача в нашем Telegram команда проводим внимательную проверку всех аспектов и подтверждаем возможный период долгой торговли или шорт. Это обеспечивает верность и качественные характеристики наших сигналов.
Присоединяйтесь к нашей команде к нашему Telegram каналу прямо сейчас и достаньте доступ к подтвержденным торговым сигналам, которые помогут вам добиться финансового успеха на рынке криптовалют!
https://t.me/Investsany_bot
Почему наши сигналы – всегда идеальный вариант:
Наша группа 24 часа в сутки на волне последних курсов и моментов, которые влияют на криптовалюты. Это позволяет коллективу сразу реагировать и подавать актуальные подачи.
Наш коллектив владеет профундным понимание технического анализа и способен выявлять сильные и уязвимые факторы для присоединения в сделку. Это способствует снижению угроз и максимизации прибыли.
Мы применяем собственные боты для анализа для анализа графиков на любых временных промежутках. Это помогает нам завоевать полную картину рынка.
Прежде подачей подачи в нашем Telegram мы проводим тщательную проверку все аспектов и подтверждаем возможный долгий или короткий. Это гарантирует предсказуемость и качественные показатели наших подач.
Присоединяйтесь к нам к нашему прямо сейчас и достаньте доступ к подтвержденным торговым подачам, которые помогут вам достичь успеха в финансах на рынке криптовалют!
https://t.me/Investsany_bot
JDBslot
JDB slot | The first bonus to rock the slot world
Exclusive event to earn real money and slot game points
JDB demo slot games for free = ?? Lucky Spin Lucky Draw!
How to earn reels free 2000? follow jdb slot games for free
#jdbslot
Demo making money : https://jdb777.com
#jdbslot #slotgamesforfree #howtoearnreels #cashreels
#slotgamepoint #demomakingmoney
Cash reels only at slot games for free
More professional jdb game bonus knowledge
Ways to Gain Turns Credit Complimentary 2000: Your Final Guide to Triumphant Large with JDB One-armed bandits
Are you you ready to embark on an exciting adventure into the universe of online slot games? Seek no further, just rotate to JDB777 FreeGames, where enthusiasm and substantial wins await you at every twist of the reel. In this comprehensive instruction, we’ll show you how to acquire reels credit free 2000 and uncover the stimulating world of JDB slots.
Experience the Excitement of Gaming Games for Free
At JDB777 FreeGames, we supply a wide range of captivating slot games that are certain to keep you entertained for hours on end. From vintage fruit machines to immersive themed slots, there’s something for every single sort of player to enjoy. And the best part? You can play all of our slot games for free and achieve real cash prizes!
Release Free Cash Reels and Achieve Big
One of the most exhilarating features of JDB777 FreeGames is the opportunity to earn reels credits complimentary 2000, which can be exchanged for real cash. Plainly sign up for an account, and you’ll receive your costless bonus to begin spinning and winning. With our liberal promotions and bonuses, the sky’s the ceiling when it comes to your winnings!
Direct Approaches and Points System
To maximize your winnings and open the entire potential of our slot games, it’s crucial to apprehend the tactics and points system. Our expert guides will take you through everything you need to have to know, from choosing the right games to grasping how to secure bonus points and cash prizes.
Exclusive Promotions and Specific Offers
As a member of JDB777 FreeGames, you’ll have access to exclusive promotions and special offers that are positive to augment your gaming experience. From welcome bonuses to daily rebates, there are plenty of opportunities to enhance your winnings and take your gameplay to the following level.
Join Us Today and Initiate Winning
Don’t miss out on your likelihood to win big with JDB777 FreeGames. Sign up now to assert your costless bonus of 2000 credits and commence spinning the reels for your opportunity to win real cash prizes. With our thrilling variety of slot games and generous promotions, the potentialities are endless. Join us today and commence winning!
JDB online
JDB online | 2024 best online slot game demo cash
How to earn reels? jdb online accumulate spin get bonus
Hot demo fun: Quick earn bonus for ranking demo
JDB demo for win? JDB reward can be exchanged to real cash
#jdbonline
777 sign up and get free 2,000 cash: https://www.jdb777.io/
#jdbonline #democash #demofun #777signup
#rankingdemo #demoforwin
2000 cash: Enter email to verify, enter verify, claim jdb bonus
Play with JDB games an online platform in every countries.
Enjoy the Delight of Gaming!
Free to Join, Gratis to Play.
Sign Up and Acquire a Bonus!
REGISTER NOW AND RECEIVE 2000?
We challenge you to claim a trial enjoyable welcome bonus for a****** members! Plus, there are other unique promotions waiting for you!
Learn more
JDB – N****** TO JOIN
Simple to play, real profit
Participate in JDB today and indulge in fantastic games without any investment! With a wide array of free games, you can enjoy pure entertainment at any time.
Quick play, quick join
Value your time and opt for JDB’s swift games. Just a few easy steps and you’re set for an amazing gaming experience!
Register now and generate money
Experience JDB: Instant play with n************ and the opportunity to win cash. Designed for effortless and lucrative play.
Dive into the Realm of Online Gaming Stimulation with Fun Slots Online!
Are you prepared to encounter the sensation of online gaming like never before? Seek no further than Fun Slots Online, your ultimate hub for exhilarating gameplay, endless entertainment, and invigorating winning opportunities!
At Fun Slots Online, we pride ourselves on offering a wide range of compelling games designed to keep you engaged and delighted for hours on end. From classic slot machines to innovative new releases, there’s something for everybody to enjoy. Plus, with our user-friendly interface and seamless gameplay experience, you’ll have no difficulty plunging straight into the action and savoring every moment.
But that’s not all – we also provide a selection of special promotions and bonuses to compensate our loyal players. From greeting bonuses for new members to privileged rewards for our top players, there’s always something exhilarating happening at Fun Slots Online. And with our secure payment system and 24-hour customer support, you can enjoy peace of mind aware that you’re in good hands every step of the way.
So why wait? Register with Fun Slots Online today and commence your voyage towards exciting victories and jaw-dropping prizes. Whether you’re a seasoned gamer or just starting out, there’s never been a better time to be part of the fun and adventure at Fun Slots Online. Sign up now and let the games begin!
Intro
betvisa vietnam
Betvisa vietnam | Grand P**** Breakout!
Betway Highlights | 499,000 Extra Bonus on betvisa com!
Cockfight to win up to 3,888,000 on betvisa game
Daily Deposit, Sunday Bonus on betvisa app 888,000!
#betvisavietnam
200% Bonus on instant deposits—start your win streak!
200% welcome bonus! Slots and Fishing Games
https://www.betvisa.com/
#betvisavietnam #betvisagame #betvisaapp
#betvisacom #betvisacasinoapp
Birthday bash? Up to 1,800,000 in prizes! Enjoy!
Friday Shopping Frenzy betvisa vietnam 100,000 VND!
Betvisa C***** App Daily Login 12% Bonus Up to 1,500,000VND!
Khám phá Thế Giới Cá Cược Trực Tuyến với BetVisa!
Dịch vụ BetVisa, một trong những nền tảng hàng đầu tại châu Á, ra đời vào năm 2017 và thao tác dưới phê chuẩn của Curacao, đã thu hút hơn 2 triệu người dùng trên toàn thế giới. Với cam kết đem đến trải nghiệm cá cược đảm bảo và tin cậy nhất, BetVisa nhanh chóng trở thành lựa chọn hàng đầu của người chơi trực tuyến.
BetVisa không chỉ cung cấp các trò chơi phong phú như xổ số, sòng bạc trực tiếp, thể thao trực tiếp và thể thao điện tử, mà còn mang đến cho người chơi những ưu đãi hấp dẫn. Thành viên mới đăng ký sẽ được tặng ngay 5 cơ hội miễn phí và có cơ hội giành giải thưởng lớn.
Đặc biệt, BetVisa hỗ trợ nhiều cách thức thanh toán linh hoạt như Betvisa Vietnam, cùng với các ưu đãi độc quyền như thưởng chào mừng lên đến 200%. Bên cạnh đó, hàng tuần còn có các chương trình khuyến mãi độc đáo như chương trình giải thưởng Sinh Nhật và Chủ Nhật Mua Sắm Điên Cuồng, mang đến cho người chơi cơ hội thắng lớn.
Do tính lời hứa về trải thảo cá cược tốt hơn nhất và dịch vụ khách hàng chuyên môn, BetVisa hoàn toàn tự tin là điểm đến lý tưởng cho những ai phấn khích trò chơi trực tuyến. Hãy ghi danh ngay hôm nay và bắt đầu hành trình của bạn tại BetVisa – nơi niềm vui và may mắn chính là điều quan trọng.
Nice i really enjoyed reading your blogs. Keep on posting. Thanks
robot88
App cá độ:Hướng dẫn tải app cá cược uy tín RG777 đúng cách
Bạn có biết? Tải app cá độ đúng cách sẽ giúp tiết kiệm thời gian đăng nhập, tăng tính an toàn và bảo mật cho tài khoản của bạn! Vậy đâu là cách để tải một app cá cược uy tín dễ dàng và chính xác? Xem ngay bài viết này nếu bạn muốn chơi cá cược trực tuyến an toàn!
tải về ngay lập tức
RG777 – Nhà Cái Uy Tín Hàng Đầu Việt Nam
Link tải app cá độ nét nhất 2023:RG777
Để đảm bảo việc tải ứng dụng cá cược của bạn an toàn và nhanh chóng, người chơi có thể sử dụng đường link sau.
tải về ngay lập tức
Intro
betvisa bangladesh
Betvisa bangladesh | Super Cricket Carnival with Betvisa!
IPL Cricket Mania | Kick off Super Cricket Carnival with bet visa.com
IPL Season | Exclusive 1,50,00,000 only at Betvisa Bangladesh!
Crash Games Heroes | Climb to the top of the 1,00,00,000 bonus pool!
#betvisabangladesh
Preview IPL T20 | Follow Betvisa BD on Facebook, Instagram for awards!
betvisa affiliate Dream Maltese Tour | Sign up now to win the ultimate p****!
https://www.bvthethao.com/
#betvisabangladesh #betvisabd #betvisaaffiliate
#betvisaaffiliatesignup #betvisa.com
Do tính lời hứa về trải nghiệm cá cược hoàn hảo nhất và dịch vụ khách hàng kỹ năng chuyên môn, BetVisa tự hào là điểm đến lý tưởng cho những ai phấn khích trò chơi trực tuyến. Hãy ghi danh ngay hôm nay và bắt đầu hành trình của bạn tại BetVisa – nơi niềm vui và may mắn chính là điều tất yếu.
Tìm hiểu Thế Giới Cá Cược Trực Tuyến với BetVisa!
BetVisa Vietnam, một trong những công ty trò chơi hàng đầu tại châu Á, được thành lập vào năm 2017 và hoạt động dưới giấy phép của Curacao, đã đưa vào hơn 2 triệu người dùng trên toàn thế giới. Với lời hứa đem đến trải nghiệm cá cược an toàn và tin cậy nhất, BetVisa nhanh chóng trở thành lựa chọn hàng đầu của người chơi trực tuyến.
BetVisa không chỉ cung cấp các trò chơi phong phú như xổ số, sòng bạc trực tiếp, thể thao trực tiếp và thể thao điện tử, mà còn mang đến cho người chơi những ưu đãi hấp dẫn. Thành viên mới đăng ký sẽ được tặng ngay 5 phần quà miễn phí và có cơ hội giành giải thưởng lớn.
Đặc biệt, BetVisa hỗ trợ nhiều hình thức thanh toán linh hoạt như Betvisa Vietnam, cùng với các ưu đãi độc quyền như thưởng chào mừng lên đến 200%. Bên cạnh đó, hàng tuần còn có các chương trình khuyến mãi độc đáo như chương trình giải thưởng Sinh Nhật và Chủ Nhật Mua Sắm Điên Cuồng, mang đến cho người chơi cơ hội thắng lớn.
exprimegranada.com
この記事は非常に有益でした。感謝します!
ananin amina ayagimi sokucam az kaldi
JDBslot
JDB slot | The first bonus to rock the slot world
Exclusive event to earn real money and slot game points
JDB demo slot games for free = ?? Lucky Spin Lucky Draw!
How to earn reels free 2000? follow jdb slot games for free
#jdbslot
Demo making money : https://jdb777.com
#jdbslot #slotgamesforfree #howtoearnreels #cashreels
#slotgamepoint #demomakingmoney
Cash reels only at slot games for free
More professional jdb game bonus knowledge
Methods to Gain Rotations Points Costless 2000: Your Greatest Instruction to Victorious Large with JDB Machines
Are you you ready to embark on an exhilarating expedition into the world of internet slot games? Hunt no further, just spin to JDB777 FreeGames, where excitement and large wins anticipate you at every single turn of the reel. In this thorough handbook, we’ll show you how to secure reels credits free 2000 and unlock the exciting world of JDB slots.
Undergo the Adrenaline rush of Slot Games for Free
At JDB777 FreeGames, we provide a wide range of captivating slot games that are certain to keep you entertained for hours on end. From timeless fruit machines to immersive themed slots, there’s something for every kind of player to enjoy. And the greatest part? You can play all of our slot games for free and win real cash prizes!
Uncover Free Cash Reels and Win Big
One of the most exciting features of JDB777 FreeGames is the opportunity to earn reels points gratis 2000, which can be exchanged for real cash. Simply sign up for an account, and you’ll obtain your costless bonus to initiate spinning and winning. With our plentiful promotions and bonuses, the sky’s the ceiling when it comes to your winnings!
Guide Tactics and Points System
To increase your winnings and open the complete potential of our slot games, it’s vital to comprehend the tactics and points system. Our expert guides will take you through everything you need to know, from selecting the right games to apprehending how to earn bonus points and cash prizes.
Special Promotions and Specific Offers
As a member of JDB777 FreeGames, you’ll have access to exclusive promotions and special offers that are positive to augment your gaming experience. From welcome bonuses to daily rebates, there are a lot of chances to enhance your winnings and take your gameplay to the following level.
Join Us Today and Begin Winning
Don’t miss out on your possibility to win big with JDB777 FreeGames. Sign up now to declare your gratis bonus of 2000 credits and start spinning the reels for your opportunity to win real cash prizes. With our exciting variety of slot games and generous promotions, the potentialities are endless. Join us today and initiate winning!
Way cool! Some very valid points! I appreciate you writing this article and also the rest of the website is also very good.
I used to be able to find good information from your blog posts.
fpparisshop.com
素晴らしい記事で、いつも新鮮な情報を提供してくれて感謝しています。
Your style is unique compared to other people I’ve read stuff from. Thanks for posting when you’ve got the opportunity, Guess I will just bookmark this web site.
thebuzzerpodcast.com
그냥… 말하자면, 거의 모든 사람들의 마음은 여전히 극도로 복잡합니다.
As an established email marketing services agency, we have been working with clients from across the globe. Visit our email template samples page to view our portfolio of email template designs, landing page designs, and banners. You can view any chosen email template’s desktop, mobile, and litmus preview. The litmus preview helps you explore the user experience of the templates on a variety of devices such as Outlook, iPhone, Android, Gmail Chrome, and many more. Generally, the larger your list, the more it costs. Just based on size, some agencies will charge up to $250 for 10,000 subscribers, for one message blast a month. If you don’t intend on sending a lot of emails, this may be fine. But if your list is already approaching the 10,000 level, you’ll likely be charged additional send fees.
https://www.weddingbee.com/members/emailcampaignte
From there, just click on Newsletter and your email will instantly be sent to your Newsletter account. (If you haven’t already connected your Newsletter account via Settings, you’ll need to do so here). In your Newsletter dashboard, you’ll find the message as a new Newsletter template. Moosend has 75+ mobile-ready free newsletter templates waiting for you. Tested in all major email clients.You can sign in here and use the Moosend email template builder to directly edit them online and download the HTML. Moosend is also an ESP (email marketing tool) you can use to send out the emails for free. We provide support for our plugin on WordPress.org forums and through our official forum. Brevo’s free drag-and-drop editor lets you create custom, professional newsletters quickly and easily. A free account includes access to dozens of newsletter templates as well as features like contact management, marketing automation, and transactional emails SMS.
busty English real cams show with a fun and wild personality
virtual terminal credit card
A great post without any doubt.
buysteriodsonline.com
Hongzhi 황제는 “내가 왕위에 올랐을 때 몇 명의 시녀가 폐지 되었습니까? “라고 말했습니다.
exprimegranada.com
この記事から多くを学びました。非常に感謝しています。
I love looking through a post that can make men and women think. Also, thank you for allowing me to comment.
