Ionic Security Recognized in Gartner Hype Cycle for Identity and Access Management Technologies
Ionic Security, a leading provider of unified data security and access control solutions, announced that it has been identified as a Sample Vendor in the Gartner Hype Cycle for Identity and Access Management Technologies, 2020 in the Externalized Authorization Management (EAM) category.
The company has also been listed as a Sample Vendor in the Gartner Hype Cycle for Cloud Security, 2020, Hype Cycle for Data Security, 2020 and Hype Cycle for Privacy, 2020.[2][3][4] We believe this recognition is validation of where Ionic sits at the intersection of security and privacy in the digital world.
Recommended AI News: Nuestra Vision Launches on Pluto TV for US Mexicans and Overall Hispanic Market
Gartner states, “Externalized authorization management (EAM) provides runtime controls, including policy management, policy enforcement, and decision modeling for fine-grained authorization to infrastructure, applications, services, transactions and data.”
“Authorization is critical to ensuring least-privilege access to data and services across your infrastructure,” said Bill LeBlanc, CTO of Ionic Security, “Externalizing authorization brings consistency and repeatability to security architectures. Application development teams who can abstract this complexity from their code innovate more quickly and more securely.”
Attribute-based access controls enforced at runtime are hallmarks of EAM solutions, in contrast to the coarser role-based controls native to access management tools. The dynamic granularity enabled by EAM solves a wide variety of security and access control use cases across multiple industries.
Market drivers like evolving policy standards and regulatory compliance mandates are driving urgency around many diverse use cases that companies need to start addressing now. For example, fine-grained controls around country of origin became required with the advent of privacy regulations like the General Data Protection Regulation (GDPR), and the recent invalidation of the EU-US Privacy Shield heralds even greater scrutiny and consequences.
Recommended AI News: SecurityMetrics Summit Brings New Ideas and Innovation to Data Security and Compliance
“The rapid shift to remote workforces has accelerated cloud adoption, but more data in the cloud exposes organizations and their supply chains to regulatory and security risks,” said Eric Hinkle, CEO of Ionic Security. “In our opinion, Gartner’s recognition of externalized authorization management — and Ionic as a Sample Vendor — reinforces our ability to address these risks with centrally managed, programmatically enforced policy.”
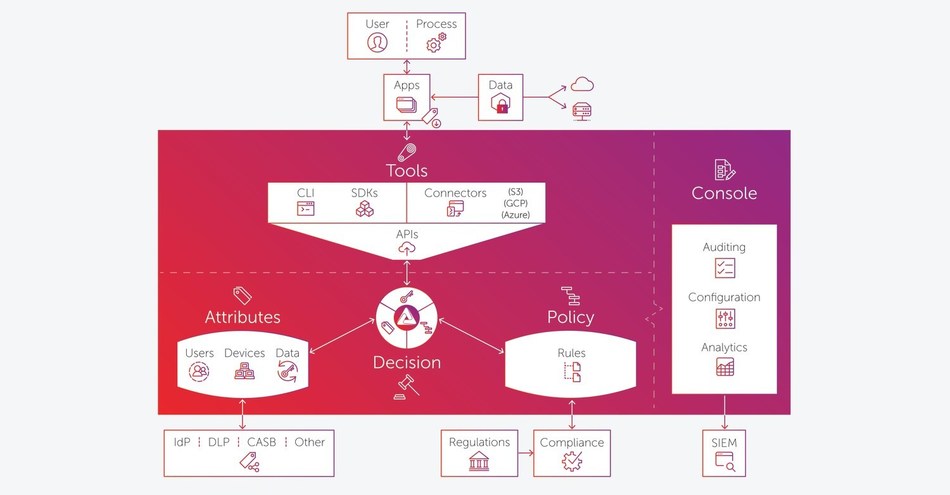
As one of ten Sample Vendors named in the Externalized Authorization Management category in the Hype Cycle for Identity and Access Management Technologies, 2020 report, Ionic brings what we believe is a uniquely data-centric approach with MachinaTM, a dynamic authorization engine coupled with an attribute store that ties together the identities of data, services, and users, plus a scalable key management system protecting data at rest and in transit.
Agnostic to data or resource type, Machina can secure objects at any granularity, in any environment, with full visibility into every transaction to provide proof of compliance. Developers can get started with Machina SDKs and APIs through an easy onboarding process, using just a few lines of code to externalize complex authorization logic. This represents a clear return on investment for application development teams and for security, risk and compliance teams, who can now enforce granular policy consistently from a central management plane.
Recommended AI News: pSemi Expands Portfolio with Two High-Performance Digital Step Attenuators








Comments are closed.