Is AI-Based Vulnerability Management Really that Efficient?
Vulnerabilities are one of the top priorities for security professionals. Security teams find themselves in a race to detect, prioritize, and fix vulnerabilities before attackers can find them and exploit them. The traditional vulnerability management tools and practices are ineffective against the increasing number of vulnerabilities and the shortage of security staff.
ome to help. Most solutions claim to give full coverage over the surface attack. Let’s review how to leverage AI-based vulnerability management tools to maximize their effectiveness.
Why do you need to include AI in vulnerability management?
Most security teams conduct vulnerability assessments, and it was a tested method for finding vulnerabilities for the last years. Vulnerability assessments check the environment for outdated or otherwise non-patched software and other openings for exposure.
Traditionally, security teams use the help of vulnerability assessment tools, but the legacy solutions are not very effective with distributed environments, especially hybrid environments, with mobile and IoT devices. Traditional vulnerability tools also overlook sophisticated attack vectors, such as credential issues or phishing.
Legacy solutions don’t prioritize the vulnerabilities, leaving security teams to handle multiple vulnerabilities lists without context. It falls into the hands of the security professionals to determine the severity of the vulnerabilities.
Artificial intelligence, specifically machine learning, analyzes the data in real-time, prioritizing the vulnerabilities according to the risk level. AI-powered solutions include threat and vulnerability management features that can scan and predict the risk across thousands of attack vectors and threats.
How critical is it to take care of vulnerabilities?
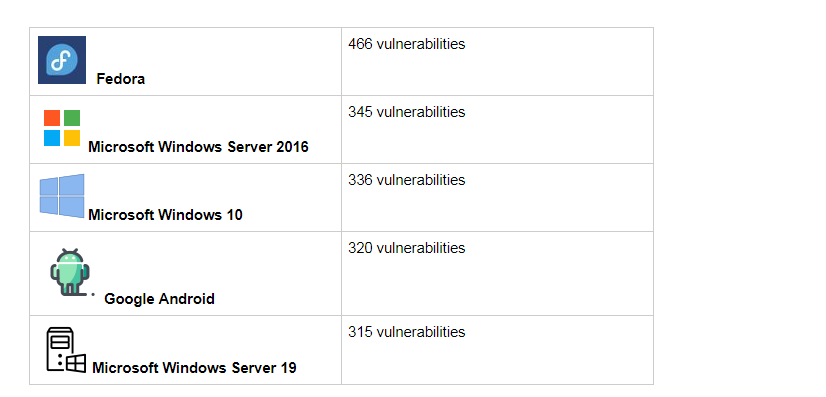
Vulnerabilities statistics highlights:
- According to the Common Vulnerabilities and Exploits (CVE), there have been over 12 thousand security vulnerabilities so far in 2021.
- The average severity of the vulnerability is a 7 in 10, the same as in 2020.
- The top 5 products with the most vulnerabilities reported in 2021 are:
 Use cases of AI techniques in Vulnerability Management
Use cases of AI techniques in Vulnerability Management
So, how can you use AI techniques for vulnerability management? Machine learning is used in cybersecurity to automate threat detection and analysis.
Improved threat detection capabilities
Tools like user and event behavior analytics (UEBA) uses machine learning to analyze the user behavior to detect any anomaly that may indicate an unknown compromise. AI technologies are especially useful to detect which assets are critical for the company and should be protected more. The system can compare different assets, establishing a normal baseline and flagging remarkable assets.
Reducing false positives in vulnerability detection
Legacy vulnerability detection usually errs on the side of caution and the process often results in a lot of false positives. Security teams employ AI technology to detect the probability of the identified vulnerability being legitimate. The systems take into account which detection mechanism flagged the vulnerability and other factors.
Context-based vulnerability risk scoring
AI techniques provide the context-based prioritization of vulnerabilities that security teams sorely need. These techniques enable the development of a more accurate risk score, taking into account an in-depth understanding of the context of an asset.
For instance, it may see that an asset potentially at risk is, in reality, isolated from the network.
Using sentiment analysis to detect vulnerability exploitation trends
Applying the same techniques used in sentiment analysis can prove useful to detect vulnerability trends. AI tools can collect data from cybersecurity chat rooms and media sites, analyze it, and detect trends in vulnerabilities to be exploited. AI techniques such as Neural Networks and Natural Language Processing make it possible to identify positive/negative sentiments and interpret the meaning of the text to evaluate risk.
Improving remediation
Many organizations face the challenge of detecting more vulnerabilities than they can remediate. As AI technologies provide a context-driven list of vulnerabilities, organizations can use this information to develop remediation plan recommendations. AI gives security teams insights on risk and vulnerability scores that improve remediation.
There’s More to Vulnerability Management Than the Right Tools
However useful AI can be for vulnerability management, it is a tool. Artificial Intelligence tools require a well-designed vulnerability management strategy and skilled security teams to ensure a strong coverage and remediation of vulnerabilities.
AI is not exempt from risks itself since cyber attackers can use machine learning technology to manipulate the security firm of AI algorithms. In addition, hackers can use the same techniques to create malicious software that imitates legitimate AI algorithms.
According to research by IBM, there are four common methods attackers can use against machine learning tools:
- Poisoning: this method adds a backdoor to the data used for training the machine learning model.
- Extraction: here attackers steal the machine learning proprietary model.
- Evasion: attackers here gain access to the model, modifying the inputs and influence the results of the model.
Final Thoughts: How can You Achieve a Solid Vulnerability Management Strategy?
To achieve a comprehensive vulnerability management program, you need to combine several factors.
First, a knowledge base, including a list of assets that rank by critical importance. Second, this inventory should be transformed into a map of vulnerabilities that can work as a basis for the vulnerability strategy.
The right AI tools help to make the process of identifying, prioritizing, and remediating vulnerabilities much easier and effective. This, together with a well-designed plan, contribute to a strong security posture.

Comments are closed.