This site was… how do I say it? Relevant!! Finally I have found something that helped me. Thanks.
Way cool! Some very valid points! I appreciate you penning this post and the rest of the website is also very good.
lacolinaecuador.com
결국… 그녀에게 붙잡힌 사람은 평생의 이름이었다.
I needed to thank you for this wonderful read!! I certainly enjoyed every little bit of it. I’ve got you book marked to check out new stuff you post…
cougarsbkjersey.com
いつも新鮮で興味深い視点を提供してくれてありがとう。
I’m genuinely thrilled about stumbling upon this gem!
En Son Dönemsel En Büyük Beğenilen Bahis Sitesi: Casibom
Kumarhane oyunlarını sevenlerin artık duymuş olduğu Casibom, en son dönemde adından çoğunlukla söz ettiren bir bahis ve oyun sitesi haline geldi. Ülkemizin en iyi bahis web sitelerinden biri olarak tanınan Casibom’un haftalık göre değişen açılış adresi, piyasada oldukça taze olmasına rağmen emin ve kazandıran bir platform olarak öne çıkıyor.
Casibom, muadillerini geride bırakarak eski kumarhane web sitelerinin üstünlük sağlamayı başarmayı sürdürüyor. Bu pazarda köklü olmak gereklidir olsa da, oyunculardan iletişim kurmak ve onlara temasa geçmek da eş miktar önemli. Bu noktada, Casibom’un 7/24 servis veren canlı olarak destek ekibi ile kolayca iletişime geçilebilir olması büyük önem taşıyan bir fayda sağlıyor.
Hızlıca artan katılımcı kitlesi ile ilgi çekici olan Casibom’un arka planında başarı faktörleri arasında, yalnızca c***** ve gerçek zamanlı c***** oyunları ile sınırlı kısıtlı olmayan kapsamlı bir hizmet yelpazesi bulunuyor. Spor bahislerinde sunduğu geniş alternatifler ve yüksek oranlar, oyuncuları ilgisini çekmeyi başarıyor.
Ayrıca, hem spor bahisleri hem de kumarhane oyunlar katılımcılara yönelik sunulan yüksek yüzdeli avantajlı bonuslar da dikkat çekici. Bu nedenle, Casibom kısa sürede alanında iyi bir reklam başarısı elde ediyor ve büyük bir katılımcı kitlesi kazanıyor.
Casibom’un kar getiren ödülleri ve popülerliği ile birlikte, web sitesine üyelik hangi yollarla sağlanır sorusuna da değinmek elzemdir. Casibom’a hareketli cihazlarınızdan, bilgisayarlarınızdan veya tabletlerinizden internet tarayıcı üzerinden rahatça erişilebilir. Ayrıca, platformun mobil uyumlu olması da önemli bir artı sağlıyor, çünkü artık pratikte herkesin bir akıllı telefonu var ve bu akıllı telefonlar üzerinden hızlıca erişim sağlanabiliyor.
Mobil tabletlerinizle bile yolda canlı iddialar alabilir ve müsabakaları gerçek zamanlı olarak izleyebilirsiniz. Ayrıca, Casibom’un mobil cihazlarla uyumlu olması, ülkemizde kumarhane ve oyun gibi yerlerin meşru olarak kapatılmasıyla birlikte bu tür platformlara erişimin önemli bir yolunu oluşturuyor.
Casibom’un emin bir kumarhane platformu olması da gereklidir bir avantaj getiriyor. Belgeli bir platform olan Casibom, kesintisiz bir şekilde eğlence ve kazanç elde etme imkanı getirir.
Casibom’a üye olmak da oldukça basittir. Herhangi bir belge şartı olmadan ve ücret ödemeden siteye kolaylıkla üye olabilirsiniz. Ayrıca, site üzerinde para yatırma ve çekme işlemleri için de birçok farklı yöntem bulunmaktadır ve herhangi bir kesim ücreti alınmamaktadır.
Ancak, Casibom’un güncel giriş adresini izlemek de önemlidir. Çünkü canlı şans ve c***** web siteleri popüler olduğu için yalancı siteler ve dolandırıcılar da görünmektedir. Bu nedenle, Casibom’un sosyal medya hesaplarını ve güncel giriş adresini periyodik olarak kontrol etmek elzemdir.
Sonuç, Casibom hem güvenilir hem de kar getiren bir kumarhane web sitesi olarak ilgi çekiyor. Yüksek ödülleri, geniş oyun alternatifleri ve kullanıcı dostu taşınabilir uygulaması ile Casibom, c***** tutkunları için mükemmel bir platform sunuyor.
thewiin.com
이… 모두의 눈알이 떨어질 지경입니다.
This is pure magic! I’m completely hooked!
I’m genuinely excited about this brilliant find!
Unparalleled brilliance! A one-of-a-kind discovery!
Remarkable post! The author’s skills are commendable!
Fantastic content! The author knows how to captivate the audience!
bmipas.com
生活に直接役立つ実用的な情報が満載で、大変感謝しています。
After going over a number of the blog articles on your web page, I honestly appreciate your way of writing a blog. I book marked it to my bookmark webpage list and will be checking back soon. Take a look at my website as well and let me know how you feel.
casibom giriş
En Son Dönemin En Büyük Beğenilen Kumarhane Platformu: Casibom
Bahis oyunlarını sevenlerin artık duymuş olduğu Casibom, en son dönemde adından sıkça söz ettiren bir bahis ve c***** platformu haline geldi. Ülkemizdeki en iyi kumarhane platformlardan biri olarak tanınan Casibom’un haftalık olarak cinsinden değişen erişim adresi, sektörde oldukça yeni olmasına rağmen emin ve kar getiren bir platform olarak tanınıyor.
Casibom, yakın rekabeti olanları geride bırakarak köklü kumarhane platformların önüne geçmeyi başarıyor. Bu sektörde eski olmak önemlidir olsa da, katılımcılarla etkileşimde olmak ve onlara erişmek da eş kadar önemli. Bu durumda, Casibom’un 7/24 hizmet veren gerçek zamanlı destek ekibi ile rahatça iletişime geçilebilir olması büyük bir avantaj sunuyor.
Süratle genişleyen katılımcı kitlesi ile dikkat çekici olan Casibom’un gerisindeki başarılı faktörleri arasında, sadece kumarhane ve gerçek zamanlı c***** oyunlarına sınırlı kısıtlı olmayan geniş bir hizmetler yelpazesi bulunuyor. Spor bahislerinde sunduğu geniş seçenekler ve yüksek oranlar, oyuncuları cezbetmeyi başarılı oluyor.
Ayrıca, hem sporcular bahisleri hem de bahis oyunları katılımcılara yönlendirilen sunulan yüksek yüzdeli avantajlı bonuslar da ilgi çekiyor. Bu nedenle, Casibom hızla piyasada iyi bir reklam başarısı elde ediyor ve önemli bir katılımcı kitlesi kazanıyor.
Casibom’un kazanç sağlayan bonusları ve popülerliği ile birlikte, platforma abonelik hangi yollarla sağlanır sorusuna da bahsetmek gereklidir. Casibom’a taşınabilir cihazlarınızdan, bilgisayarlarınızdan veya tabletlerinizden web tarayıcı üzerinden kolaylıkla erişilebilir. Ayrıca, sitenin mobil uyumlu olması da önemli bir fayda sunuyor, çünkü artık pratikte herkesin bir akıllı telefonu var ve bu telefonlar üzerinden hızlıca giriş sağlanabiliyor.
Mobil tabletlerinizle bile yolda canlı olarak bahisler alabilir ve yarışmaları canlı olarak izleyebilirsiniz. Ayrıca, Casibom’un mobil uyumlu olması, memleketimizde kumarhane ve c***** gibi yerlerin yasal olarak kapatılmasıyla birlikte bu tür platformlara erişimin önemli bir yolunu oluşturuyor.
Casibom’un emin bir bahis sitesi olması da önemlidir bir fayda getiriyor. Lisanslı bir platform olan Casibom, duraksız bir şekilde eğlence ve kazanç elde etme imkanı sunar.
Casibom’a kullanıcı olmak da oldukça basittir. Herhangi bir belge koşulu olmadan ve ücret ödemeden platforma kolaylıkla kullanıcı olabilirsiniz. Ayrıca, site üzerinde para yatırma ve çekme işlemleri için de birçok farklı yöntem vardır ve herhangi bir kesim ücreti alınmamaktadır.
Ancak, Casibom’un güncel giriş adresini takip etmek de gereklidir. Çünkü canlı bahis ve c***** platformlar popüler olduğu için sahte web siteleri ve dolandırıcılar da ortaya çıkmaktadır. Bu nedenle, Casibom’un sosyal medya hesaplarını ve güncel giriş adresini periyodik olarak kontrol etmek önemlidir.
Sonuç olarak, Casibom hem itimat edilir hem de kazandıran bir c***** platformu olarak dikkat çekiyor. yüksek promosyonları, kapsamlı oyun alternatifleri ve kullanıcı dostu taşınabilir uygulaması ile Casibom, oyun tutkunları için ideal bir platform sunuyor.
ilogidis.com
Hongzhi 황제는 차갑게 말했습니다. “하지만 내가 허용하지 않으면.”
I’m feeling so connected to the author’s message in this post!
May I simply say what a comfort to uncover someone that genuinely knows what they’re discussing on the web. You certainly understand how to bring an issue to light and make it important. More and more people have to look at this and understand this side of your story. It’s surprising you’re not more popular since you definitely have the gift.
toasterovensplus.com
この記事は心に響きました。とても感動しました。
This is a topic that’s close to my heart… Thank you! Exactly where can I find the contact details for questions?
veganchoicecbd.com
정말 무서운 숫자입니다. 이것은 앞뒤로의 여행 일뿐입니다.
Проверка Tether для чистоту: Каковым способом обезопасить свои криптовалютные активы
Постоянно все больше граждан придают важность к секурити личных электронных финансов. Каждый день дельцы предлагают новые методы кражи криптовалютных средств, и также собственники электронной валюты являются жертвами их афер. Один из подходов охраны становится проверка кошельков в присутствие нелегальных денег.
Зачем это потребуется?
Преимущественно, для того чтобы обезопасить личные финансы от обманщиков и также похищенных монет. Многие специалисты встречаются с вероятностью убытков своих активов из-за мошеннических схем или хищений. Проверка бумажников позволяет определить подозрительные операции или предотвратить потенциальные убытки.
Что наша команда предлагаем?
Наша компания предоставляем подход анализа криптовалютных бумажников и операций для обнаружения источника денег. Наша технология анализирует информацию для выявления противозаконных операций и также проценки риска для вашего портфеля. Из-за данной проверке, вы сможете избегнуть проблем с регуляторами или предохранить себя от участия в незаконных операциях.
Как это работает?
Наша фирма сотрудничаем с передовыми проверочными организациями, вроде Certik, чтобы обеспечить точность наших тестирований. Мы внедряем новейшие техники для выявления опасных транзакций. Ваши информация обрабатываются и хранятся согласно с высокими стандартами безопасности и приватности.
Как проверить свои Tether для прозрачность?
В случае если вы желаете убедиться, что ваши Tether-бумажники чисты, наш подход предоставляет бесплатную проверку первых пяти кошельков. Просто введите адрес своего кошелька в нашем сайте, и также мы предложим вам детальный отчет об его положении.
Защитите свои средства уже сейчас!
Не подвергайте риску подвергнуться мошенников либо оказаться в неприятную ситуацию вследствие противозаконных транзакций. Обратитесь к нам, для того чтобы предохранить свои электронные финансовые ресурсы и предотвратить неприятностей. Предпримите первый шаг к безопасности вашего криптовалютного портфеля уже сегодня!
九州娛樂城
cá cược thể thao
cá cược thể thao
Осмотр USDT на чистоту: Как обезопасить свои цифровые состояния
Все больше пользователей обращают внимание в безопасность личных электронных финансов. День ото дня дельцы придумывают новые методы кражи криптовалютных активов, или владельцы цифровой валюты становятся страдающими их подстав. Один методов обеспечения безопасности становится проверка кошельков на присутствие противозаконных средств.
Для чего это полезно?
Преимущественно, с тем чтобы защитить личные средства от шарлатанов или украденных монет. Многие участники сталкиваются с потенциальной угрозой убытков своих финансов в результате обманных механизмов либо грабежей. Проверка бумажников способствует определить непрозрачные операции а также предотвратить возможные убытки.
Что мы предлагаем?
Мы предлагаем сервис тестирования электронных кошельков и операций для обнаружения начала денег. Наша система анализирует информацию для выявления нелегальных операций и также оценки риска для вашего портфеля. Вследствие такой проверке, вы сможете избегнуть проблем с регулированием и обезопасить себя от участия в противозаконных операциях.
Как это действует?
Мы работаем с первоклассными проверочными организациями, вроде Certik, чтобы гарантировать аккуратность наших тестирований. Мы используем передовые технологии для выявления опасных сделок. Ваши данные обрабатываются и сохраняются в соответствии с высокими нормами безопасности и конфиденциальности.
Как проверить свои Tether для прозрачность?
Если хотите проверить, что ваши Tether-кошельки чисты, наш сервис предоставляет бесплатную проверку первых пяти кошельков. Легко вбейте место вашего кошелька в на нашем веб-сайте, и также наш сервис предоставим вам подробный отчет об его положении.
Обезопасьте ваши фонды уже сейчас!
Избегайте риска стать жертвой дельцов либо оказаться в неприятную ситуацию вследствие незаконных операций. Обратитесь к нашей команде, для того чтобы обезопасить ваши криптовалютные активы и предотвратить затруднений. Примите первый шаг к сохранности вашего криптовалютного портфеля уже сегодня!
creating articles
Creating unique articles on Medium and Telegraph, why it is essential:
Created article on these resources is superior ranked on less frequent queries, which is very important to get organic traffic.
We get:
organic traffic from search algorithms.
organic traffic from the inner rendition of the medium.
The platform to which the article refers gets a link that is liquid and increases the ranking of the webpage to which the article refers.
Articles can be made in any amount and choose all low-frequency queries on your topic.
Medium pages are indexed by search algorithms very well.
Telegraph pages need to be indexed individually indexer and at the same time after indexing they sometimes occupy positions higher in the search engines than the medium, these two platforms are very useful for getting visitors.
Here is a hyperlink to our services where we offer creation, indexing of sites, articles, pages and more.
cougarsbkjersey.com
非常に興味深い記事でした。新たな知識をありがとう。
lacolinaecuador.com
누군가 눈살을 찌푸렸다. “설마… 시공이라니…”
This is a topic that’s near to my heart… Thank you! Where can I find the contact details for questions?
I blog quite often and I seriously appreciate your information. The article has really peaked my interest. I am going to book mark your blog and keep checking for new details about once per week. I opted in for your Feed as well.
vảy gà
Can I simply say what a relief to find somebody who genuinely knows what they’re discussing over the internet. You definitely realize how to bring an issue to light and make it important. More and more people ought to read this and understand this side of the story. I was surprised you’re not more popular given that you definitely possess the gift.
alexisaevansleak, leaked, leakshttps://www.start.gg/user/19170a76
Hello there! I just want to offer you a huge thumbs up for your great information you have right here on this post. I am coming back to your website for more soon.
k8 カジノ 月替わりボーナス
非常に実用的で、具体的な例が豊富なのがとても役立ちます。
animehangover.com
Fang Jifan은이 기사를 선택하고 그것을 검토하는 일부 의사에게 테스트를 지시했습니다.
