Info-Tech Research Group Releases Blueprint for Security and Privacy in an Exponential IT Era
Info-Tech’s latest research blueprint navigates the complex landscape of AI-driven security threats and ethical considerations. The resource offers a strategic approach for security leaders to safeguard their organizations in the exponential IT era.
Due to advancements in emerging technologies like AI and quantum computing, data breaches and cyber threats are becoming increasingly sophisticated. With this development, the traditional paradigms of IT security and privacy are undergoing a radical transformation. To guide security leaders through the new challenges they face when working to protect their organizations from attacks, Info-Tech Research Group, a global leader in IT research and advisory, has introduced its latest blueprint, Exponential IT for Security and Privacy. The new resource provides a comprehensive roadmap to help navigate the new realities of information security.
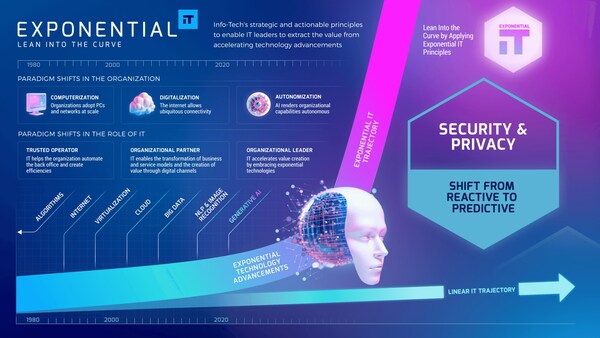
Info-Tech’s Exponential IT framework is designed to guide technology leaders in elevating their maturity and value-creation capabilities. The framework aims to bridge the gap between the exponential progression of technological change and the linear progression of IT’s ability to successfully manage that change.
Recommended AI News: Variational AI Announces Generative AI Project With Merck
“Today, information security departments are being challenged on many fronts. An upswing in credential and identity compromise is leading to increasing instances of ransomware attacks on enterprises,” says Kate Wood, research practice lead at Info-Tech Research Group. “Security leaders are looking to implement zero-trust architectures, increase automation, and govern their data, all to protect their assets, maintain their stakeholder privacy, and remain compliant. And all the while, security practitioners are burning out and leaving and are increasingly expensive to retain and rehire.”
Info-Tech’s blueprint outlines a future where autonomous security operation centers (SOCs) become a reality, offering unparalleled efficiency in threat detection and response. However, it is also cautioned that this automation brings new challenges, particularly in ensuring continuous ethical assurance and responsible private data usage. The research explores how zero-trust behavior, once a technical concept, now permeates everyday interactions, requiring a comprehensive shift in organizational conduct to ensure security and trust at every level.
“Exponential technologies will be both a bane and a boon to information security,” says Fred Chagnon, principal research director at Info-Tech Research Group. “Combine the deeper understanding of assets and infrastructure with a learned sense of pressures, threats, and posture, and AI can make autonomous tactical decisions, completely revolutionizing security operations.”
Recommended AI News: Intel and UMC Announce New Foundry Collaboration
The newly published resource emphasizes that the future of security and privacy in IT is not just about technological advancements but also about adapting to a new culture of security awareness and ethical responsibility. This shift calls for a holistic approach where technology, people, and processes are aligned to create a secure and trustworthy digital environment.
“The more we use AI for autonomous tactical decision-making, the more this pushes the envelope for the potential misuse of private data and the question of ethics in AI,” explains Wood. “Mitigating these risks and alleviating the associated concerns is the CISO’s raison d’être in an Exponential IT world.”
The firm’s blueprint outlines the following key actions, which security leaders can implement to proactively address the evolving landscape of threats while upholding the highest standards of privacy and ethical conduct:
- Assume They Are More Sophisticated: Defend Against AI-Enabled Attacks – Security teams must adapt to the reality that threat actors are utilizing AI to enhance their attack capabilities. These teams must anticipate the rise of polymorphic APTs and zero-day threats, understanding that attackers operate without the constraints of laws and regulations.
- Go Back to the Drawing Board: Mitigate Rampant Privacy Risks – As organizations rapidly adopt AI-enabled functions, IT departments must detect and mitigate unintended security and privacy impacts. This process involves managing the risks associated with the speed, scope, and volume of data harvested, particularly in terms of unintentional PII exposure and compliance with privacy regulations.
- Overcome Hesitation: Enable Autonomous Decision-Making – IT leaders should enable AI systems to make informed decisions autonomously in areas such as prioritizing audit recommendations, risk mitigation, and control implementation efforts. This approach requires aligning AI decision-making processes with the organization’s objectives and risk appetite, ensuring that AI-driven actions are both effective and aligned with business goals.
“Threat actors will soon be engaging with employees, blending generative AI with deepfake video and voice synthesis to create a social engineering attack landscape that will shake our understanding of trust,” says Chagnon. “Security leaders have to wield these exponential technologies on defense if they’re going to have any chance at protecting their enterprises from the AI-enabled threats of the future.”
Info-Tech’s research underscores the transformative impact of exponential technology advancements on the IT security landscape. By adopting the strategic actions outlined in the blueprint, security leaders can steer their organizations toward a future where security and privacy are not just about defense but also about ethical responsibility and proactive risk management. This approach not only enhances the security posture but also aligns security strategies with broader business objectives, positioning security as a crucial contributor to organizational resilience and success in a rapidly evolving digital world.
Recommended AI News: Google Cloud and Hugging Face Announce Strategic Partnership
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]

Comments are closed.