“Evolution of IoT Attacks” Study Exposes the Arms Race Between Cybercriminals and Cybersecurity
Sectigo Chronicles Attacks on Cars, Homes, Infrastructure, Medical, and Other Connected Devices, Leading to an ‘Era of Protection’
The number of devices connected to the internet is expected to reach 50 billion worldwide by the end of 20301, posing dangerous risks to people, businesses, and critical systems. To illustrate the divide between cyberattacks on these devices and business preparedness, Sectigo, a leading provider of automated digital identity management and web security solutions, today released its Evolution of IoT Attacks study.
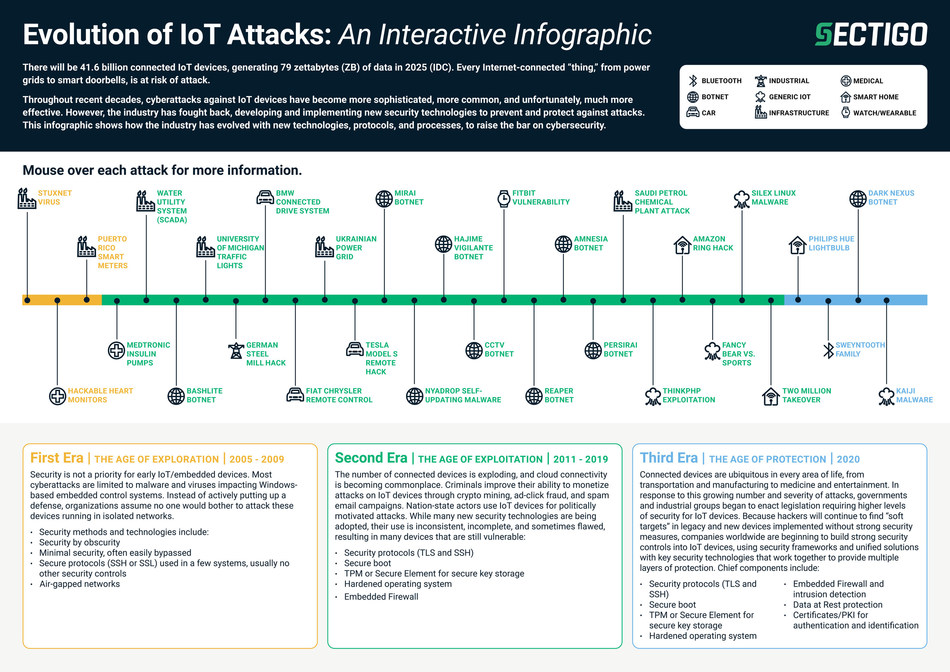
The study report and associated infographic chronicle the progression, variety, and growing sophistication of many of the most infamous vulnerabilities and attacks on connected devices, as well as the emerging defenses used by organizations to fight them.
Recommended AI News: Microsoft Cloud For Healthcare Launched; Takes The Limelight In Fight Against COVID-19
Sectigo has categorized IoT attacks into three eras:
The Era of Exploration
Beginning in 2005, cybercriminals started to explore the potential to cause lasting damage to critical infrastructure, and even life. Security defenses at the time were rudimentary, with organizations unaware of the value the IoT could have for hostile actors.
The Era of Exploitation
Spanning 2011-2018, cybercriminals actively exploited the lucrative and damaging potential of attacking the IoT, thus expanding attacks to more targets with increased severity. However, they found organizations more prepared to withstand the onslaught. White hat hackers exposed potential IoT vulnerabilities to help shore up defenses before attacks occurred in the wild. Meanwhile, as organizations fortified their defenses, cybercriminals found more ways to monetize their attacks through crypto mining, ad-click fraud, ransomware, and spam email campaigns.
The Era of Protection
By 2019, enterprises and other organizations had become increasingly capable of countering these attacks. Just recently, governments have begun enacting regulations to protect IoT assets, and businesses and manufacturers are heeding the warnings. In fact, according to the recent 451 Research Enterprise IoT Budgets and Outlook report2, organizations are investing more than half of their IoT budgets, 51%, to implement security controls in devices, using security frameworks and unified solutions with strong technologies that work together to provide multiple layers of protection.
Recommended AI News: HashCash to Help Banking Sector With Blockchain-Based Digital Identity to Streamline Remote Operations
“As we move into this decade, protecting the vast Internet of Things has never been more critical for our safety and business continuity,” said Alan Grau, VP of IoT/Embedded Solutions at Sectigo. “Cybercriminals are retooling and honing their techniques to keep striking at vulnerable targets. Yes, businesses and governments are making laudable efforts to protect all things connected, but we are only at the beginning of the Era of Protection and should assume that these efforts will be met by hackers doubling down on their efforts.”
IoT security must start on the factory floor with manufacturers and continue throughout the device’s lifecycle. Power grids, highways, data security, and more depend on organizations adopting ever- evolving, cutting-edge security technologies in order to withstand attacks.
For more information about the evolution of IoT attacks, download the full report or related interactive infographic.
1 Strategy Analytics – Global Connected and IoT Device Forecast Update
2 451 Research – Voice of the Enterprise. Internet of Things: Budgets and Outlook 2020
Recommended AI News: 3 Steps To Channel Customer Feedback Into Product Innovation

Comments are closed, but trackbacks and pingbacks are open.