Max and Justin will go to war for this bout. Both fighters are UFC veterans with differing reputations — Gaethje is power, while Holloway is output — but neither guy is satisfied until he crushes his opponent. Both of these fan favorites have agreed to square off in what will instantly become one of the most anticipated matchups of the year. Justin Gaethje enters this contest off his head-kick knockout over Dustin Poirier to claim the BMF title back in June of last year. Max Holloway will return to Lightweight here for the first time since his loss to Dustin Poirier for the interim title, he is also coming off an insane knockout over Chan Sung Jung in August. Also Read: UFC 286: Justin Gaethje vs Rafael Fiziev- Preview, Prediction, and latest b****** odds
https://en-web-directory.com/listings12701082/pari-matches
The helpful FA app includes daily b****** tips from various guest tipsters, with the Smart Acca feature the ideal tool to search for matches throughout the world that have the greatest chances of landing. Our global expertise ensures you have access to reliable sports b****** picks for all major b****** markets, in every event, across the global sporting schedule, including: B****** on Test matches can be good fun as the format, taking place over such a long period of time, means that momentum changes from team to team a lot over the course of the match. Our team of cricket experts is always working on new algorithms for providing the best b****** tips for Test format matches. The difference between b****** on Tests rather than T20s is that you will have to wait longer for the game to end and for your winning wagers to be settled by the bookmakers, of course!
This is a topic that’s near to my heart… Cheers! Where are your contact details though?
Saved as a favorite, I love your site!
Having read this I believed it was rather informative. I appreciate you spending some time and energy to put this information together. I once again find myself personally spending a significant amount of time both reading and commenting. But so what, it was still worthwhile!
Having read this I thought it was really informative. I appreciate you spending some time and effort to put this informative article together. I once again find myself personally spending a significant amount of time both reading and posting comments. But so what, it was still worthwhile!
Pretty! This has been a really wonderful article. Many thanks for supplying these details.
mikaspa.com
Hongzhi 황제는 요즘 고통이 조금 완화되었다고 느꼈습니다.
Как охранять свои данные: остерегайтесь утечек информации в интернете. Сегодня обеспечение безопасности своих данных становится всё значимее важной задачей. Одним из наиболее часто встречающихся способов утечки личной информации является слив «сит фраз» в интернете. Что такое сит фразы и в каком объеме защититься от их утечки? Что такое «сит фразы»? «Сит фразы» — это комбинации слов или фраз, которые бывают используются для входа к различным онлайн-аккаунтам. Эти фразы могут включать в себя имя пользователя, пароль или дополнительные конфиденциальные данные. Киберпреступники могут пытаться получить доступ к вашим аккаунтам, с помощью этих сит фраз. Как защитить свои личные данные? Используйте непростые пароли. Избегайте использования очевидных паролей, которые легко угадать. Лучше всего использовать комбинацию букв, цифр и символов. Используйте уникальные пароли для всего аккаунта. Не применяйте один и тот же пароль для разных сервисов. Используйте двухэтапную аутентификацию (2FA). Это вводит дополнительный уровень безопасности, требуя подтверждение входа на ваш аккаунт посредством другое устройство или метод. Будьте осторожны с онлайн-сервисами. Не доверяйте свою информацию ненадежным сайтам и сервисам. Обновляйте программное обеспечение. Установите обновления для вашего операционной системы и программ, чтобы защитить свои данные от вредоносного ПО. Вывод Слив сит фраз в интернете может спровоцировать серьезным последствиям, таким вроде кража личной информации и финансовых потерь. Чтобы сохранить себя, следует принимать меры предосторожности и использовать надежные методы для хранения и управления своими личными данными в сети
k8 カジノ 絵師
情報が豊富で読み応えがありました。非常に有益です。
Thank you for sharing indeed great looking !
Player線上娛樂城遊戲指南與評測
台灣最佳線上娛樂城遊戲的終極指南!我們提供專業評測,分析熱門老虎機、百家樂、棋牌及其他賭博遊戲。從遊戲規則、策略到選擇最佳娛樂城,我們全方位覆蓋,協助您更安全的遊玩。
Player如何評測:公正與專業的評分標準
在【Player娛樂城遊戲評測網】我們致力於為玩家提供最公正、最專業的娛樂城評測。我們的評測過程涵蓋多個關鍵領域,旨在確保玩家獲得可靠且全面的信息。以下是我們評測娛樂城的主要步驟:
娛樂城是什麼?
娛樂城是什麼?娛樂城是台灣對於線上賭場的特別稱呼,線上賭場分為幾種:現金版、信用版、手機娛樂城(娛樂城APP),一般來說,台灣人在稱娛樂城時,是指現金版線上賭場。
線上賭場在別的國家也有別的名稱,美國 – C*****, G*******、中國 – 线上赌场,娱乐城、日本 – オンラインカジノ、越南 – Nhà cái。
娛樂城會被抓嗎?
在台灣,根據刑法第266條,不論是實體或線上賭博,參與賭博的行為可處最高5萬元罰金。而根據刑法第268條,為賭博提供場所並意圖營利的行為,可能面臨3年以下有期徒刑及最高9萬元罰金。一般賭客若被抓到,通常被視為輕微罪行,原則上不會被判處監禁。
信用版娛樂城是什麼?
信用版娛樂城是一種線上賭博平台,其中的賭博活動不是直接以現金進行交易,而是基於信用系統。在這種模式下,玩家在進行賭博時使用虛擬的信用點數或籌碼,這些點數或籌碼代表了一定的貨幣價值,但實際的金錢交易會在賭博活動結束後進行結算。
現金版娛樂城是什麼?
現金版娛樂城是一種線上博弈平台,其中玩家使用實際的金錢進行賭博活動。玩家需要先存入真實貨幣,這些資金轉化為平台上的遊戲籌碼或信用,用於參與各種賭場遊戲。當玩家贏得賭局時,他們可以將這些籌碼或信用兌換回現金。
娛樂城體驗金是什麼?
娛樂城體驗金是娛樂場所為新客戶提供的一種免費遊玩資金,允許玩家在不需要自己投入任何資金的情況下,可以進行各類遊戲的娛樂城試玩。這種體驗金的數額一般介於100元到1,000元之間,且對於如何使用這些體驗金以達到提款條件,各家娛樂城設有不同的規則。
взлом кошелька
Как обезопасить свои данные: берегитесь утечек информации в интернете. Сегодня обеспечение безопасности личных данных становится все более важной задачей. Одним из наиболее популярных способов утечки личной информации является слив «сит фраз» в интернете. Что такое сит фразы и в каком объеме защититься от их утечки? Что такое «сит фразы»? «Сит фразы» — это комбинации слов или фраз, которые бывают используются для доступа к различным онлайн-аккаунтам. Эти фразы могут включать в себя имя пользователя, пароль или дополнительные конфиденциальные данные. Киберпреступники могут пытаться получить доступ к вашим аккаунтам, используя этих сит фраз. Как сохранить свои личные данные? Используйте комплексные пароли. Избегайте использования очевидных паролей, которые просто угадать. Лучше всего использовать комбинацию букв, цифр и символов. Используйте уникальные пароли для каждого из аккаунта. Не применяйте один и тот же пароль для разных сервисов. Используйте двухфакторную проверку (2FA). Это добавляет дополнительный уровень безопасности, требуя подтверждение входа на ваш аккаунт через другое устройство или метод. Будьте осторожны с онлайн-сервисами. Не доверяйте свою информацию ненадежным сайтам и сервисам. Обновляйте программное обеспечение. Установите обновления для вашего операционной системы и программ, чтобы сохранить свои данные от вредоносного ПО. Вывод Слив сит фраз в интернете может повлечь за собой серьезным последствиям, таким как кража личной информации и финансовых потерь. Чтобы сохранить себя, следует принимать меры предосторожности и использовать надежные методы для хранения и управления своими личными данными в сети
слив сид фраз
Слив засеянных фраз (seed phrases) является одной из наиболее распространенных способов утечки личных информации в мире криптовалют. В этой статье мы разберем, что такое сид фразы, по какой причине они важны и как можно защититься от их утечки.
Что такое сид фразы?
Сид фразы, или мнемонические фразы, представляют собой комбинацию слов, которая используется для создания или восстановления кошелька криптовалюты. Обычно сид фраза состоит из 12 или 24 слов, которые являются собой ключ к вашему кошельку. Потеря или утечка сид фразы может приводить к потере доступа к вашим криптовалютным средствам.
Почему важно защищать сид фразы?
Сид фразы представляют собой ключевым элементом для безопасного хранения криптовалюты. Если злоумышленники получат доступ к вашей сид фразе, они смогут получить доступ к вашему кошельку и украсть все средства.
Как защититься от утечки сид фраз?
Никогда не передавайте свою сид фразу ничьему, даже если вам происходит, что это доверенное лицо или сервис.
Храните свою сид фразу в защищенном и секурном месте. Рекомендуется использовать аппаратные кошельки или специальные программы для хранения сид фразы.
Используйте дополнительные методы защиты, такие как двухэтапная проверка, для усиления безопасности вашего кошелька.
Регулярно делайте резервные копии своей сид фразы и храните их в других безопасных местах.
Заключение
Слив сид фраз является существенной угрозой для безопасности владельцев криптовалют. Понимание важности защиты сид фразы и принятие соответствующих мер безопасности помогут вам избежать потери ваших криптовалютных средств. Будьте бдительны и обеспечивайте надежную защиту своей сид фразы
buysteriodsonline.com
Fang Jifan은 “이게 무슨 악이야? “라고 한숨을 쉬었습니다.
This is the right webpage for everyone who wants to understand this topic. You know so much its almost tough to argue with you (not that I really would want to…HaHa). You certainly put a brand new spin on a topic that’s been written about for years. Wonderful stuff, just wonderful.
This website certainly has all of the information and facts I needed about this subject and didn’t know who to ask.
|The passion the author has for the subject is palpable.
هنا النص مع استخدام السبينتاكس:
“بنية الروابط الخلفية
بعد التحديثات العديدة لمحرك البحث G، تحتاج إلى تنفيذ خيارات ترتيب مختلفة.
هناك طريقة لجذب انتباه محركات البحث إلى موقعك على الويب باستخدام الروابط الخلفية.
الروابط الخلفية ليست فقط أداة فعالة للترويج، ولكن تمتلك أيضًا حركة مرور عضوية، والمبيعات المباشرة من هذه الموارد على الأرجح قد لا تكون كذلك، ولكن التغييرات ستكون، وهي حركة المرور التي نحصل عليها أيضًا.
ما سنحصل عليه في النهاية في النهاية في الإخراج:
نعرض الموقع لمحركات البحث من خلال الروابط الخلفية.
2- نحصل على تبديلات عضوية إلى الموقع، وهي أيضًا إشارة لمحركات البحث أن المورد يستخدمه الناس.
كيف نظهر لمحركات البحث أن الموقع سائل:
1 يتم عمل لينك خلفي للصفحة الرئيسية حيث المعلومات الرئيسية
نقوم بعمل وصلات خلفية من خلال عمليات توجيه مرة أخرى المواقع الموثوقة
الأهم من ذلك أننا نضع الموقع على أداة منفصلة من أدوات تحليل المواقع، ويدخل الموقع في ذاكرة التخزين المؤقت لهذه المحللات، ثم الروابط المستلمة التي نضعها كتوجيه على المدونات والمنتديات والتعليقات.
هذا الإجراء المهم يُظهر لمحركات البحث خارطة الموقع، حيث تعرض أدوات تحليل المواقع جميع المعلومات عن المواقع مع جميع الكلمات الرئيسية والعناوين وهو أمر جيد جداً
جميع المعلومات عن خدماتنا على الموقع!
Spot on with this write-up, I actually feel this site needs a lot more attention. I’ll probably be back again to see more, thanks for the advice!
bestmanualpolesaw.com
많은 사람들이 “편집자님 감사합니다. 편집자님의 친절함이 대단합니다…”라며 고개를 숙였습니다.
Hi to all, how is all, I think every one is getting more from this web page,
and your views are fastidious for new visitors.
k8 カジノ 銀行入金
このトピックについてこんなに詳しく書かれた記事は初めてです。素晴らしいです!
Este site é uma referência em termos de segurança e confiabilidade online. A cada clique, minha confiança nele só aumenta. Recomendo a todos!
veganchoicecbd.com
뒤에 있던 제자들도 부끄러워했습니다.그들과 함께 온 군마들이 즉시 경계하기 시작했습니다.
A segurança e a confiabilidade deste site são incomparáveis. É um alívio saber que posso contar com ele para minhas necessidades online. Obrigado por manter os mais altos padrões!
Have you ever considered writing an e-book or guest authoring on other websites?
I have a blog based upon on the same topics you discuss
and would really like to have you share some stories/information. I know my audience would appreciate your work.
If you’re even remotely interested, feel free to shoot me an email.
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
Your publication was like a burst of sunshine in my daily routine. Keep brightening our days with your positivity!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
Your post brought a genuine smile to my face. Keep filling our days with that contagious joy!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
I never expected a post to have such a profound impact on my day. Keep the magic alive in your content!
zanetvize.com
Fang Jifan의 얼굴은 상대적으로 잘 생겼지 만 얼핏 보면 도발하기 쉽지 않은 치열한 얼굴을 가지고 있습니다.
rikvip
Rikvip Club: Trung Tâm Giải Trí Trực Tuyến Hàng Đầu tại Việt Nam
Rikvip Club là một trong những nền tảng giải trí trực tuyến hàng đầu tại Việt Nam, cung cấp một loạt các trò chơi hấp dẫn và dịch vụ cho người dùng. Cho dù bạn là người dùng iPhone hay Android, Rikvip Club đều có một cái gì đó dành cho mọi người. Với sứ mạng và mục tiêu rõ ràng, Rikvip Club luôn cố gắng cung cấp những sản phẩm và dịch vụ tốt nhất cho khách hàng, tạo ra một trải nghiệm tiện lợi và thú vị cho người chơi.
Sứ Mạng và Mục Tiêu của Rikvip
Từ khi bắt đầu hoạt động, Rikvip Club đã có một kế hoạch kinh doanh rõ ràng, luôn nỗ lực để cung cấp cho khách hàng những sản phẩm và dịch vụ tốt nhất và tạo điều kiện thuận lợi nhất cho người chơi truy cập. Nhóm quản lý của Rikvip Club có những mục tiêu và ước muốn quyết liệt để biến Rikvip Club thành trung tâm giải trí hàng đầu trong lĩnh vực game đổi thưởng trực tuyến tại Việt Nam và trên toàn cầu.
Trải Nghiệm Live C*****
Rikvip Club không chỉ nổi bật với sự đa dạng của các trò chơi đổi thưởng mà còn với các phòng trò chơi c***** trực tuyến thu hút tất cả người chơi. Môi trường này cam kết mang lại trải nghiệm chuyên nghiệp với tính xanh chín và sự uy tín không thể nghi ngờ. Đây là một sân chơi lý tưởng cho những người yêu thích thách thức bản thân và muốn tận hưởng niềm vui của chiến thắng. Với các sảnh cược phổ biến như Roulette, Sic Bo, Dragon Tiger, người chơi sẽ trải nghiệm những cảm xúc độc đáo và đặc biệt khi tham gia vào c***** trực tuyến.
Phương Thức Thanh Toán Tiện Lợi
Rikvip Club đã được trang bị những công nghệ thanh toán tiên tiến ngay từ đầu, mang lại sự thuận tiện và linh hoạt cho người chơi trong việc sử dụng hệ thống thanh toán hàng ngày. Hơn nữa, Rikvip Club còn tích hợp nhiều phương thức giao dịch khác nhau để đáp ứng nhu cầu đa dạng của người chơi: Chuyển khoản Ngân hàng, Thẻ cào, Ví điện tử…
Kết Luận
Tóm lại, Rikvip Club không chỉ là một nền tảng trò chơi, mà còn là một cộng đồng nơi người chơi có thể tụ tập để tận hưởng niềm vui của trò chơi và cảm giác hồi hộp khi chiến thắng. Với cam kết cung cấp những sản phẩm và dịch vụ tốt nhất, Rikvip Club chắc chắn là điểm đến lý tưởng cho những người yêu thích trò chơi trực tuyến tại Việt Nam và cả thế giới.
