Cyberattacks Strike More Than 40% Of Manufacturers
- Onclave Networks Highly Recommends Manufacturers Adopt a Zero Trust Framework to Protect Their Network Enterprise and Customers.
In response to the 62% global increase in ransomware since 2019 and over 40% of manufacturing firms suffering a cyberattacks last year, cybersecurity leader Onclave Networks, Inc. recommends manufacturers adopt Zero Trust Architecture and security guidelines as supported by the U.S. National Security Agency (NSA), the Biden Administration executive order 14028 and NIST (National Institute of Standards Technology) SP 800-207 Cybersecurity Framework.
Recommended AI News: REPAY Expands Acumatica Functionality to Offer Accounts Payable Automation
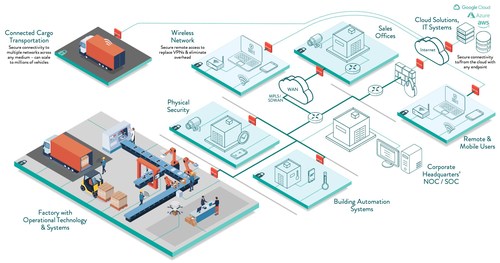
Over the last several years, manufacturing has gone through an Information Technology (IT) and Operational Technology (OT) convergence. The integration is expected to expand more rapidly in the years ahead due to the increased availability of 5G and more sophisticated Industrial Internet of Things (IIoT) devices and systems and Industrial Control Systems (ICS). Onclave warns that as manufacturers modernize their digital operations, they will connect more disparate devices and systems and transmit that data across IT networks, significantly expanding their attack surface and vulnerability to a cyberattack in the process.
“Most of the IT security methods that manufacturers have relied on for years are not designed to identify or protect Operational Technology,” said Don Stroberg, CEO of Onclave Networks. “Manufacturers need to be aware that layering IT solutions on top of one another is not adequate protection for these IoT, IIoT and ICS systems and devices.” Stroberg and Onclave recommend that manufacturers secure their network edge by using the Onclave TrustedPlatform™ to cryptographically separate the OT from the IT network. This approach provides detection, isolation, and containment of threats to the enterprise and eliminates the OT attack surface.
Onclave also cautions manufacturers that the rise in cybersecurity threats is due to both the growth in internet-enabled devices and Operational Technology, as well as to the greater integration between companies and their supply chain partners. As cyberattacks on SolarWinds, Bombardier, Colonial Pipeline, and others have demonstrated, these threats put critical and confidential data at risk, as well as jeopardize operations and production.
“The recent supply chain and critical infrastructure cyberattacks have opened the eyes of a lot of executives and managers who are concerned about their exposure to malware from suppliers as well as whether or not they could unknowingly spread malware across their supply chain,” Stroberg said. “The potential for massive disruption to the business is greater, as is the liability these companies could face in the future – more reason why manufacturers are turning to Zero Trust to better secure their networks.”
Recommended AI News: Actian Launches Next-Generation Zen Embedded Database For Mobile And IoT
Why adopt Zero Trust principles?
The goal of a Zero Trust framework deployed in an enterprise is to verify trust in people, devices, systems, and networks before engaging/interacting with them – and continuously verify that trust to ensure nothing is compromised. It changes the old saying of ‘trust, but verify’ to ‘never trust, and always verify’ and that any request for network access must be continuously authorized.
Onclave’s technology, based on DoD and intelligence community techniques, implements those principles and goes beyond them to what the firm calls Zero Trust + by applying the NIST framework to the entire network and providing a secure foundation for SASE implementations and critical infrastructure protection. Onclave protects networks by creating secure enclaves, eliminating entry points for intrusion, and thereby preventing attacks instead of simply identifying and reporting them.
“Onclave can support manufacturers in protecting their smart factories and supply chain,” Stroberg said. “With our network, we eliminate the attack surface area for Operational Technology, while simplifying management issues and reducing their costs.”
Recommended AI News: TripleLift Names New Leadership to Oversee Technology Organization