Vulcan Cyber Study Reveals IT Leaders Overestimate Vulnerability Management Program Maturity
84% of Security and IT Leaders Feel Their Programs Are Mature, but the Data Reveals Otherwise
Vulcan Cyber, the vulnerability remediation company, announced the results of a research project conducted to better gauge the maturity of enterprise vulnerability management programs. Vulcan Cyber surveyed more than 100 security and IT leaders about the current state of vulnerability management at their companies and compared the results to its vulnerability remediation maturity model which was developed to help companies fix vulnerabilities and reduce business risk. Surprisingly, 84% of respondents felt their programs were mature, but a deeper dive revealed a major disconnect between perception and reality.
Recommended AI News: Intel Promotes Chief Diversity and Inclusion Officer Barbara Whye
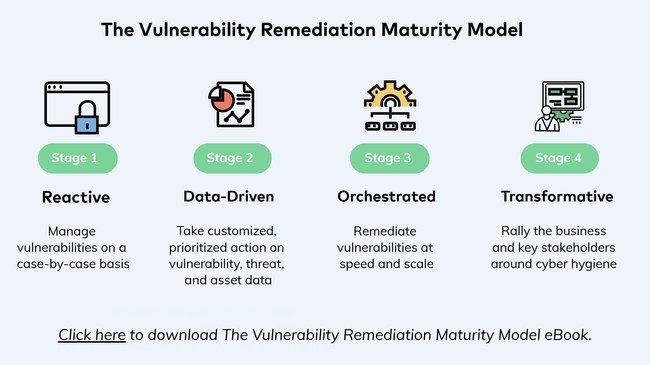
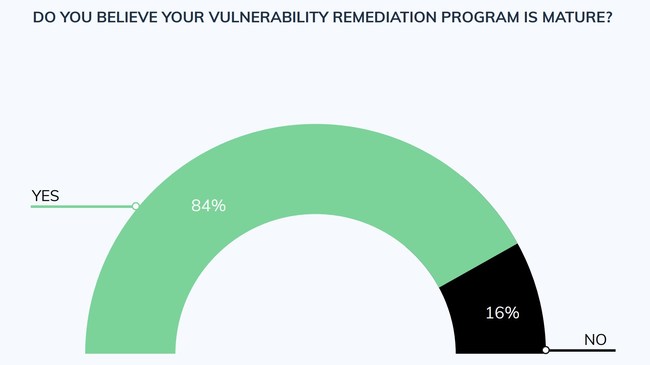
“We already know most enterprise vulnerability management programs are immature. We see it every day in the field. We mapped the survey results against our maturity model to helping IT leaders shift their focus from simply managing vulnerabilities to actual remediation,” said Yaniv Bar-Dayan, Co-founder and CEO of Vulcan Cyber. “What caught us off guard was that the vast majority of respondents felt their programs were already mature. Given the amount of breaches caused by known, unpatched vulnerabilities, we discovered a surprising disconnect that merits a closer look.”
Vulcan Cyber worked with Pulse, tapping into its social research platform of CIOs, CISOs, and other tech leaders, to survey the readiness of enterprise vulnerability management programs. Key findings from the survey of more than 100 security and IT leaders include:
- The most mature element of enterprise vulnerability management programs are vulnerability scanning (72%), followed by the effective use of vulnerability remediation tools (49%) and vulnerability prioritization (44%).
- The three least-mature elements are orchestrated, collaborative remediation (48%), continuous, automated remediation (48%) and business alignment around cyber hygiene objectives (31%).
- 89% of security and IT teams say they spend at least some time collaborating with cross-functional teams to remediate vulnerabilities, with 42 % reporting they spend “a lot” or “too much” (7%) time every week working with other teams. A notable 83% of companies that said they spend too much time collaborating with other teams have 500-1,000 employees.
- Roughly 50% of IT and security teams share responsibility for key remediation functions (identifying vulnerabilities, prioritization, crafting remediation strategies, deploying patches and remedies, etc.), revealing an opportunity to facilitate more effective and efficient collaboration by clearly defining the division of labor.
Recommended AI News: Bidalgo Transforms Ad Creative Production and Analysis With the Launch of Creative Center
These research highlights and more can be found in this Vulcan Cyber whitepaper and infographic.
“Vulnerability scanning and prioritization are essential functions, but they are the bare minimum — not what constitutes a mature program,” Bar-Dayan continues. “In our experience, program bottlenecks are further along in the remediation lifecycle, stemming from inefficient cross-team collaboration. Changing the status quo requires organizations to update and automate their remediation processes. It’s a heavy undertaking, but one that transforms vulnerability management programs into a powerful lever for shrinking security debt and strengthening the company’s security posture.”
Recommended AI News: Faction 2020 VMware Cloud on AWS Market Survey

Comments are closed, but trackbacks and pingbacks are open.