I have no words to describe how your content illuminated my day. Keep being that source of inspiration!
Euro 2024
UEFA Euro 2024 Sân Chơi Bóng Đá Hấp Dẫn Nhất Của Châu Âu
Euro 2024 là sự kiện bóng đá lớn nhất của châu Âu, không chỉ là một giải đấu mà còn là một cơ hội để các quốc gia thể hiện tài năng, sự đoàn kết và tinh thần cạnh tranh.
Euro 2024 hứa hẹn sẽ mang lại những trận cầu đỉnh cao và kịch tính cho người hâm mộ trên khắp thế giới. Cùng tìm hiểu các thêm thông tin hấp dẫn về giải đấu này tại bài viết dưới đây, gồm:
Nước chủ nhà
Đội tuyển tham dự
Thể thức thi đấu
Thời gian diễn ra
Sân vận động
Euro 2024 sẽ được tổ chức tại Đức, một quốc gia có truyền thống vàng của bóng đá châu Âu.
Đức là một đất nước giàu có lịch sử bóng đá với nhiều thành công quốc tế và trong những năm gần đây, họ đã thể hiện sức mạnh của mình ở cả mặt trận quốc tế và câu lạc bộ.
Việc tổ chức Euro 2024 tại Đức không chỉ là một cơ hội để thể hiện năng lực tổ chức tuyệt vời mà còn là một dịp để giới thiệu văn hóa và sức mạnh thể thao của quốc gia này.
Đội tuyển tham dự giải đấu Euro 2024
Euro 2024 sẽ quy tụ 24 đội tuyển hàng đầu từ châu Âu. Các đội tuyển này sẽ là những đại diện cho sự đa dạng văn hóa và phong cách chơi bóng đá trên khắp châu lục.
Các đội tuyển hàng đầu như Đức, Pháp, Tây Ban Nha, Bỉ, Italy, Anh và Hà Lan sẽ là những ứng viên nặng ký cho chức vô địch.
Trong khi đó, các đội tuyển nhỏ hơn như Iceland, Wales hay Áo cũng sẽ mang đến những bất ngờ và thách thức cho các đối thủ.
Các đội tuyển tham dự được chia thành 6 bảng đấu, gồm:
Bảng A: Đức, Scotland, Hungary và Thuỵ Sĩ
Bảng B: Tây Ban Nha, Croatia, Ý và Albania
Bảng C: Slovenia, Đan Mạch, Serbia và Anh
Bảng D: Ba Lan, Hà Lan, Áo và Pháp
Bảng E: Bỉ, Slovakia, Romania và Ukraina
Bảng F: Thổ Nhĩ Kỳ, Gruzia, Bồ Đào Nha và Cộng hoà Séc
For s** toys to do a good job, they need to have a few important features. Here are some of the most popular options that free adult webcams swear by, and the reasons why these adult products are so great.
Euro
UEFA Euro 2024 Sân Chơi Bóng Đá Hấp Dẫn Nhất Của Châu Âu
Euro 2024 là sự kiện bóng đá lớn nhất của châu Âu, không chỉ là một giải đấu mà còn là một cơ hội để các quốc gia thể hiện tài năng, sự đoàn kết và tinh thần cạnh tranh.
Euro 2024 hứa hẹn sẽ mang lại những trận cầu đỉnh cao và kịch tính cho người hâm mộ trên khắp thế giới. Cùng tìm hiểu các thêm thông tin hấp dẫn về giải đấu này tại bài viết dưới đây, gồm:
Nước chủ nhà
Đội tuyển tham dự
Thể thức thi đấu
Thời gian diễn ra
Sân vận động
Euro 2024 sẽ được tổ chức tại Đức, một quốc gia có truyền thống vàng của bóng đá châu Âu.
Đức là một đất nước giàu có lịch sử bóng đá với nhiều thành công quốc tế và trong những năm gần đây, họ đã thể hiện sức mạnh của mình ở cả mặt trận quốc tế và câu lạc bộ.
Việc tổ chức Euro 2024 tại Đức không chỉ là một cơ hội để thể hiện năng lực tổ chức tuyệt vời mà còn là một dịp để giới thiệu văn hóa và sức mạnh thể thao của quốc gia này.
Đội tuyển tham dự giải đấu Euro 2024
Euro 2024 sẽ quy tụ 24 đội tuyển hàng đầu từ châu Âu. Các đội tuyển này sẽ là những đại diện cho sự đa dạng văn hóa và phong cách chơi bóng đá trên khắp châu lục.
Các đội tuyển hàng đầu như Đức, Pháp, Tây Ban Nha, Bỉ, Italy, Anh và Hà Lan sẽ là những ứng viên nặng ký cho chức vô địch.
Trong khi đó, các đội tuyển nhỏ hơn như Iceland, Wales hay Áo cũng sẽ mang đến những bất ngờ và thách thức cho các đối thủ.
Các đội tuyển tham dự được chia thành 6 bảng đấu, gồm:
Bảng A: Đức, Scotland, Hungary và Thuỵ Sĩ
Bảng B: Tây Ban Nha, Croatia, Ý và Albania
Bảng C: Slovenia, Đan Mạch, Serbia và Anh
Bảng D: Ba Lan, Hà Lan, Áo và Pháp
Bảng E: Bỉ, Slovakia, Romania và Ukraina
Bảng F: Thổ Nhĩ Kỳ, Gruzia, Bồ Đào Nha và Cộng hoà Séc
k8 カジノ 日替わり ボーナス
この記事は実用性が高くて、本当に助かります!
jeetwin login
thephotoretouch.com
양야의 얼굴은 잿빛이었지만 반박할 수는 없었다.
카지노사이트
Your post is a beacon of positivity this beautiful Monday. The insights provided are invaluable and uplifting. Adding more visuals might just be the cherry on top for future posts.
I’m delighted by your post and its celebration of this wonderful Monday. The content is both insightful and uplifting. Adding more visuals could make it even more engaging for a wider audience.
What a brilliant way to start the week with your post! This Monday feels even more special thanks to your words. I’m curious if you’ll add more visuals in the future, as it could enhance the storytelling.
This is a very comprehensive and well-rounded piece.
onair2tv.com
내장을 빼면 장마비를 고칠 수 있다고 해서 많은 환자들이 보내졌다.
Right here is the perfect blog for anyone who really wants to understand this topic. You understand a whole lot its almost tough to argue with you (not that I actually will need to…HaHa). You definitely put a new spin on a topic that has been written about for a long time. Wonderful stuff, just wonderful.
That is a very good tip especially to those new to the blogosphere. Brief but very accurate information… Many thanks for sharing this one. A must read post!
k8 ビデオスロット
このブログのファンになりました。これからも素敵な記事を期待しています。
nikontinoll.com
장 황후는 “지판이 왜 안 왔어? “라고 말했다.
mail me on “ageofz8899@outlook.com”
pg slot
הפלטפורמה הווה פלטפורמה פופולרית בארץ לקנייה של מריחואנה באופן אינטרנטי. זו מעניקה ממשק נוח ומאובטח לרכישה וקבלת משלוחים מ מוצרי צמח הקנאביס מרובים. בכתבה זו נסקור עם העיקרון מאחורי הפלטפורמה, איך היא פועלת ומה היתרונות של השימוש בה.
מהי הפלטפורמה?
טלגראס מהווה דרך לרכישת צמח הקנאביס דרך האפליקציה טלגרם. זו נשענת על ערוצי תקשורת וקבוצות טלגראם ספציפיות הקרויות ״טלגראס כיוונים, שם אפשר להרכיב מרחב פריטי צמח הקנאביס ולקבלת אלו ישירותית למשלוח. הערוצים אלו מאורגנים על פי איזורים גיאוגרפיים, כדי לשפר על קבלתם של המשלוחים.
איך זה פועל?
התהליך קל למדי. ראשית, צריך להצטרף לערוץ הטלגראס הנוגע לאזור המגורים. שם ניתן לצפות בתפריטים של הפריטים השונים ולהרכיב את הפריטים הרצויים. לאחר ביצוע ההזמנה וסיום התשלום, השליח יופיע לכתובת שצוינה עם החבילה המוזמנת.
מרבית ערוצי טלגראס מספקים טווח נרחב של פריטים – זנים של צמח הקנאביס, עוגיות, שתייה ועוד. בנוסף, אפשר לראות ביקורות מ צרכנים שעברו לגבי רמת הפריטים והשרות.
מעלות השימוש בפלטפורמה
יתרון מרכזי מ האפליקציה הינו הנוחות והדיסקרטיות. ההרכבה והתהליך מתקיימים מרחוק מכל מיקום, בלי נחיצות בהתכנסות פיזי. בנוסף, האפליקציה מאובטחת היטב ומבטיחה חיסיון גבוהה.
נוסף אל זאת, עלויות המוצרים באפליקציה נוטים לבוא זולים, והמשלוחים מגיעים במהירות ובמסירות גבוהה. קיים אף מוקד תמיכה פתוח לכל שאלה או בעיית.
סיכום
טלגראס הווה שיטה חדשנית ויעילה לקנות פריטי צמח הקנאביס במדינה. זו משלבת בין הנוחות הטכנולוגית של האפליקציה הפופולרית, ועם הזריזות והדיסקרטיות מ שיטת השילוח הישירה. ככל שהדרישה לקנאביס גובר, פלטפורמות בדוגמת טלגראס צפויות להמשיך ולצמוח.
k8 パチンコ
こんなに実用的な記事は珍しい。本当に役に立ちました!
Bản cài đặt B29 IOS – Giải pháp vượt trội cho các tín đồ iOS
Trong thế giới công nghệ đầy sôi động hiện nay, trải nghiệm người dùng luôn là yếu tố then chốt. Với sự ra đời của Bản cài đặt B29 IOS, người dùng sẽ được hưởng trọn vẹn những tính năng ưu việt, mang đến sự hài lòng tuyệt đối. Hãy cùng khám phá những ưu điểm vượt trội của bản cài đặt này!
Tính bảo mật tối đa
Bản cài đặt B29 IOS được thiết kế với mục tiêu đảm bảo an toàn dữ liệu tuyệt đối cho người dùng. Nhờ hệ thống mã hóa hiện đại, thông tin cá nhân và dữ liệu nhạy cảm của bạn luôn được bảo vệ an toàn khỏi những kẻ xâm nhập trái phép.
Trải nghiệm người dùng đỉnh cao
Giao diện thân thiện, đơn giản nhưng không kém phần hiện đại, B29 IOS mang đến cho người dùng trải nghiệm duyệt web, truy cập ứng dụng và sử dụng thiết bị một cách trôi chảy, mượt mà. Các tính năng thông minh được tối ưu hóa, giúp nâng cao hiệu suất và tiết kiệm pin đáng kể.
Tính tương thích rộng rãi
Bản cài đặt B29 IOS được phát triển với mục tiêu tương thích với mọi thiết bị iOS từ các dòng iPhone, iPad cho đến iPod Touch. Dù là người dùng mới hay lâu năm của hệ điều hành iOS, B29 đều mang đến sự hài lòng tuyệt đối.
Quá trình cài đặt đơn giản
Với những hướng dẫn chi tiết, việc cài đặt B29 IOS trở nên nhanh chóng và dễ dàng. Chỉ với vài thao tác đơn giản, bạn đã có thể trải nghiệm ngay tất cả những tính năng tuyệt vời mà bản cài đặt này mang lại.
Bản cài đặt B29 IOS không chỉ là một bản cài đặt đơn thuần, mà còn là giải pháp công nghệ hiện đại, nâng tầm trải nghiệm người dùng lên một tầm cao mới. Hãy trở thành một phần của cộng đồng sử dụng B29 IOS để khám phá những tiện ích tuyệt vời mà nó có thể mang lại!
tvlore.com
Zhu Houzhao는 “Daming Palace는 여성 친척 만 점유하고 있으며 목사들이 밤에 거기에 머무르는 것이 불편합니다. “라고 말했습니다.
Проверить перевод usdt trc20
Необходимость верификации транзакции USDT TRC-20
Операции USDT в протокола TRC20 набирают повышенную спрос, вместе с тем важно являться особенно осторожными во время их обработке.
Этот вид транзакций часто задействуется в процессе обеления средств, полученных незаконным образом.
Ключевой факторов риска приобретения USDT по сети TRC20 – подразумевает, что подобные операции вероятно будут зачислены благодаря многочисленных способов мошенничества, включая хищения личных данных, принуждение, кибератаки наряду с прочие противоправные схемы. Зачисляя указанные переводы, получатель автоматически выглядите подельником нелегальной деятельности.
В связи с этим повышенно необходимо тщательно исследовать генезис любых зачисляемого операции через USDT TRC20. Необходимо запрашивать посредством перевододателя данные о правомерности активов, а минимальных сомнениях – не принимать данные платежей.
Учитывайте, в ситуации, когда в обнаружения противоправных происхождений средств, получатель можете быть привлечены с применением взысканиям параллельно вместе с перевододателем. Таким образом целесообразнее подстраховаться как и скрупулезно изучать любой перевод, нежели рисковать собственной репутацией а также оказаться с серьезные судебные трудности.
Поддержание внимательности в процессе операциях с USDT в сети TRC20 – выступает основа собственной материальной сохранности как и защита попадания в нелегальные операции. Будьте бдительными наряду с всегда проверяйте генезис криптовалютных средств.
I really appreciate the time and effort you put into your blog posts.
It’s clear that you’re passionate about it.
Car parking shades in Saudi Arabia
It’s hard to find well-informed people about this topic, however, you sound like you know what you’re talking about! Thanks
thewiin.com
이제 그는 부끄럽고 당황했습니다.
Very good post. I definitely love this website. Stick with it!
Замена венцов красноярск
Геракл24: Профессиональная Реставрация Основания, Венцов, Настилов и Перемещение Строений
Компания Gerakl24 специализируется на предоставлении комплексных сервисов по смене основания, венцов, настилов и переносу зданий в городе Красноярском регионе и за его пределами. Наша группа квалифицированных специалистов обещает отличное качество выполнения различных типов ремонтных работ, будь то из дерева, каркасного типа, кирпичные или бетонные дома.
Плюсы работы с Gerakl24
Квалификация и стаж:
Все работы проводятся исключительно высококвалифицированными специалистами, с обладанием многолетний практику в сфере строительства и ремонта зданий. Наши мастера профессионалы в своем деле и выполняют проекты с высочайшей точностью и вниманием к деталям.
Всесторонний подход:
Мы осуществляем все виды работ по восстановлению и восстановлению зданий:
Замена фундамента: укрепление и замена старого фундамента, что обеспечивает долгий срок службы вашего здания и предотвратить проблемы, связанные с оседанием и деформацией.
Реставрация венцов: восстановление нижних венцов деревянных зданий, которые чаще всего подвергаются гниению и разрушению.
Смена настилов: замена старых полов, что существенно улучшает визуальное восприятие и функциональные характеристики.
Перемещение зданий: безопасное и надежное перемещение зданий на новые локации, что обеспечивает сохранение строения и избегает дополнительных затрат на создание нового.
Работа с любыми типами домов:
Древесные строения: восстановление и укрепление деревянных конструкций, защита от гниения и вредителей.
Каркасные строения: усиление каркасных конструкций и смена поврежденных частей.
Кирпичные строения: ремонт кирпичных стен и укрепление конструкций.
Бетонные строения: реставрация и усиление бетонных элементов, исправление трещин и разрушений.
Надежность и долговечность:
Мы применяем только высококачественные материалы и новейшее оборудование, что обеспечивает долгий срок службы и надежность всех работ. Все наши проекты проходят тщательную проверку качества на каждом этапе выполнения.
Персонализированный подход:
Мы предлагаем каждому клиенту индивидуальные решения, с учетом всех особенностей и пожеланий. Мы стараемся, чтобы итог нашей работы полностью соответствовал вашим ожиданиям и требованиям.
Почему выбирают Геракл24?
Обратившись к нам, вы найдете надежного партнера, который берет на себя все заботы по ремонту и реставрации вашего дома. Мы обеспечиваем выполнение всех проектов в сроки, оговоренные заранее и с в соответствии с нормами и стандартами. Связавшись с Геракл24, вы можете быть спокойны, что ваше строение в надежных руках.
Мы предлагаем консультацию и дать ответы на все вопросы. Звоните нам, чтобы обсудить детали вашего проекта и получить больше информации о наших услугах. Мы сохраним и улучшим ваш дом, сделав его уютным и безопасным для долгого проживания.
Gerakl24 – ваш партнер по реставрации и ремонту домов в Красноярске и окрестностях.
slot gacor
Hi there! I just would like to offer you a huge thumbs up for your great info you have got here on this post. I will be coming back to your blog for more soon.
largestcatbreed.com
누군가 약간 떨면서 일어섰고, 눈물이 두 줄로 흘러내렸습니다.
Honestly stated! 🌈 Previous remarks are sincere. This post is truly incredible! 🚀
八代將軍戰神版 (V2.2)
素晴らしい記事!共有せずにはいられません。
The b****** app works under a license from the Malta Gaming Authority, which means you can use the app legally and safely. The installed app will take up about 80 MB of internal space, which is affordable for all modern smartphones.The app is well optimized with low system requirements: 6. Enjoy playing Babu88 on PC with MEmu Babu88 is Bangladesh’s leading b****** platform and online c*****, where you’ll find some of the most extensive cricket and other sports b****** opportunities. Place bets on any IPL, World Cup, Big Bash League, CPL, T20, Test Cricket, or ICC matches. Choose the most profitable outcomes and g******* for each successful prediction. Deposit your account any way you like and don’t forget to activate your welcome bonus up to BDT 12,000. A bonus offer at Jaya Baji Bangladesh for users who register and deposit an amount of ৳500, a bonus of ৳1000 for their first bet in the live c***** game category. Users must generate a turnover of 12x within seven days and cannot use this offer in conjunction with other Jaya Baji promotions.
https://johnnycrkm925176.activoblog.com/26724113/parimatch-download-free
Melbet has firmly established itself as a favored c***** b****** site in Bangladesh, providing a diverse and expansive gaming platform. Boasting an impressive collection of over 1000 games, Melbet appeals to a broad audience. It features dynamic and interactive gameplay in the Live C*****, a variety of engaging Slot Games with diverse themes, strategic Table Games, distinctive options like Fishing and Crash Games, and a dedicated Sports B****** section, including cricket—a sport passionately followed in the region. Jaya Baji is one of the best online casinos in Bangladesh that offers top-notch cricket b****** with an official license from the Malta Gaming Authority. It provides various options for live c***** games, table b******, sports b******, fishing games, and many other popular games to enjoy as a beginner or a professional player.
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
This is a topic that is close to my heart… Thank you! Exactly where are your contact details though?
This website really has all of the information and facts I needed about this subject and didn’t know who to ask.
ilogidis.com
오랫동안 생각한 끝에 Hongzhi 황제는 갑자기 깨달았습니다.
ssri withdrawal joint pain https://jointpain.top/# sickle cell dactilitis and joint pain causes
Каннабис в израиле
Каннабис в Израиле: Современные перспективы для здравья и счастья
В последние годы гашиш становился материалом все более распространенного обсуждения в мире медицины и лечебной практики. В разнообразных территориях, в числе Юдейская область, трава становился все более легальным вследствие переменам в законах и развитию медицины. Посмотрим, как закупка и использование каннабиса в Юдейской области может принести пользу здоровью и процветанию.
В Юдейской области каннабис разрешен для медицинского использования с начала 1990-х. Это открыло дорогу большому количеству пациентов получать доступ к полезным свойствам подобного растения. Каннабис обладает множеством активных веществ, называющихся каннабиноидами, включая ТГК и КБД, которые имеют различными медицинскими свойствами.
Один из ключевых достоинств травы является его возможность снимать боль и избавлять от воспаления. Многочисленные научные исследования показывают, что марихуана может быть эффективным средством для борьбы с хронической болью, такие как артрит, метеозависимость и невралгия. В дополнение, гашиш может содействовать сократить проявления различных заболеваний, в том числе паркинсонизм, болезнь Альцгеймера и меланхолию.
Еще одним важным параметром гашиша представляет собой его способность снижать тревожность и улучшать настроение. Многие люди тревожатся от расстройств тревожности и пессимизма, и марихуана может быть полезным средством управления данными психическими состояниями. каннабидиол, один из ключевых компонентов каннабиса, завсегдатай своими анксиолитическими свойствами, которые способны помочь снизить степень тревожности и стеснения.
Более того, каннабис может быть благотворным для повышения аппетита и времени сна. Для людей переживающих проблем с аппетитом или бессонницы, потребление марихуаны может быть способом восстановить нормальные телесные функции.
Следует отметить, что использование каннабиса должно быть осознанным и поддающимся контролю. Хотя гашиш обладает множеством полезных аспектов, он также может провоцировать негативные последствия, такие как сонливость, психоактивные реакции и снижение когнитивных способностей. По этой причине, важно использовать каннабис под наблюдением квалифицированных специалистов и по рекомендации врача.
По итогу, возможность использования гашиша в Юдейской области является новым шансом для усиления здоровья и удачи. Благодаря своим лечебным качествам, трава может оказаться эффективным средством для лечения разных болезней и повышения качества жизни нескольких индивидуумов.
북 오브 데드
“무슨 일이야, 형님?” Zhang Yanling은 매우 어지러움을 느꼈습니다.
Website ini mengintegrasikan video dan infografis dengan sangat baik membantu menjelaskan informasi kompleks dengan cara yang mudah dipahami
Euro 2024
Euro 2024 – Sân chơi bóng đá đỉnh cao Châu Âu
Euro 2024 (hay Giải vô địch bóng đá Châu Âu 2024) là một sự kiện thể thao lớn tại châu Âu, thu hút sự chú ý của hàng triệu người hâm mộ trên khắp thế giới. Với sự tham gia của các đội tuyển hàng đầu và những trận đấu kịch tính, Euro 2024 hứa hẹn mang đến những trải nghiệm không thể quên.
Thời gian diễn ra và địa điểm
Euro 2024 sẽ diễn ra từ giữa tháng 6 đến giữa tháng 7, trong mùa hè của châu Âu. Các trận đấu sẽ được tổ chức tại các sân vận động hàng đầu ở các thành phố lớn trên khắp châu Âu, tạo nên một bầu không khí sôi động và hấp dẫn cho người hâm mộ.
Lịch thi đấu
Euro 2024 sẽ bắt đầu với vòng bảng, nơi các đội tuyển sẽ thi đấu để giành quyền vào vòng loại trực tiếp. Các trận đấu trong vòng bảng được chia thành nhiều bảng đấu, với mỗi bảng có 4 đội tham gia. Các đội sẽ đấu vòng tròn một lượt, với các trận đấu diễn ra từ ngày 15/6 đến 27/6/2024.
Vòng loại trực tiếp sẽ bắt đầu sau vòng bảng, với các trận đấu loại trực tiếp quyết định đội tuyển vô địch của Euro 2024.
Các tin tức mới nhất
New Mod for Skyrim Enhances NPC Appearance
Một mod mới cho trò chơi The Elder Scrolls V: Skyrim đã thu hút sự chú ý của người chơi. Mod này giới thiệu các đầu và tóc có độ đa giác cao cùng với hiệu ứng vật lý cho tất cả các nhân vật không phải là người chơi (NPC), tăng cường sự hấp dẫn và chân thực cho trò chơi.
Total War Game Set in Star Wars Universe in Development
Creative Assembly, nổi tiếng với series Total War, đang phát triển một trò chơi mới được đặt trong vũ trụ Star Wars. Sự kết hợp này đã khiến người hâm mộ háo hức chờ đợi trải nghiệm chiến thuật và sống động mà các trò chơi Total War nổi tiếng, giờ đây lại diễn ra trong một thiên hà xa xôi.
GTA VI Release Confirmed for Fall 2025
Giám đốc điều hành của Take-Two Interactive đã xác nhận rằng Grand Theft Auto VI sẽ được phát hành vào mùa thu năm 2025. Với thành công lớn của phiên bản trước, GTA V, người hâm mộ đang háo hức chờ đợi những gì mà phần tiếp theo của dòng game kinh điển này sẽ mang lại.
Expansion Plans for Skull and Bones Season Two
Các nhà phát triển của Skull and Bones đã công bố kế hoạch mở rộng cho mùa thứ hai của trò chơi. Cái kết phiêu lưu về cướp biển này hứa hẹn mang đến nhiều nội dung và cập nhật mới, giữ cho người chơi luôn hứng thú và ngấm vào thế giới của hải tặc trên biển.
Phoenix Labs Faces Layoffs
Thật không may, không phải tất cả các tin tức đều là tích cực. Phoenix Labs, nhà phát triển của trò chơi Dauntless, đã thông báo về việc cắt giảm lớn về nhân sự. Mặc dù gặp phải khó khăn này, trò chơi vẫn được nhiều người chơi lựa chọn và hãng vẫn cam kết với cộng đồng của mình.
Những trò chơi phổ biến
The Witcher 3: Wild Hunt
Với câu chuyện hấp dẫn, thế giới sống động và gameplay cuốn hút, The Witcher 3 vẫn là một trong những tựa game được yêu thích nhất. Câu chuyện phong phú và thế giới mở rộng đã thu hút người chơi.
Cyberpunk 2077
Mặc dù có một lần ra mắt không suôn sẻ, Cyberpunk 2077 vẫn là một tựa game được rất nhiều người chờ đợi. Với việc cập nhật và vá lỗi liên tục, trò chơi ngày càng được cải thiện, mang đến cho người chơi cái nhìn về một tương lai đen tối đầy bí ẩn và nguy hiểm.
Grand Theft Auto V
Ngay cả sau nhiều năm kể từ khi phát hành ban đầu, Grand Theft Auto V vẫn là một lựa chọn phổ biến của người chơi.
supermoney88
supermoney88
크립토 골드
돈이 있는 사람은 필연적으로 고귀한 감정을 갖게 되는 것 같습니다.
बेटवीसा ऑनलाइन कैसीनो पर ब्लैकजैक और रूलेट का आनंद
ऑनलाइन कैसीनो में ब्लैकजैक और रूलेट दो बहुत ही लोकप्रिय और मजेदार खेल हैं। बेटवीसा ऑनलाइन कैसीनो इन दोनों खेलों के विभिन्न वेरिएंट्स को पेश करता है, जो खिलाड़ियों को अनूठा और रोमांचक अनुभव प्रदान करते हैं।
ब्लैकजैक:
ब्लैकजैक एक क्लासिक कार्ड गेम है जो रणनीति और कौशल की मांग करता है। यह गेम सरल है, लेकिन इसमें महारत हासिल करने के लिए अभ्यास की आवश्यकता होती है। बेटवीसा ऑनलाइन कैसीनो क्लासिक ब्लैकजैक, मल्टीहैंड ब्लैकजैक, और लाइव डीलर ब्लैकजैक जैसे विविध वेरिएंट्स प्रदान करता है।
क्लासिक ब्लैकजैक में लक्ष्य डीलर को 21 के करीब पहुंचकर हराना होता है। मल्टीहैंड ब्लैकजैक में आप एक साथ कई हाथ खेल सकते हैं, जो आपके जीतने के अवसरों को बढ़ाता है। जबकि लाइव डीलर ब्लैकजैक खिलाड़ियों को असली कैसीनो जैसा अनुभव प्रदान करता है।
रूलेट:
रूले एक और लोकप्रिय कैसीनो गेम है जिसे खेलने में बहुत मजा आता है। यह खेल भाग्य और रोमांच का सही मिश्रण है। बेटवीसा ऑनलाइन कैसीनो पर उपलब्ध विभिन्न रूले वेरिएंट्स में यूरोपियन रूले, अमेरिकन रूले, और फ्रेंच रूले शामिल हैं।
यूरोपियन रूले सबसे लोकप्रिय वर्जन है, जबकि अमेरिकन रूले में एक अतिरिक्त डबल शून्य (00) होता है, जिससे खेल थोड़ा चुनौतीपूर्ण हो जाता है। फ्रेंच रूले यूरोपियन रूले के समान है, लेकिन इसमें कुछ अतिरिक्त नियम और बेटिंग ऑप्शंस होते हैं।
बेटवीसा लॉगिन करके या बेटवीसा ऐप डाउनलोड करके आप इन रोमांचक और चुनौतीपूर्ण कैसीनो गेम्स का आनंद ले सकते हैं। चाहे आप ब्लैकजैक की रणनीति को समझना चाहते हों या रूलेट के भाग्य का परीक्षण करना चाहते हों, बेटवीसा ऑनलाइन कैसीनो आपके लिए सबकुछ प्रदान करता है।
इन गेम्स को खेलकर आप अपने ऑनलाइन कैसीनो अनुभव को और भी रोमांचक बना सकते हैं। इसलिए, बेटवीसा इंडिया में जाकर इन गेम्स का आनंद लेना न भूलें!
Betvisa Bet
Betvisa Bet | Catch the BPL Excitement with Betvisa!
Hunt for ₹10million! | Enter the BPL at Betvisa and chase a staggering Bounty.
Valentine’s Boost at Visa Bet! | Feel the rush of a 143% Love Mania Bonus .
predict BPL T20 outcomes | score big rewards through Betvisa login!
#betvisa
Betvisa bonus Win! | Leverage your 10 free spins to possibly win $8,888.
Share and Earn! | win ₹500 via the Betvisa app download!
https://www.betvisa-bet.com/hi
#visabet #betvisalogin #betvisaapp #betvisaIndia
Sign-Up Jackpot! | Register at Betvisa India and win ₹8,888.
Double your play! | with a ₹1,000 deposit and get ₹2,000 free at Betvisa online!
Download the Betvisa download today and don’t miss out on the action!
video games guide
Thrilling Developments and Iconic Games in the Domain of Videogames
In the fluid environment of videogames, there’s constantly something innovative and thrilling on the forefront. From enhancements optimizing iconic mainstays to forthcoming debuts in renowned brands, the gaming landscape is flourishing as ever.
We’ll take a snapshot into the up-to-date announcements and specific the iconic games engrossing fans worldwide.
Latest News
1. Innovative Modification for The Elder Scrolls V: Skyrim Improves NPC Aesthetics
A freshly-launched enhancement for Skyrim has grabbed the notice of gamers. This mod adds high-polygon heads and realistic hair for all (NPCs), elevating the world’s visuals and engagement.
2. Total War Games Title Placed in Star Wars Universe Under Development
Creative Assembly, famous for their Total War Games lineup, is supposedly crafting a upcoming experience located in the Star Wars Setting realm. This exciting collaboration has players looking forward to the profound and captivating journey that Total War Games releases are acclaimed for, at last located in a world distant.
3. Grand Theft Auto VI Release Announced for Autumn 2025
Take-Two Interactive’s CEO’s Head has announced that GTA VI is scheduled to launch in Q4 2025. With the colossal popularity of its prior release, GTA V, players are awaiting to see what the upcoming installment of this iconic franchise will provide.
4. Growth Developments for Skull & Bones Second Season
Creators of Skull and Bones have revealed broader initiatives for the experience’s sophomore season. This nautical journey offers new experiences and improvements, maintaining enthusiasts invested and immersed in the realm of oceanic nautical adventures.
5. Phoenix Labs Studio Experiences Staff Cuts
Sadly, not all news is positive. Phoenix Labs, the developer in charge of Dauntless Experience, has disclosed significant staff cuts. In spite of this difficulty, the experience remains to be a popular selection across players, and the developer continues to be focused on its audience.
Beloved Games
1. The Witcher 3
With its captivating plot, captivating realm, and enthralling adventure, Wild Hunt keeps a cherished game within enthusiasts. Its expansive narrative and expansive nonlinear world keep to engage players in.
2. Cyberpunk Game
Regardless of a rocky arrival, Cyberpunk Game continues to be a eagerly awaited title. With continuous patches and fixes, the game continues to improve, providing players a glimpse into a futuristic world abundant with peril.
3. Grand Theft Auto V
Despite time following its debut debut, GTA V remains a renowned selection across players. Its expansive open world, compelling story, and co-op components keep enthusiasts coming back for more journeys.
4. Portal
A legendary analytical release, Portal Game is celebrated for its innovative gameplay mechanics and brilliant spatial design. Its complex challenges and witty writing have established it as a noteworthy release in the gaming industry.
5. Far Cry
Far Cry 3 Game is celebrated as a standout entries in the franchise, presenting fans an free-roaming exploration rife with excitement. Its compelling plot and iconic entities have solidified its status as a beloved release.
6. Dishonored Series
Dishonored Game is celebrated for its stealthy features and unique setting. Fans take on the persona of a mystical killer, exploring a city teeming with governmental intrigue.
7. Assassin’s Creed 2
As part of the iconic Assassin’s Creed Series series, Assassin’s Creed 2 is cherished for its immersive narrative, captivating features, and historical realms. It continues to be a remarkable experience in the collection and a beloved across fans.
In conclusion, the realm of videogames is thriving and constantly evolving, with groundbreaking advan
JiliAce ক্যাসিনোতে অনলাইন মোরগ লড়াই এবং রেসিং গেম: একটি নতুন অভিজ্ঞতা
অনলাইন গেমিংয়ের বিশ্বে JiliAce ক্যাসিনো একটি বিশেষ স্থান অধিকার করে নিয়েছে, যেখানে ব্যবহারকারীরা বিভিন্ন ধরনের গেম উপভোগ করতে পারেন। আজ আমরা JiliAce〡JitaBet প্ল্যাটফর্মে পাওয়া দুটি জনপ্রিয় গেম সম্পর্কে জানবো: অনলাইন মোরগ লড়াই এবং রেসিং গেম।
অনলাইন মোরগ লড়াই: ঐতিহ্যবাহী গেমের ডিজিটাল রূপ
মোরগ লড়াই হল একটি অনলাইন গেম যা পন্টারদের বিভিন্ন প্রতিযোগী ডিজিটাল মোরগগুলিতে বাজি রাখার ক্ষমতা দেয়। ঐতিহ্যগতভাবে, মোরগ লড়াই একটি জনপ্রিয় খেলা ছিল, যেখানে মোরগদের মধ্যে প্রতিযোগিতা হতো। এখন এই গেমটি অনলাইনে খেলা যায়, যেখানে আপনি আপনার পছন্দের মোরগের উপর বাজি রাখতে পারেন এবং উত্তেজনাপূর্ণ প্রতিযোগিতার অভিজ্ঞতা উপভোগ করতে পারেন। Jili ace c*****-তে এই গেমটি খেলে আপনি ঐতিহ্যবাহী মোরগ লড়াইয়ের মজার অভিজ্ঞতা পাবেন, যা ডিজিটাল প্ল্যাটফর্মে খেলার সুবিধা নিয়ে আসে।
অনলাইন রেসিং: স্পিড এবং উত্তেজনার মিশ্রণ
“অনলাইনে রেসিং” রেসিং সম্পর্কিত বিভিন্ন অনলাইন ক্রিয়াকলাপকে উল্লেখ করতে পারে এবং প্রসঙ্গটি নির্ভর করে নির্দিষ্ট ধরণের রেসিংয়ের উপর। JiliAce ক্যাসিনোতে, আপনি বিভিন্ন ধরনের রেসিং গেম খুঁজে পাবেন, যেখানে আপনি গাড়ি, বাইক এবং অন্যান্য যানবাহনের প্রতিযোগিতায় অংশ নিতে পারবেন। রেসিং গেমগুলি তাদের বাস্তবসম্মত গ্রাফিক্স এবং উত্তেজনাপূর্ণ গেমপ্লের জন্য পরিচিত, যা আপনাকে একটি শ্বাসরুদ্ধকর অভিজ্ঞতা প্রদান করবে। Jili ace c*****-তে রেসিং গেম খেলে আপনি স্পিড এবং উত্তেজনার মিশ্রণ উপভোগ করতে পারবেন।
সহজ লগইন এবং সুবিধাজনক গেমিং
Jili ace login প্রক্রিয়া অত্যন্ত সহজ এবং ব্যবহারকারীদের জন্য সুবিধাজনক। একবার লগইন করলে, আপনি সহজেই বিভিন্ন গেমের অ্যাক্সেস পাবেন এবং আপনার পছন্দসই গেম খেলার জন্য প্রস্তুত হয়ে যাবেন। Jiliace login করার পর, আপনি আপনার গেমিং যাত্রা শুরু করতে পারবেন এবং বিভিন্ন ধরনের বোনাস ও পুরস্কার উপভোগ করতে পারবেন।
Jita Bet: বড় পুরস্কারের সুযোগ
JiliAce ক্যাসিনোতে Jita Bet-এর সাথে আপনার গেমিং অভিজ্ঞতা আরও সমৃদ্ধ করুন। এখানে আপনি বিভিন্ন ধরণের বাজি ধরতে পারেন এবং বড় পুরস্কার জিততে পারেন। Jita Bet প্ল্যাটফর্মটি ব্যবহারকারীদের জন্য সহজ এবং সুরক্ষিত বাজি ধরার সুযোগ প্রদান করে।
যোগদান করুন এবং উপভোগ করুন
JiliAce〡JitaBet-এর অংশ হয়ে আজই আপনার গেমিং যাত্রা শুরু করুন। Jili ace c***** এবং Jita Bet-এ লগইন করে অনলাইন মোরগ লড়াই এবং রেসিং গেমের মত আকর্ষণীয় গেম উপভোগ করুন। এখনই যোগ দিন এবং অনলাইন গেমিংয়ের এক নতুন জগতে প্রবেশ করুন!
Jiliacet c*****
Jiliacet c***** |
Warm welcome! | Get a 200% Welcome Bonus when you log in jiliace c*****.
IPL Tournament! | Join the IPL fever with Jita Bet. Win big prizes!
Epic JILI Tournaments! | Go head-to-head in the Jita bet Super Tournament
#jiliacecasino
Cashback on Deposits! | Get cash back on every deposit. At Jili ace c*****
Uninterrupted bonuses at JITAACE! | Stay logged in Jiliace login!
https://www.jiliace-c*****.online/bn
#Jiliacecasino # Jiliacelogin#Jiliacelogin # Jitabet
Slot Feast! | Spin to win 100% up to 20,000 ৳. at Jili ace login!
Big Fishing Bonus! | Get a 100% bonus up to ৳20,000 in the Fishing Game.
JiliAce C*****’s top choice for great bonuses. login, play, and win big today!
에그슬롯
Fang Xiaofan은 단호하게 말했습니다. “당신은 거짓말을 했어요. 나는 그것을 먹지 않았습니다!”
The Ultimate Guide to Finding the Best Online Casinos for Real Money in the Philippines
The thrilling world of online g******* has transformed the landscape of the c***** industry, bringing the excitement of the c***** floor right to the comfort of your own home. For players in the Philippines seeking the best online c***** experience, the process of finding a reliable and trustworthy platform can seem daunting. Fear not, as we have curated this ultimate guide to help you navigate the dynamic world of online casinos and make informed choices that cater to your preferences and maximize your gaming experience.
Prioritizing Reputation and Licensing
When it comes to online g*******, reputation and licensing are the cornerstones of a reliable and secure platform. Betvisa C***** has established itself as a leader in the industry, boasting a solid reputation for fair play, responsible gaming practices, and robust regulatory oversight. By choosing platforms like Betvisa C*****, you can rest assured that your personal and financial information is protected, allowing you to focus on the thrill of the game.
Exploring the Betvisa PH Advantage
As a player in the Philippines, you deserve an online c***** experience that is tailored to your local needs and preferences. Betvisa PH offers a specialized platform that caters to the Philippine market, providing a seamless Betvisa Login process, a curated game selection, and promotions that resonate with your gaming preferences. This localized approach ensures that you can immerse yourself in an online c***** experience that truly resonates with you.
Embracing the Diversity of Games
The best online casinos, such as Betvisa C*****, offer a vast and diverse selection of games to cater to a wide range of player preferences. From classic table games like Visa Bet to the latest slot titles, the platform’s game library is constantly evolving to provide you with a thrilling and engaging experience. Explore the offerings, take advantage of demo versions, and find the games that ignite your passion for online g*******.
Unlocking Bonuses and Promotions
Online casinos are known for their generous bonuses and promotions, and Betvisa C***** is no exception. From welcome packages to free spins and reload offers, these incentives can provide you with valuable extra funds to explore the platform’s offerings. However, it’s crucial to carefully read the t******************* to ensure that you maximize the potential benefits and avoid any unintended consequences.
Ensuring Secure and Seamless Transactions
In the world of online g*******, the security and reliability of financial transactions are paramount. Betvisa C*****’s commitment to player protection is evident in its adoption of state-of-the-art security measures and its support for a wide range of payment methods, including Visa Bet. This ensures that your gaming experience is not only thrilling but also secure, instilling confidence in your online c***** endeavors.
Accessing Responsive Customer Support
When navigating the complexities of online g*******, having access to reliable and responsive customer support can make a significant difference. Betvisa C*****’s dedicated team is committed to addressing player inquiries and resolving any issues that may arise, ensuring a seamless and stress-free experience.
By following the guidance outlined in this ultimate guide, you can confidently explore the world of online casinos and find the best platform that caters to your gaming preferences and maximizes your chances of success. Betvisa C*****, with its unwavering commitment to player satisfaction, diverse game offerings, and secure platform, stands out as a premier destination for players in the Philippines seeking the ultimate online g******* experience.
Betvisa Bet | Step into the Arena with Betvisa!
Spin to Win Daily at Betvisa PH! | Take a whirl and bag ?8,888 in big rewards.
Valentine’s 143% Love Boost at Visa Bet! | Celebrate r****** and rewards !
Deposit Bonus Magic! | Deposit 50 and get an 88 bonus instantly at Betvisa C*****.
#betvisa
Free Cash & More Spins! | Sign up betvisa login,grab 500 free cash plus 5 free spins.
Sign-Up Fortune | Join through betvisa app for a free ?500 and fabulous ?8,888.
https://www.betvisa-bet.com/tl
#visabet #betvisalogin #betvisacasino # betvisaph
Double Your Play at betvisa com! | Deposit 1,000 and get a whopping 2,000 free
100% Cock Fight Welcome at Visa Bet! | Plunge into the exciting world .Bet and win!
Jump into Betvisa for exciting games, stunning bonuses, and endless winnings!
supermoney88
SUPERMONEY88: Situs Game Online Deposit Pulsa Terbaik di Indonesia
SUPERMONEY88 adalah situs game online deposit pulsa terbaik tahun 2020 di Indonesia. Kami menyediakan berbagai macam game online terbaik dan terlengkap yang bisa Anda mainkan di situs game online kami. Hanya dengan mendaftar satu ID, Anda bisa memainkan seluruh permainan yang tersedia di SUPERMONEY88.
Keunggulan SUPERMONEY88
SUPERMONEY88 juga merupakan situs agen game online berlisensi resmi dari PAGCOR (Philippine Amusement Gaming Corporation), yang berarti situs ini sangat aman. Kami didukung dengan server hosting yang cepat dan sistem keamanan dengan metode enkripsi termutakhir di dunia untuk menjaga keamanan database Anda. Selain itu, tampilan situs kami yang sangat modern membuat Anda nyaman mengakses situs kami.
Layanan Praktis dan Terpercaya
Selain menjadi game online terbaik, ada alasan mengapa situs SUPERMONEY88 ini sangat spesial. Kami memberikan layanan praktis untuk melakukan deposit yaitu dengan melakukan deposit pulsa XL ataupun Telkomsel dengan potongan terendah dari situs game online lainnya. Ini membuat situs kami menjadi salah satu situs game online pulsa terbesar di Indonesia. Anda bisa melakukan deposit pulsa menggunakan E-commerce resmi seperti OVO, Gopay, Dana, atau melalui minimarket seperti Indomaret dan Alfamart.
Kami juga terkenal sebagai agen game online terpercaya. Kepercayaan Anda adalah prioritas kami, dan itulah yang membuat kami menjadi agen game online terbaik sepanjang masa.
Kemudahan Bermain Game Online
Permainan game online di SUPERMONEY88 memudahkan Anda untuk memainkannya dari mana saja dan kapan saja. Anda tidak perlu repot bepergian lagi, karena SUPERMONEY88 menyediakan beragam jenis game online. Kami juga memiliki jenis game online yang dipandu oleh host cantik, sehingga Anda tidak akan merasa bosan.
크립토 골드
Hongzhi 황제는 눈에 눈물을 흘리며 여기 핀과 바늘에 앉아있는 것처럼 느꼈습니다.
Wonderful job on this post! I learned a lot.
बेटवीसा ऑनलाइन कैसीनो में रोमांचक और मजेदार गेम्स का आनंद
ऑनलाइन कैसीनो का आनंद लेते हुए रोमांचक और मजेदार गेम्स खेलना एक बेहतरीन अनुभव होता है। बेटवीसा ऑनलाइन कैसीनो एक प्रमुख प्लेटफॉर्म है जो खिलाड़ियों को विविध और रोमांचक गेम्स का अनुभव प्रदान करता है।
अगर आप बेटवीसा लॉगिन करके या बेटवीसा ऐप का उपयोग करके बेटवीसा ऑनलाइन कैसीनो में शामिल होते हैं, तो आपको कुछ वास्तव में मजेदार और लोकप्रिय खेलों का आनंद लेने को मिलेगा।
पहला है – सलाह वाला या “रूलेट”। यह एक पारंपरिक कैसीनो गेम है लेकिन बेटवीसा ने इसे आधुनिक और रोमांचक बना दिया है। खिलाड़ी अपने भाग्य का परीक्षण कर सकते हैं और बड़े पैसों की जीत का सपना देख सकते हैं।
बेटवीसा इंडिया में बहुत लोकप्रिय है “ब्लैकजैक” भी। यह गेम कार्ड गेमिंग का क्लासिक अनुभव प्रदान करता है और कुशल खिलाड़ियों को अच्छा रिटर्न देता है।
इसके अलावा, बेटवीसा ऑनलाइन कैसीनो में “स्लॉट मशीन” भी उपलब्ध हैं। ये ड्रैमेटिक थीम्स और जबरदस्त जैकपॉट के साथ आकर्षक और रोमांचक हो सकते हैं।
कुछ अन्य लोकप्रिय गेम्स में “बैकरेट”, “पोकर”, और “लाइव डीलर कैसीनो” शामिल हैं। ये सभी भव्य ग्राफिक्स, सरल नियम और उत्साहजनक विजय संभावनाएं प्रदान करते हैं।
समग्र रूप से, बेटवीसा ऑनलाइन कैसीनो में उपलब्ध गेम्स अनूठे, रोमांचक और मनोरंजक हैं। चाहे आप क्लासिक कैसीनो गेम्स का आनंद लेना चाहते हों या नए और नवीनतम गेम्स की तलाश में हों, बेटवीसा आपके लिए सबकुछ प्रदान करता है।
बेटवीसा लॉगिन करके या बेटवीसा ऐप डाउनलोड करके आप इन मजेदार गेम्स का आनंद ले सकते हैं और अपने ऑनलाइन कैसीनो अनुभव को और भी रोचक बना सकते हैं। हमारा सुझाव है कि आप इन गेम्स को आजमाकर देखें और देखें कि आप कितना उत्साहित और उत्साहित होते हैं!
Betvisa Bet
Betvisa Bet | Catch the BPL Excitement with Betvisa!
Hunt for ₹10million! | Enter the BPL at Betvisa and chase a staggering Bounty.
Valentine’s Boost at Visa Bet! | Feel the rush of a 143% Love Mania Bonus .
predict BPL T20 outcomes | score big rewards through Betvisa login!
#betvisa
Betvisa bonus Win! | Leverage your 10 free spins to possibly win $8,888.
Share and Earn! | win ₹500 via the Betvisa app download!
https://www.betvisa-bet.com/hi
#visabet #betvisalogin #betvisaapp #betvisaIndia
Sign-Up Jackpot! | Register at Betvisa India and win ₹8,888.
Double your play! | with a ₹1,000 deposit and get ₹2,000 free at Betvisa online!
Download the Betvisa download today and don’t miss out on the action!
럭키 네코
“아니, 아니, 아니.” Zhang Heling은 그의 마음에 희미한 희망을 느꼈습니다.
I’m in awe of your skills, this is amazing!
Контроль аккаунта токенов
Контроль USDT TRC20 и прочих блокчейн переводов
На данном ресурсе вы развернутые обзоры различных инструментов для верификации операций и кошельков, содержащие anti-money laundering анализы для USDT и различных блокчейн-активов. Вот основные функции, которые в наших описаниях:
Проверка USDT на платформе TRC20
Многие ресурсы предлагают полную верификацию операций монет на блокчейне TRC20. Это позволяет фиксировать подозрительную деятельность и удовлетворять законодательным положениям.
Проверка транзакций токенов
В наших обзорах указаны инструменты для детального проверки и наблюдения переводов USDT, которые гарантирует сохранять чистоту и надежность операций.
антиотмывочная верификация монет
Известные ресурсы поддерживают anti-money laundering проверку монет, гарантируя идентифицировать и исключать эпизоды незаконных операций и финансовых нарушений.
Верификация адреса монет
Наши ревью охватывают сервисы, которые позволяют верифицировать кошельки USDT на предмет санкций и необычных платежей, гарантируя повышенный степень безопасности защищенности.
Анализ операций криптовалюты на платформе TRC20
Вы сможете найти найдете ресурсы, поддерживающие проверку платежей монет на блокчейне TRC20 сети, что соответствие соответствие всем необходимым необходимым нормам.
Анализ аккаунта аккаунта монет
В ревью описаны сервисы для контроля аккаунтов аккаунтов токенов на потенциальных угроз рисков.
Верификация кошелька монет на блокчейне TRC20
Наши ревью представляют сервисы, предлагающие проверку адресов USDT на блокчейне TRC20 блокчейна, что помогает предотвращает предотвратить мошенничество и финансовых нарушений.
Верификация USDT на прозрачность
Описанные платформы предусматривают контролировать транзакции и кошельки на чистоту, выявляя необычную активность.
антиотмывочного закона анализ USDT на платформе TRC20
В оценках представлены платформы, предлагающие anti-money laundering верификацию для токенов в сети TRC20 блокчейна, что позволяет вашему компании выполнять международным положениям.
Верификация токенов на сети ERC20
Наши ревью содержат платформы, предоставляющие анализ монет на блокчейне ERC20 сети, что гарантирует позволяет комплексный анализ транзакций и кошельков.
Анализ виртуального кошелька
Мы описываем сервисы, обеспечивающие опции по верификации криптовалютных кошельков, содержащие контроль операций и выявление необычной активности.
Проверка кошелька криптовалютного кошелька
Наши описания представляют сервисы, предназначенные для проверять счета криптовалютных кошельков для гарантирования дополнительного уровня надежности.
Верификация виртуального кошелька на транзакции
В наших описаниях описаны сервисы для верификации криптокошельков на транзакции, что обеспечивает поддерживать гарантировать чистоту операций.
Контроль цифрового кошелька на отсутствие подозрительных действий
Наши описания включают решения, позволяющие контролировать криптовалютные кошельки на отсутствие подозрительных действий, определяя подозрительные подозреваемые действия.
Читая представленные оценки, вы сможете подберете лучшие платформы для верификации и отслеживания цифровых транзакций, чтобы обеспечивать обеспечивать повышенный степень защищенности и удовлетворять все правовым положениям.
에그슬롯
그녀는 실제로 소녀이고 Tiger의 책을 읽는 소녀가 있다고 생각하지 않았습니다.그는 실제로 이때 침수 지역의 모든 사람들을 재배치하기로 결정했습니다.
online c***** real money
Virtual G******* Platform Real Money: Upsides for Participants
Introduction
Virtual g******* platforms delivering for-profit activities have gained considerable widespread appeal, delivering customers with the chance to earn financial payouts while relishing their cherished gaming offerings from home. This piece examines the benefits of online c***** for-profit offerings, accentuating their favorable effect on the leisure sector.
Ease of Access and Reachability
Internet-based g******* platform for-profit experiences provide convenience by permitting users to reach a extensive variety of experiences from anywhere with an network access. This eradicates the obligation to travel to a brick-and-mortar g******* establishment, preserving expenses. Online casinos are also present at all times, giving users to partake in at their ease.
Diversity of Options
Internet-based g******* platforms present a wider diversity of games than physical casinos, involving slot-based activities, pontoon, spinning wheel, and card games. This breadth enables customers to experiment with different activities and identify novel favorites, improving their holistic entertainment experience.
Rewards and Discounts
Digital gaming sites present generous incentives and discounts to draw in and hold onto players. These bonuses can incorporate introductory rewards, non-chargeable turns, and cashback promotions, delivering supplemental significance for participants. Reward initiatives likewise compensate customers for their persistent support.
Capability Building
Partaking in for-profit activities on the internet can facilitate users acquire aptitudes such as problem-solving. Games like pontoon and c*****-style games call for customers to make determinations that can shape the outcome of the experience, helping them develop decision-making faculties.
Communal Engagement
ChatGPT l Валли, [06.06.2024 4:08]
Internet-based g******* platforms deliver prospects for communal connection through discussion forums, online communities, and live dealer offerings. Players can communicate with each other, communicate advice and tactics, and sometimes create social relationships.
Financial Advantages
The digital gaming industry generates employment and provides for the economy through budgetary incomes and authorization charges. This fiscal effect upsides a comprehensive variety of professions, from experience developers to user assistance representatives.
Key Takeaways
Internet-based g******* platform real money offerings present many upsides for customers, encompassing ease, breadth, rewards, competency enhancement, communal engagement, and monetary benefits. As the sector persistently progress, the broad acceptance of online casinos is projected to expand.
No-Cost Slot-Based Offerings: A Enjoyable and Beneficial Experience
No-Cost virtual wagering experiences have transformed into steadily well-liked among users aiming for a exciting and safe interactive sensation. These offerings present a comprehensive selection of advantages, making them a chosen choice for many. Let’s explore in what way complimentary slot-based experiences can reward players and the motivations behind they are so widely experienced.
Entertainment Value
One of the main factors users savor partaking in complimentary slot-based experiences is for the fun element they provide. These activities are developed to be engaging and enthralling, with lively illustrations and absorbing music that enhance the holistic leisure encounter. Whether you’re a leisure-oriented user wanting to pass the time or a dedicated leisure activity enthusiast aiming for thrills, free poker machine games offer amusement for everyone.
Capability Building
Engaging with complimentary slot-based offerings can likewise assist develop beneficial abilities such as critical analysis. These games necessitate participants to arrive at immediate decisions based on the virtual assets they are acquired, helping them sharpen their critical-thinking skills and cerebral acuity. Additionally, players can investigate various methods, honing their faculties devoid of the possibility of financial impact of parting with actual currency.
Convenience and Accessibility
A supplemental benefit of gratis electronic gaming activities is their simplicity and accessibility. These games can be partaken in in the virtual sphere from the comfort of your own residence, removing the necessity to commute to a physical c*****. They are also offered around the clock, allowing customers to savor them at whatever moment that fits them. This convenience establishes gratis electronic gaming activities a well-liked option for players with demanding routines or those looking for a quick entertainment remedy.
Communal Engagement
Many free poker machine experiences in addition grant group-based aspects that allow participants to communicate with their peers. This can feature messaging platforms, interactive platforms, and competitive configurations where participants can pit themselves against one another. These shared experiences inject an supplemental facet of enjoyment to the entertainment encounter, enabling customers to communicate with others who have in common their preferences.
Worry Mitigation and Emotional Refreshment
Interacting with free poker machine activities can as well be a superb way to destress and unwind after a prolonged period. The effortless engagement and peaceful soundtracks can assist diminish tension and nervousness, providing a refreshing escape from the challenges of normal experience. Additionally, the suspense of winning simulated credits can enhance your frame of mind and leave you feeling revitalized.
Conclusion
Complimentary slot-based games offer a comprehensive selection of upsides for participants, including entertainment, competency enhancement, ease, social interaction, and tension alleviation and decompression. Regardless of whether you’re looking to improve your leisure abilities or simply enjoy yourself, no-cost virtual wagering games deliver a profitable and pleasurable encounter for participants of every types.
Website ini adalah salah satu yang terbaik yang pernah saya kunjungi. Desainnya modern, navigasinya sangat mudah digunakan, dan kontennya sangat berkualitas dan up-to-date. Saya selalu menemukan informasi yang saya cari dengan cepat dan akurat. Terima kasih telah menyediakan sumber yang begitu hebat dan bermanfaat.
https://xn--lg3bul62mlrndkfq2f.com/ed98b8ecb998ebafbc-ec9785ecb2b4/ed98b8ecb998ebafbc-ebb688eab1b4eba788/
mantul88
리액툰즈
이것은 의심 할 여지없이 그에게 폭발적인 소식입니다.
Examining Promotion Gaming Hubs: An Exciting and Accessible B****** Choice
Prelude
Contest casinos are growing into a popular substitute for players looking for an exciting and legal way to relish internet-based gaming. Unlike classic digital g******* platforms, lottery g******* platforms function under separate legitimate structures, facilitating them to offer events and awards without being subject to the same rules. This piece analyzes the concept of promotion gaming hubs, their benefits, and why they are attracting a increasing figure of players.
Sweepstakes Casinos Explained
A sweepstakes gaming hub works by supplying participants with online coins, which can be used to engage in games. Gamers can earn more online currency or actual gifts, like money. The main difference from traditional gaming hubs is that participants do not buy funds immediately but obtain it through advertising campaigns, such as acquiring a goods or joining in a gratis participation lottery. This model facilitates contest casinos to work legally in many jurisdictions where classic virtual gaming is restricted.
Imagine that every week you bet a $20, 10-team NFL parlay with a potential payout of $10,000. You’ve never actually hit one, but for you, it’s akin to playing the lottery: investing a little and dreaming big. As you’re about to walk into the sportsbook, you find $5,000 lying on the ground, and you have no way of finding its owner to return it. After you pick up the cash and do a happy dance in your mind, do you rush to the window and bet it all on one game? Let’s assume that you’ve placed the above wager with a $100 bet. Should all three teams win, you stand to profit $370 from your bet. In our example, all three matches kicked off at the same time, and for your parlay bet to win, each of your selections needs to win their respective matches.
https://worlds-directory.com/listings12756415/more-hints
You can bet on a wide range of sports on Michigan sportsbooks. While the standard markets for baseball, basketball, football, and hockey are all present in every sportsbook, you can find more niche markets like cycling, darts, and snooker as well. For a full list of the sports available at Michigan sportsbooks, check the section of this page titled ‘B****** Markets Available on Michigan Sportsbooks’. ESPN BET is one of the newest b****** sites in the U.S., having just launched in late 2023. It’s rare that we see a brand-new online b****** site launch to such success these days, and a lot of that is due to its promos. BetMGM Sportsbook sets the industry standard in many regards, one of them being in the area of sports b****** apps. The modern interface mixed in with a smooth layout enhances the sports b****** experience tenfold. It does not matter what you are looking for at BetMGM Sportsbook Michigan—you will be able to find it with ease.
오공 슬롯
Zhu Houzhao가 원했던 것은 큰 승리, 비행 팀이 그에게 가져온 큰 승리였습니다.
Euro
에그슬롯
그러나 배는 여전히 남동쪽을 향해 빠르게 달리고 있었다.
Este site é uma referência em termos de segurança e confiabilidade online. A cada clique, minha confiança nele só aumenta. Recomendo a todos!
A cada acesso a este site, sinto-me imediatamente envolvido por uma atmosfera de confiança. Parabéns pela dedicação à segurança dos usuários!
Cada vez que acesso este site, sinto-me acolhido por sua atmosfera de confiança. É reconfortante saber que minhas informações estão em boas mãos. Obrigado pela paz de espírito!
https://thepetmaven.ca/batman138
Great article, totally what I wanted to find.
Terrific! But, seriously, why the abundance of English comments and emojis? 😁
북 오브 데드
“오.” Hongzhi 황제는 “읽고 들어라. “라고 고개를 끄덕였다.
Admirable! But, seriously, what’s with all the English comments and emojis? 😄
Admirable! But, seriously, what’s with all the English comments and emojis? 😄
贏家娛樂城DACRD
슬롯 게임 사이트
하지만 가짜가 아니니까 이 어린 왕자 푸주가 진짜야?
在现代,在线赌场提供了多种便捷的存款和取款方式。对于较大金额的存款,您可以选择中国信托、台中银行、合作金库、台新银行、国泰银行或中华邮政。这些银行提供的服务覆盖金额范围从$1000到$10万,确保您的资金可以安全高效地转入赌场账户。
如果您需要进行较小金额的存款,可以选择通过便利店充值。7-11、全家、莱尔富和OK超商都提供这种服务,适用于金额范围在$1000到$2万之间的充值。通过这些便利店,您可以轻松快捷地完成资金转账,无需担心银行的营业时间或复杂的操作流程。
在进行娱乐场提款时,您可以选择通过各大银行转账或ATM转账。这些方法不仅安全可靠,而且非常方便,适合各种提款需求。最低提款金额为$1000,而上限则没有限制,确保您可以灵活地管理您的资金。
在选择在线赌场时,玩家评价和推荐也是非常重要的。许多IG网红和部落客,如丽莎、穎柔、猫少女日记-Kitty等,都对一些知名的娱乐场给予了高度评价。这些推荐不仅帮助您找到可靠的娱乐场所,还能确保您在游戏中享受到最佳的用户体验。
总体来说,在线赌场通过提供多样化的存款和取款方式,以及得到广泛认可的服务质量,正在不断吸引更多的玩家。无论您选择通过银行还是便利店进行充值,都能体验到快速便捷的操作。同时,通过查看玩家的真实评价和推荐,您也能更有信心地选择合适的娱乐场,享受安全、公正的游戏环境。
피망 슬롯
게다가 Xiao Jing이 공장 경비를 통제할 수 없다면 누가 적합할까요?
에그벳 스포츠
그렇다면 그가 준 선물은 지극히 귀한 것임에 틀림없다.
פוקר באינטרנט
הימורי ספורט – הימורים באינטרנט
הימור ספורט נעשו לאחד התחומים הצומחים ביותר בהימורים באינטרנט. שחקנים יכולים להתערב על תוצאות של אירועים ספורטיביים נפוצים כמו כדור רגל, כדור סל, טניס ועוד. האופציות להימור הן מרובות, כולל תוצאתו המשחק, כמות השערים, כמות הפעמים ועוד. להלן דוגמאות של למשחקי נפוצים שעליהם ניתן להתערב:
כדורגל: ליגת אלופות, מונדיאל, ליגות אזוריות
כדור סל: NBA, יורוליג, טורנירים בינלאומיים
טניס: טורניר ווימבלדון, אליפות ארה”ב הפתוחה, רולאן גארוס
פוקר ברשת – הימורים ברשת
פוקר ברשת הוא אחד ממשחקי ההימורים הפופולריים ביותר כיום. משתתפים יכולים להתמודד מול יריבים מכל רחבי תבל בסוגי וריאציות של המשחק , למשל Texas Hold’em, Omaha, Stud ועוד. אפשר למצוא תחרויות ומשחקי קש במבחר דרגות ואפשרויות הימור מגוונות. אתרי הפוקר המובילים מציעים:
מבחר רב של גרסאות פוקר
טורנירים שבועיות וחודשיים עם פרסים כספיים גבוהים
שולחנות המשחק למשחק מהיר ולטווח ארוך
תוכניות נאמנות ומועדוני VIP עם הטבות בלעדיות
בטיחות ואבטחה והוגנות
בעת בוחרים בפלטפורמה להימורים, חשוב לבחור גם אתרים מורשים ומפוקחים המציעים סביבת למשחק בטוחה והוגנת. אתרים אלו עושים שימוש בטכנולוגיות אבטחה מתקדמת להגנה על נתונים אישיים ופיננסיים, וגם בתוכנות גנרטור מספרים רנדומליים (RNG) כדי להבטיח הגינות במשחקים במשחקי ההימורים.
מעבר לכך, חשוב לשחק בצורה אחראי תוך כדי הגדרת מגבלות הימור אישיות. רוב האתרים מאפשרים גם לשחקנים לקבוע מגבלות הפסד ופעילות, וגם לנצל כלים למניעת התמכרות. שחקו בחכמה ואל תרדפו גם אחרי הפסד.
המדריך המלא למשחקי קזינו ברשת, משחקי ספורט ופוקר באינטרנט באינטרנט
הימורים ברשת מציעים גם עולם שלם של הזדמנויות מלהיבות למשתתפים, החל מקזינו באינטרנט וכל משחקי ספורט ופוקר באינטרנט. בעת בחירת בפלטפורמת הימורים, חשוב לבחור גם אתרי הימורים המפוקחים המציעים גם סביבה משחק מאובטחת והוגנת. זכרו גם לשחק תמיד בצורה אחראית תמיד ואחראי – משחקי ההימורים באינטרנט נועדו להיות מבדרים ולא לגרום לבעיות פיננסיות או גם חברתיות.
마종 웨이즈 2
형을 두고 떠났지만 황금산은 아직 멀었다.
슬롯 무료 사이트
Liu Jian의 얼굴은 더욱 충혈되었고 얼굴은 귀 밑까지 붉어졌습니다.
bocor88
bocor88
황제 슬롯
펀치와 발차기 후 고통이 그의 심장을 찔렀고 Zhang Yanling은 머리를 껴안고 통곡했습니다!
플레이 슬롯
이때 황실 의사가 급히 와서 Ouyang Zhi의 출혈을 막았습니다.
하이브 슬롯
그 남자는 똑바로 서서 “당신이 스페인어를 할 수 있다고 들었습니까?”라고 말했습니다.
91club06.com
Коммерческий секс в городе Москве существует как сложной и сложноустроенной проблемой. Невзирая на данная деятельность противозаконна юридически, эта деятельность является существенным нелегальной областью.
Исторические аспекты
В советского времени периоды секс-работа имела место в тени. По окончании Союза, в обстановке рыночной неопределенности, проституция стала быть более заметной.
Нынешняя Ситуация
Сейчас коммерческий секс в городе Москве включает многочисленные формы, от престижных эскорт-услуг и до уличной коммерческого секса. Престижные сервисы обычно предлагаются через интернет, а публичная коммерческий секс концентрируется в определённых районах города.
Социальные и экономические факторы
Большинство представительницы слабого пола занимаются в эту деятельность по причине материальных проблем. Интимные услуги может быть интересной из-за возможности немедленного дохода, но она влечет за собой рисками для здоровья и личной безопасности.
Правовые Вопросы
Секс-работа в РФ не законна, и за её занятие установлены серьёзные наказания. Секс-работниц зачастую привлекают к ответственности к административной и правовой вине.
Таким образом, не обращая внимания на запреты, секс-работа существует как аспектом нелегальной экономики российской столицы с существенными социальными и юридическими последствиями.
эротический массаж для девушек
무료 슬롯 게임
그는 빨리 앞으로 걸어 Fang Jifan 앞에 도착한 다음 Fang Jifan을 응시했습니다.
IT outsourcing
How Might A Outsourcing Organization Achieve At Least One Transaction From Ten Appointments?
Outsourcing firms can enhance their deal success rates by concentrating on a several crucial approaches:
Understanding Customer Needs
Before appointments, conducting comprehensive investigation on potential clients’ businesses, challenges, and particular requirements is essential. This planning allows outsourcing companies to adapt their services, thereby making them more enticing and pertinent to the client.
Transparent Value Statement
Presenting a clear, compelling value proposition is crucial. Outsourcing firms should emphasize the ways in which their services offer cost reductions, enhanced efficiency, and expert knowledge. Explicitly showcasing these benefits assists customers comprehend the tangible advantage they would receive.
Creating Trust
Confidence is a foundation of fruitful transactions. BPO firms can establish trust by highlighting their history with case histories, endorsements, and sector credentials. Verified success stories and reviews from happy customers can notably strengthen credibility.
Efficient Follow Through
Steady follow through following appointments is crucial to retaining interaction. Tailored follow through communications that recap important discussion points and address any queries enable retain client engagement. Utilizing CRM tools ensures that no prospect is neglected.
Non-Standard Lead Generation Strategy
Innovative strategies like content promotion can position BPO companies as market leaders, pulling in prospective clients. Connecting at market events and utilizing online platforms like LinkedIn can extend influence and build important connections.
Benefits of Contracting Out IT Support
Outsourcing tech support to a outsourcing firm might lower expenses and offer availability of a skilled labor force. This permits companies to prioritize core activities while ensuring excellent service for their clients.
Application Development Best Practices
Adopting agile methods in application development ensures faster delivery and step-by-step advancement. Multidisciplinary teams improve teamwork, and ongoing input helps detect and resolve issues at an early stage.
Significance of Individual Employee Brands
The individual brands of staff improve a outsourcing company’s reputation. Recognized sector experts within the company pull in customer confidence and add to a good standing, helping with both new client engagement and keeping talent.
International Impact
These strategies help BPO companies by promoting productivity, enhancing client interactions, and encouraging How Could A Outsourcing Firm Secure At Least One Sale From Ten Sessions?
BPO firms could boost their sales conversion rates by concentrating on a several key approaches:
Comprehending Client Needs
Ahead of appointments, carrying out thorough analysis on prospective customers’ businesses, issues, and unique demands is vital. This planning permits outsourcing firms to customize their offerings, rendering them more appealing and relevant to the client.
Transparent Value Statement
Offering a coherent, compelling value statement is vital. Outsourcing firms should highlight the ways in which their solutions provide cost reductions, increased effectiveness, and expert expertise. Explicitly showcasing these benefits enables customers grasp the tangible value they would gain.
Creating Reliability
Trust is a key element of effective transactions. Outsourcing firms could establish confidence by showcasing their history with case histories, reviews, and market credentials. Demonstrated success stories and endorsements from satisfied customers might notably strengthen credibility.
Productive Follow Through
Consistent follow-up after meetings is key to retaining interaction. Personalized post-meeting communication emails that repeat key discussion points and answer any concerns help retain client engagement. Using customer relationship management tools ensures that no prospect is forgotten.
Non-Standard Lead Generation Approach
Creative strategies like content strategies can position outsourcing firms as industry leaders, pulling in potential clients. Networking at market events and using social networks like business social media might increase reach and build significant connections.
Benefits of Contracting Out Tech Support
Outsourcing tech support to a outsourcing company might cut expenses and give entry to a skilled workforce. This permits businesses to focus on core activities while guaranteeing excellent support for their users.
Application Development Best Practices
Embracing agile methods in software development ensures more rapid completion and step-by-step advancement. Cross-functional units improve cooperation, and ongoing feedback aids spot and resolve issues early on.
Relevance of Individual Employee Brands
The personal brands of workers boost a BPO firm’s credibility. Recognized sector experts within the firm pull in client credibility and contribute to a good reputation, helping with both new client engagement and employee retention.
Worldwide Effect
These methods help outsourcing companies by promoting efficiency, enhancing client interactions, and fostering
슬롯 나라 무료
밖에는 여전히 문제가 있기 때문에 상황이 더 심각해질지 하나님은 아십니다.
꽁포 사이트
눈에서 눈물을 닦고 가마에서 내려 큰 집을 바라보니…
리액툰즈
Hongzhi 황제는 Fang Jifan을 바라보고 고개를 끄덕이며 “맞습니다. “라고 말했습니다.
산타스 스택
“예, 전하, 그는 세상 밖의 전문가입니다.” Fang Jifan이 확신을 가지고 말했습니다.
슬롯 카지노
Chenla 왕은 항상 신음하며 얼굴을 가리고 땅에 쓰러졌습니다.
Terima kasih atas posting yang luar biasa! 🌈 Berapa penghasilan seorang penulis di sini? Saya ingin bergabung!
Sungguh mengagumkan! 🚀 Berapa bayaran yang bisa didapat oleh penulis di sini? Saya ingin bergabung!
sm 슬롯
이것은 꽃 자체만큼이나 고귀한 매우 아름다운 이름입니다.이것은 새로운 디자인입니다. 패키지를 보낸 사람은…여전히 Lord Hou입니다…
I’m extremely pleased to discover this website. I wanted to thank you for ones time just for this fantastic read!
My website: порно римминг
台灣線上娛樂城
Eddie Callaham
In total, there are around 140 different slots on the menu. All the games at Parx are provided by the igaming software provider GAN, who have signed an e************* with the c***** to power the online c*****. Parx also includes games from NetEnt and Evolution, who have a third-party integration agreement with GAN. One more thing that has to be mentioned about the Parx C***** Sportsbook: The LED lighting on the ceiling can be adjusted based on whatever local team is playing that day. So if it’s an Eagles game, the sportsbook gets a green theme. If it’s a 76ers game, it turns to red, white, and blue. If it’s the Phillies…you get the idea. We told you no detail was spared when they made this sportsbook and we weren’t kidding. Join Our Mailing List 21+ G******* problem? Call 1-800-Gambler. If you or someone you know has a g******* problem, crisis counseling and referral services can be accessed by calling 1-800-GAMBLER (1-800-426-2537) (IL). G******* problem? Call 1-800-GAMBLER (IN MI NJ PA WV WY), 1-800-522-4700 (CO NH), 1-800-BETS OFF (IA), 1-888-532-3500 (VA), 1-800-NEXT STEP (AZ), call text TN REDLINE 1-800-889-9789 (TN), or 888-789-7777 visit ccpg.org chat (CT). 21+ (18+ NH WY). AZ CO CT IL IN IA MI NH NJ PA TN VA WV WY only. Deposit bonus requires 25x play-thru. Bonus issued as site credits. Eligibility restrictions apply. See draftkings sportsbook for full t*******************.
https://dominickjtqi295163.rimmablog.com/27478730/who-won-the-wsop-main-event-2024
N*****************. Offer applies to Grosvenor Sports bets only. Max stake £20. Bets made with Odds Boost Token. Neteller & Skrill deposits excluded. T&Cs apply. When using no deposit free spins, much like regular free spins bonuses, the c***** will likely pick the eligible slot for you. This means that, in most cases, you can’t use your free spins on whatever slot you want. Copyright © 2024 PTCC Lakeside. Powered by PTCC Lakeside. N*****************. Offer applies to Grosvenor Sports bets only. Max stake £20. Bets made with Odds Boost Token. Neteller & Skrill deposits excluded. T&Cs apply. Get 10 Free Spins for Registration. Bonus rounds can be used on “Book of Dead” game. Wagering is x25 the bonus amount. Cash out is limited to €$200. Play responsibly. C***** general T******************* apply.
ragnarok for android
Punjab struggled throughout their innings. They just scored 38 runs in the powerplay, the fourth-lowest powerplay score in the IPL 2024. Rajasthan bowlers chipped in with wickets at regular intervals to keep PBKS under control. KKR won by 8 Wickets 14:26 mins Mitchell Starc hopes to be retained by KKR ahead of IPL 2025 mega-auction Rohit Sharma will be keen to continue his good form when Mumbai Indians take on Sunrisers Hyderabad at the Wankhede Stadium on Monday (May 6). Simon Helmot backs Travis Head and Abhishek Sharma to come good in next match Mumbai Indians in IPL 2024: What went wrong for MI in IPL? | HT Cricket Most Runs In T20 World Cup 2024 1st Innings Who won yesterday’s IPL final match? Kolkata Knight Riders (KKR) emerged as champions once again at the MA Chidambaram Stadium in Chennai on Friday, May 24 thanks to their 8-wicket victory over Pat Cummins-led Sunrisers Hyderabad. (As It Happened) | Report)
https://zionufnt874937.blogsuperapp.com/27927855/now-liverpool-transfer-news
81 minutes: Manchester City 2-1 Manchester United YOU COULDN’T WRITE IT рџ¤ЇAcademy graduate, Kobbie Mainoo scores in the #EmiratesFACup Final for @ManUtd рџ± pic.twitter d68cAKvaE8 This would be Man Utd’s 13th league defeat of the season. The last time they suffered as many was in 1988-89, a bleak campaign in which attendances at Old Trafford dropped as low as 23,000. Erik Ten Hag led Manchester United to a stunning FA Cup victory over rivals Manchester City, then warned the club’s hierarchy: ‘If you don’t want me, I’ll go and win elsewhere!’ Chelsea breathed life into their quest to qualify for Europe after defeating Manchester United 4-3 in an instant Premier League classic. Antony feels he is in a good moment in terms of performances, as he looks forward to another Wembley trip…
ragnarok online server
카지노 슬롯
그는 Jinyiwei에서 중요하지 않은 작은 깃발 장교 일뿐입니다.
슬롯 킹
그러나 이후 세대에서는 작업이 거의 없습니다. 거의 할례와 같습니다.
온라인 슬롯 게임 추천
이 사람은 수다를 떨고 있습니다. 그는 더 이상 참을 수 없습니다.
Marvelous article! ✨ The depth of information is commendable. Consider adding more visuals in your future articles for a more immersive reader experience. 📷
Excellent piece! 👏 The information is presented in a compelling manner. Adding more visuals in your future articles could make them even more enjoyable for readers. 📷
강원 랜드 슬롯 머신 종류
“정말요?” 리동양은 관심을 갖고 개인적으로 그에게 다가갔고, 과연…
슬롯 나라 에그 벳
얼마 지나지 않아 Zhu Zaimo는 궁전에 들어가 큰 경례를하며 “아버지를 보았습니다. “라고 말했습니다.
돌리고 슬롯
아니나 다를까, 좋은 형제는 헛되지 않으며, 중요한 순간에 항상 나타날 수 있습니다.
coindarwin price analysis
The Untold Account Behind Solana Founder Toly Yakovenko’s Achievement
Subsequent to A Pair of Cups of Java plus a Brew
Toly Yakovenko, the mastermind behind Solana, began his path with a simple habit – two coffees and a brew. Little did he know, these moments would ignite the gears of his journey. Today, Solana remains as a powerful contender in the cryptocurrency realm, with a worth in billions.
First Sales of Ethereum ETF
The Ethereum ETF lately launched with an impressive trade volume. This significant event saw multiple spot Ethereum ETFs from different issuers begin trading in the U.S., introducing unprecedented activity into the generally calm ETF trading market.
SEC Approved Ethereum ETF
The U.S. SEC has sanctioned the Ethereum exchange-traded fund for being listed. As a digital asset featuring smart contracts, Ethereum is anticipated to significantly impact the digital currency industry due to this approval.
Trump’s Bitcoin Tactics
As the election approaches, Trump portrays himself as the ‘Crypto President,’ continually showcasing his backing of the blockchain space to garner votes. His approach differs from Biden’s method, seeking to capture the focus of the blockchain community.
Elon Musk’s Crypto Moves
Elon Musk, a famous figure in the blockchain world and a supporter of the Trump camp, shook things up once more, promoting a meme coin connected to his actions. His involvement continues to influence market trends.
Binance Developments
Binance’s unit, BAM, has been allowed to channel customer funds in U.S. Treasuries. Furthermore, Binance marked its seventh year, emphasizing its progress and achieving several compliance licenses. Simultaneously, the company also made plans to take off several notable cryptocurrency trading pairs, affecting different market players.
AI’s Impact on the Economy
Goldman Sachs’ leading stock analyst recently observed that artificial intelligence won’t trigger an economic transformation
An fascinating discussion may be worth comment I do think that you need to write regarding this topic, it might become a taboo subject but typically individuals are not enough to communicate in on such topics To a higher Cheers
Discover exclusive Marc Jacobs offers at the marc jacobs outlet.